 By: Kelly White, Founder, RiskRecon, a Mastercard Company
By: Kelly White, Founder, RiskRecon, a Mastercard Company
Any company operating a modern information technology environment can fall victim to system-encrypting ransomware. But not every company has fallen victim. Do companies that experience an operations-impacting ransomware event have poor cybersecurity hygiene? Or is the quality of cybersecurity hygiene not a factor in the frequency of ransomware events? To answer these questions, RiskRecon analyzed the cybersecurity hygiene on the day of ransomware detonation for 622 organizations spanning 633 ransomware events occurring between 2017 and 2021.
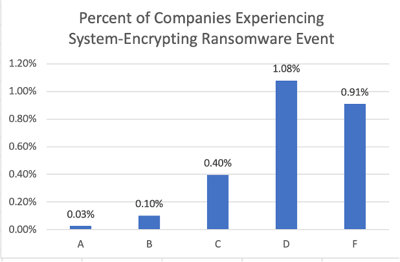
Based on RiskRecon’s comparison population of cybersecurity ratings and assessments of over 100,000 entities, companies that RiskRecon observes to have very poor cybersecurity hygiene in their Internet-facing systems (a ‘D’ or ‘F’ RiskRecon rating) have about a 40 times higher rate of destructive ransomware events in comparison with companies that have clean cybersecurity hygiene. As shown in the chart below, only 0.03% of ‘A-rated’ companies were victims of a destructive ransomware attack, compared with 1.08% of ‘D-rated’ and 0.91% of ‘F-rated’ companies.
The cybersecurity conditions underlying the RiskRecon rating reveal just how poor the cybersecurity hygiene is of companies, on average, that fall victim to a material system-encrypting ransomware attack. For example, ransomware victims have an average of 11 material software vulnerabilities in their internet-facing systems, in comparison with only one issue in the general population. Looking at network services that criminals commonly exploit, ransomware victims expose 3.3 times more unsafe network services to the internet than the general population.
The table below contains a comparison of the cybersecurity conditions of victim companies at the time of ransomware detonation relative to the general population of approximately 100,000 companies.
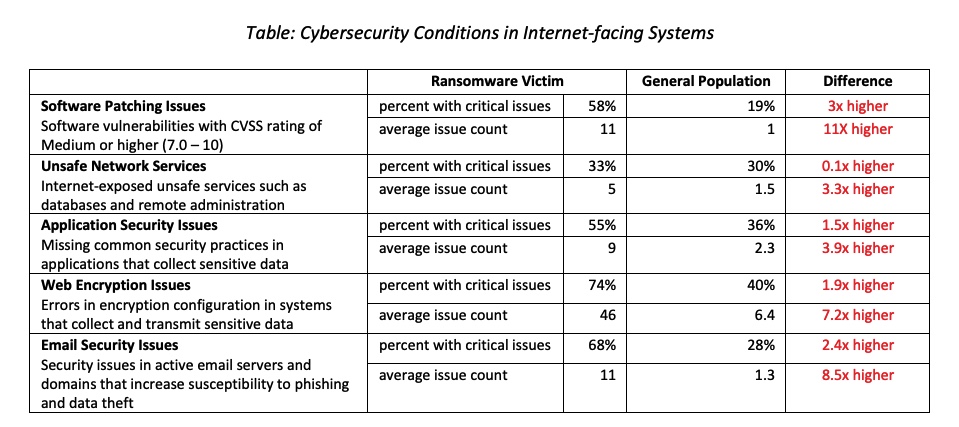
In comparison with the general population, the cybersecurity hygiene of victims of ransomware is very unhealthy.
The data clearly shows that good cybersecurity hygiene matters. On average, companies experiencing system-encrypting ransomware events that are significant enough to be newsworthy have significantly worse cybersecurity hygiene than the general population. Based on RiskRecon’s analysis of their internet-facing systems they have an 11 times higher rate of material software vulnerabilities, 3.3 times higher rate of unsafe network services, and an 8.5 times higher rate of email security issues.
While the cybersecurity hygiene issues RiskRecon observes through its passive analytics of Internet-facing systems and accessible signals may not be the exact vectors the criminals exploited to compromise each victim organization, their presence is a strong indicator that these organizations, on average, do not have robust cybersecurity risk management programs.
Check out this detailed study, to learn more about how RiskRecon's cybersecurity ratings correlate to organizations affected by ransomware attacks.







