New terms, new reports and a new direction for an emerging risk
By Richard Seiersen: Risk Management Author, Serial CISO, CEO Soluble
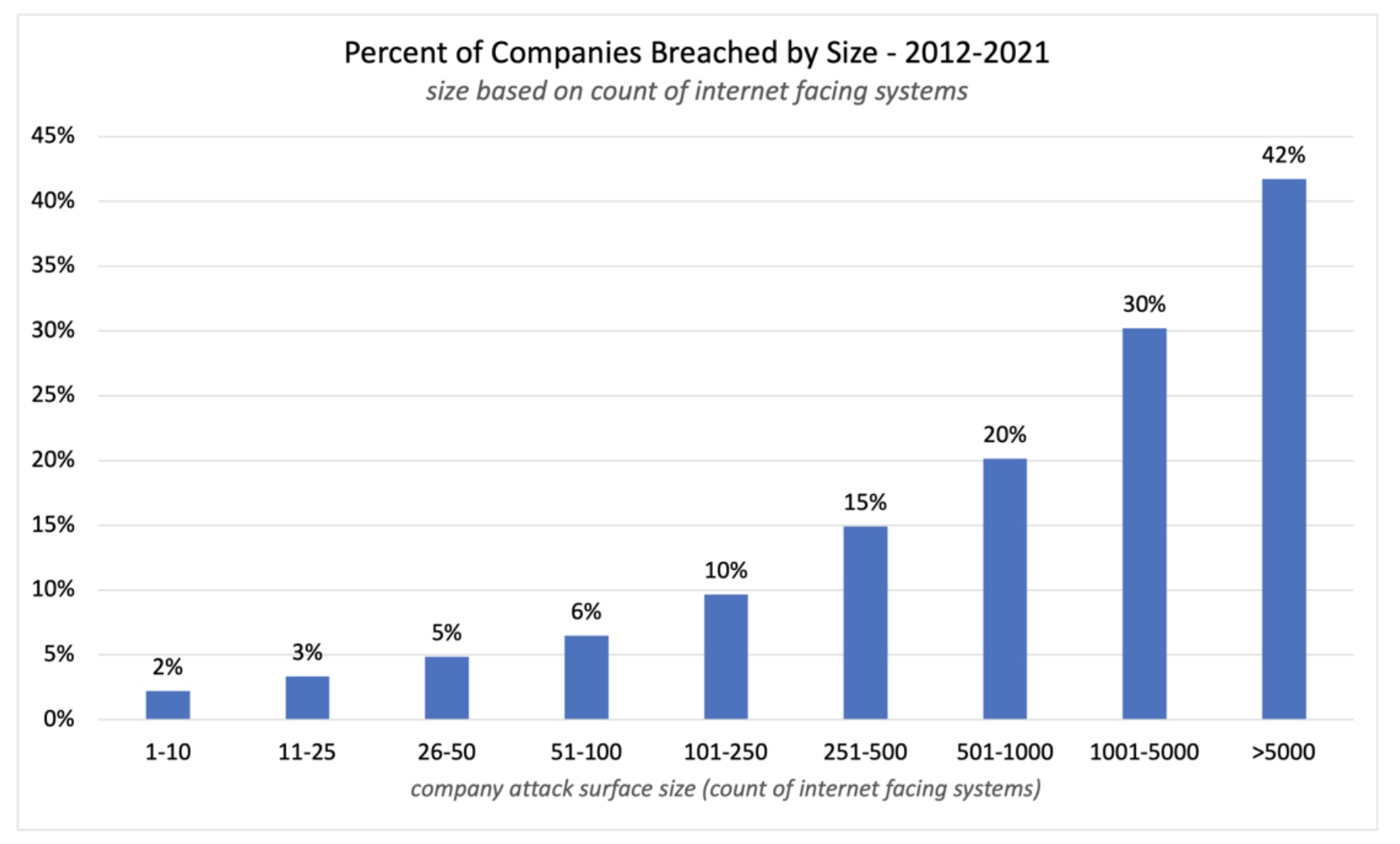
What Is Risk Surface?
