During a recent webcast with Kelly White, the founder of RiskRecon MasterCard company, and Jake Bernardes the acting CISO from Whistic discuss trends in cyber risk and how you can maximize your investment in vendor risk management technology to keep your company safe and secure from third-party threats. In this blog, they discuss the idea of cybersecurity deficit, what it is, and how to deal with firms in your vendor ecosystem who have a deficit.
Kelly White: There may not be a great common understanding of the definition of cybersecurity deficit. When you look at common practices like you would see in the NIST cybersecurity framework, that is commonly and broadly accepted as necessary for protecting businesses that are operating digitally, it's particularly important for SaaS where your business is the collection, processing, and dissemination of information, but other businesses as well. As we look at the correlation and understanding of, for example, things like ransomware attacks, it's the exploitation of basic security practices where companies have a deficit. In vulnerability management, it's in not exposing unsafe network services. It's defending against email-borne phishing, social engineering, malware attacks, etc.
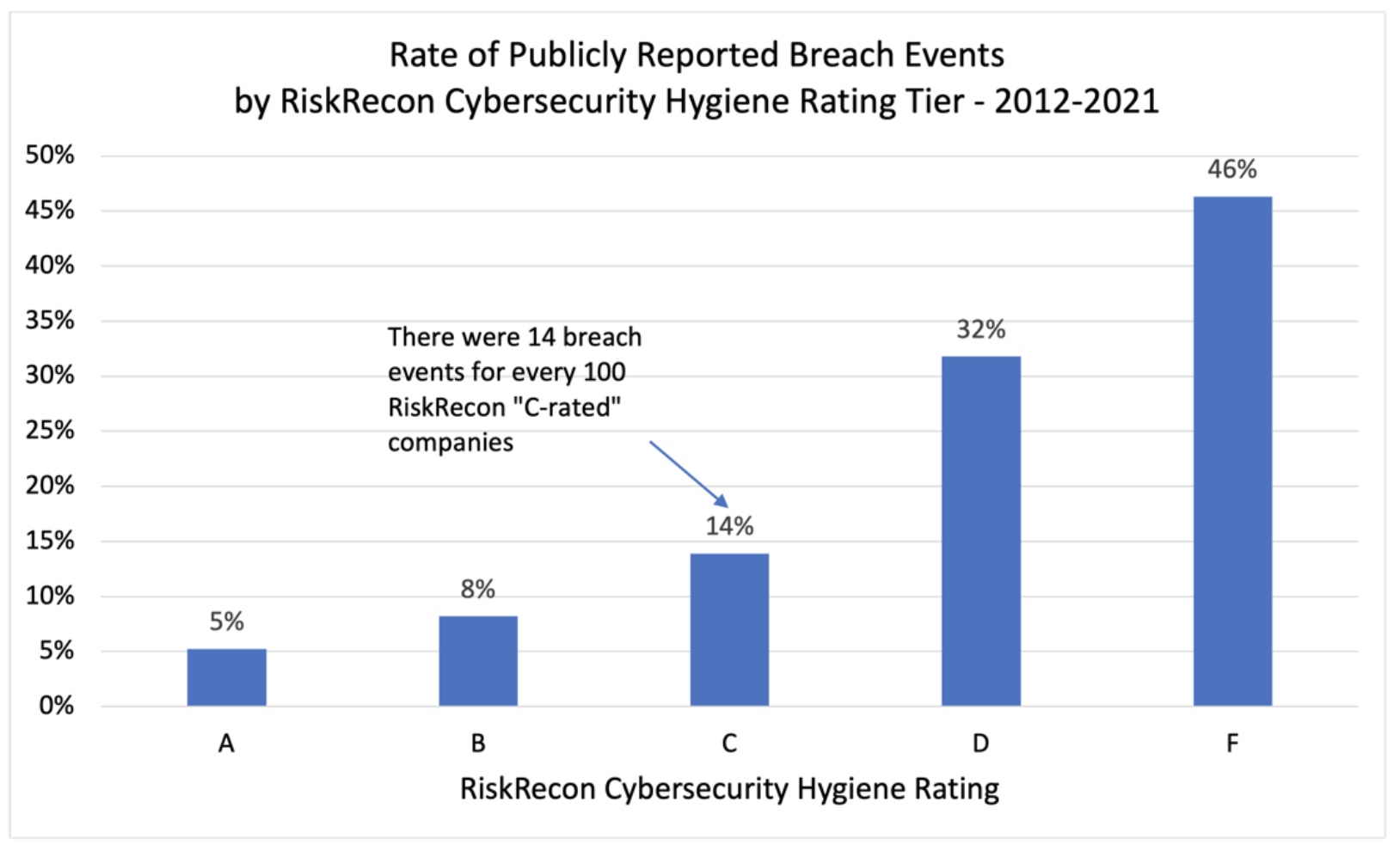
In fact, those things that I just mentioned represent 90 plus percent of all initial attack vectors of ransomware, as you dissect the attacks themselves. You could look at the NIST cybersecurity framework. Still, you could even boil it down even further to just, what are the basic information security elements commonly accepted for protecting an organization. I've been in the field since the mid-'90s and the basics haven't really changed. What we see is a deficit and I suppose to get more precise, a deficit in those just really basic areas. I use the term hygiene intentionally because there's a failure in doing just the basics.
Unfortunately, we’ve seen it time and time again that there is a deficit in a business' vendor portfolio – and you need to have the visibility to determine where that deficit lies and who it lies with. If you are part of a third-party cybersecurity risk management program, you probably are in the category of mature or advanced in your practices as an organization. It's dangerous to project that assumption on everyone. You can't make the assumption that every vendor you’re working with also has a mature information security program because the stats bear that it is not valid.
Jake Bernardes: I think you are right. If I think of deficit, I think of either not doing anything in a particular area or just being completely ineffective but there is often a lack of control or not wanting control over certain security areas, but that's very different from practices that effectively mitigate a present and known risk. So, when I think of deficit, I think of a lack of or ineffective control.
Download the report here to see the full results from our study and check back to get more of their thoughts on our blog!