Organizations are dependent upon their third-party vendors to provide such important services as payroll, software development or data processing. However, without having strong security controls in place vendors, suppliers, contractors or business partners can put organizations at risk for a third-party data breach. A third-party data breach is an incident where sensitive data from an organization is not stolen directly from it, but through the vendor’s systems that are misused to steal sensitive, proprietary or confidential information.
Sponsored by RiskRecon, a Mastercard Company and conducted by Ponemon Institute,1,162 IT and IT security professionals in North America and Western Europe were surveyed for this new study, Data Risk in the Third-Party Ecosystem. All participants in the research are familiar with their organizations’ approach to managing data risks created through outsourcing. Sixty percent of these respondents say the number of cybersecurity incidents involving third parties is increasing.
We define the third-party ecosystem as the many direct and indirect relationships companies have with third parties and Nth parties. These relationships are important to fulfilling business functions or operations. However, the research underscores the difficulty companies have in detecting, mitigating and minimizing risks associated with third parties and Nth parties that have access to their sensitive or confidential information.
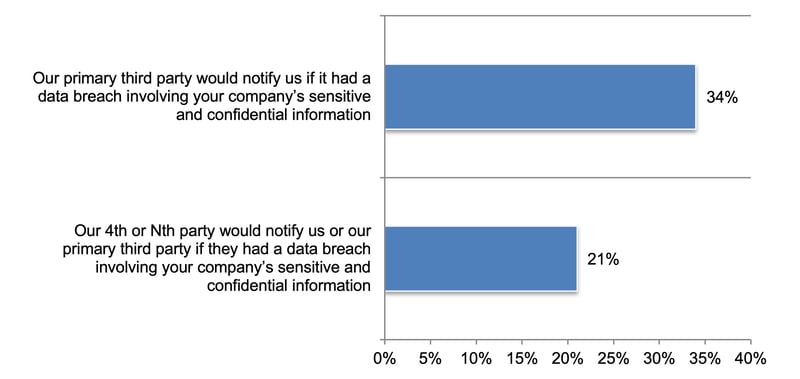
Third-and-Nth party data breaches may be underreported. Respondents were asked to rate how confident their organizations are that a third or Nth party would disclose a data breach involving its sensitive and confidential information on a scale from 1 = not confident to 10 = highly confident.
Figure 1 shows the very and highly confident responses (7+ on the 10-point scale).
Only about one-third of respondents say that they have confidence that a primary third party would notify their organizations (34 percent) and even fewer respondents (21 percent) say the Nth party would disclose the breach.
How confident is your organization that a third party or Nth party would disclose a data breach involving sensitive and confidential information?
On a scale from 1 = not confident to 10 = highly confident, 7+ responses presented
Based on the findings, companies should consider the following actions to reduce the likelihood of a third-party or Nth party data breach.
-
Create an inventory of all third parties with whom you share information and evaluate their security and privacy practices. Before onboarding new third parties, conduct audits and assessments to evaluate the effectiveness of their security and privacy practices. However, only 36 percent of respondents say that before starting a business relationship that requires the sharing of sensitive or confidential information their company evaluates the security and privacy practices of all vendors.
Organizations should have a comprehensive list of third parties who have access to confidential information and how many of these third parties are sharing this data with one or more of their contractors. Identify vendors who no longer meet your organization’s security and privacy standards. Facilitate the offboarding of these third parties without causing business continuity issues.
-
Conduct frequent reviews of third-party management policies and programs. Only 43 percent of respondents say their organizations’ third-party management policies and programs are frequently reviewed to ensure they address the ever-changing landscape of third-party risk and regulations. Organizations should consider automating third-party risk evaluation and management.
-
Study the causes and consequences of recent third-party breaches and incorporate the takeaways in your assessment processes. Only 40 percent of respondents say their third parties’ data safeguards, security policies and procedures are sufficient to prevent a data breach and only 39 percent of respondents say these data safeguards, security policies and procedures enable organizations to minimize the consequences of a data breach. In the past year, breaches were caused by such vulnerabilities as unsecured data on the Internet, not configuring cloud storage buckets properly and not assessing and monitoring password managers.
-
Improve visibility into third or Nth parties with whom you do not have a direct relationship. More than half (53 percent) of respondents say they are relying upon the third party to notify their organization when data is shared with Nth parties.
A barrier to visibility is that only 35 percent of respondents say their organizations are monitoring third-party data handling practices with Nth parties. To increase visibility into the security practices of all parties with access to company sensitive information – even subcontractors, notification when data is shared with Nth parties is critical. In addition, organizations should include in their vendor contracts requirements that third parties provide information about possible third-party relationships with whom they will be sharing sensitive information.
-
Form a third-party risk management committee and establish accountability for the proper handling of third-party risk management program. Many organizations have strategic shortfalls in third-party risk management governance. Specifically, only 42 percent of respondents say managing outsourced relationship risk is a priority in our organization and only 40 percent of respondents say there are enough resources to manage these relationships.
To improve third-party governance practices, organizations should centralize and assign accountability for the correct handling of their company’s third-party risk management program and ensure that appropriate privacy and security language is included in all vendor contracts. Create a cross-functional team to regularly review and update third-party management policies and programs.
6. Require oversight by the board of directors. Involve senior leadership and boards of directors in third-party risk management programs. This includes regular reports on the effectiveness of these programs based on the assessment, management and monitoring of third-party security practices and policies. Such high-level attention to third-party risk may increase the budget available to address these threats to sensitive and confidential information.
Download the study today to see the full results from our research.