It’s big! RiskRecon’s report defines it as follows:
“Risk surface refers to anywhere an organization’s ability to operate, reputation, assets, legal obligations, or regulatory compliance is at risk. The aspects of a firm’s risk exposure that are associated with or observable from the internet can be considered its internet risk surface.”
 Does the description above sound a bit like Enterprise Risk Management (ERM)? It’s different in that ERM is a practice and risk surface is a type of risk. We would practice ERM in relationship to risk surface.
Does the description above sound a bit like Enterprise Risk Management (ERM)? It’s different in that ERM is a practice and risk surface is a type of risk. We would practice ERM in relationship to risk surface.
Then why not just call it “Risk?" I suppose we could, but that defeats the purpose. We want to call out risk surface. It’s a new distinction for an emerging, dynamic and critical risk. We think it needs more focus - a lot more.
Why Risk Surface?
The risk surface report digs into the “why” of risk surface right from the start. It states that the internet facing assets we think we are hosting on premises are most likely hosted elsewhere. On average, 65% of externally facing hosts are hosted by a third party. By extension, what is the likelihood of our third parties using their own third parties?
Consider this, when you sign up for that new SaaS service should you assume they also use third parties? Of course. In fact, I think most of us expect that they are running their instances in one of the various established cloud services. But how sure are you sure they are using the established players?
And are you sure which country those third parties assets reside in? You will find out more about that distribution in the reports, particularly the cloud risk surface report.
Perhaps all of this is old news? Here is another small nugget from the report, did you know that over a quarter of firms use ten or more hosting services and many well over 100! This is just a small view into the data from the reports and what we see as a new reality. It's a mass migration of compute responsibilities outward with an increase in complexity for data controllers.
And I don’t want to steal to much thunder from the risk surface reports (there are two reports right now and expect more to come) but you should read them with the thought, “Do I really know where my data is and are we being consciously competent in how its getting exposed?”
Managing Risk Surface
I suspect many reading this will think, “it’s impossible for me to keep up with all of this! My third parties are certainly sharing data with third parties ad nauseam!” Yes, it would be pretty hard to have perfect visibility. We have a hard enough time knowing what’s going with the stuff we own on premise!
But, this is “risk management” after all. We are trying to move the needle when it comes to reducing probable future loss. Our goal is better, not perfection, in the face of uncertainty.
The first step is increasing awareness of the third parties we have. And having that, starting to get visibility into their posture based on what they expose. What can we tell about the systems they are exposing? Do they manage their systems well based on the empirical data we have on hand? This of course presupposes you are using a service like RiskRecon to pull this data in and measuring exposure and related risks over time.
How about your capabilities for managing third party risk, are you moving the needle? Meaning, how are you doing in managing and measuring third party risk?
- Are you getting faster in risk based decision making when it comes to where your data will go?
- Are you getting faster at burning down the toxic risk that was accepted in the past?
- Are you getting better at identifying who your top “data partners” are or third party “crown jewels”?
- How about cyber insurance? Do you need to make any changes based on the volumes of data you are sending outward? Is cybersecurity insurance even part of the discussion when it comes to third party risk management?
Next Steps
Much of the third party risk focus has been outward. What if we turn that focus inward? Are you able to tell when new third party services are being spun up in your environment? For example, what new microservices have been deployed in the last N days that shovel data to and from third parties? If the majority of your digital risk (data) is moving to third parties shouldn’t we have visibility into that movement?
So the question is, should you have visibility in terms of the third party service development similar to how devops has visibility into operations and development? For example, has anything changed in terms of ingress and egress services in relationship to your third party supporting “crown jewels”? How about the security posture of those services? Are they covered by all of your defense in depth controls? That certainly seems in scope, at least from a governance perspective, for a third party risk management capability concerned with risk surface.
This is an area I will likely write more about as it relates in part to my new book and general interests. And expect a number of articles discussing risk surface and broader risk management topics for the modern enterprise.