Within this blog post, readers will learn if breach events are more common during peak holiday seasons and the time elapsed from the actual breach to the public disclosure of the event. As always, this analysis is from our latest report on Risk Insights from 10 years of Breach Events.
Time Elapsed from Breach to Public Disclosure
For 80% of events, the time between initial compromise and disclosure is less than three months. This seems reasonable given some days to detect the event, followed by weeks to investigate, and then work with legal and PR to formulate and submit the necessary filings and disclosures.
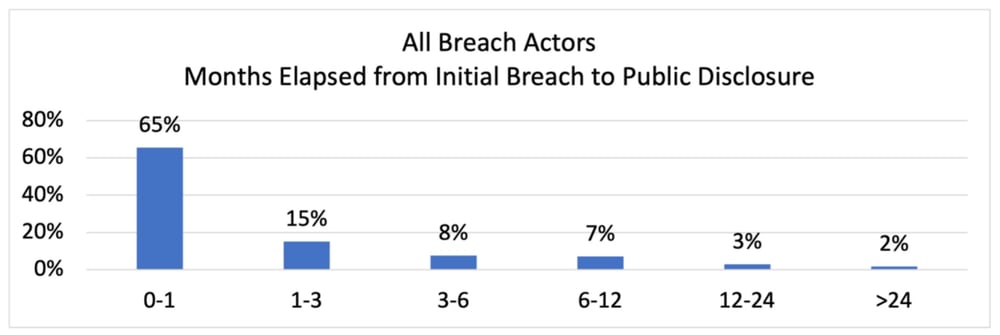
The events of particular interest are the 5% that take longer than twelve months to disclose. In most of these cases, the systems were compromised long before detection. Here are some examples of delayed disclosure breach notices:
-
“[Company] has discovered its web hosting provider failed to patch vulnerabilities which were exploited by cybercriminals to gain access to its website and protected health information of applicants for benefits for the past seven years.”
-
“Healthcare Provider Discovers Patient Data Exposed Online for Over Four Years”
-
“After thorough investigation, it was determined that the employee improperly accessed certain patient information between October 2009 and February 2019.”
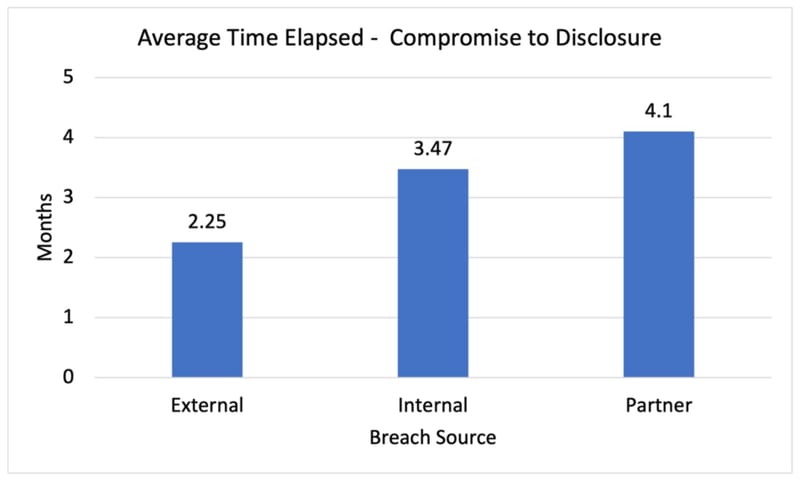
Disclosure of breach events rooted in compromise of a partner took the longest to disclose, averaging 4.1 months. Insider breach events took 3.5 months to disclose, 54% longer than compromises by external actors which averaged 2.25 months.
The problem of timely partner-related breach event reporting is magnified when examining the disclosure time distributions by actor. For breaches occurring within their own environment, companies disclosed 68% of events within one month of the initial compromise. In contrast, for breaches rooted in the compromise of a vendor, companies only disclosed 38% of breach events within one month.
Twenty-one percent of the vendor breach events took longer than six months to disclose. In comparison, only 11% of breach events in an organization’s own environment took longer than six months.
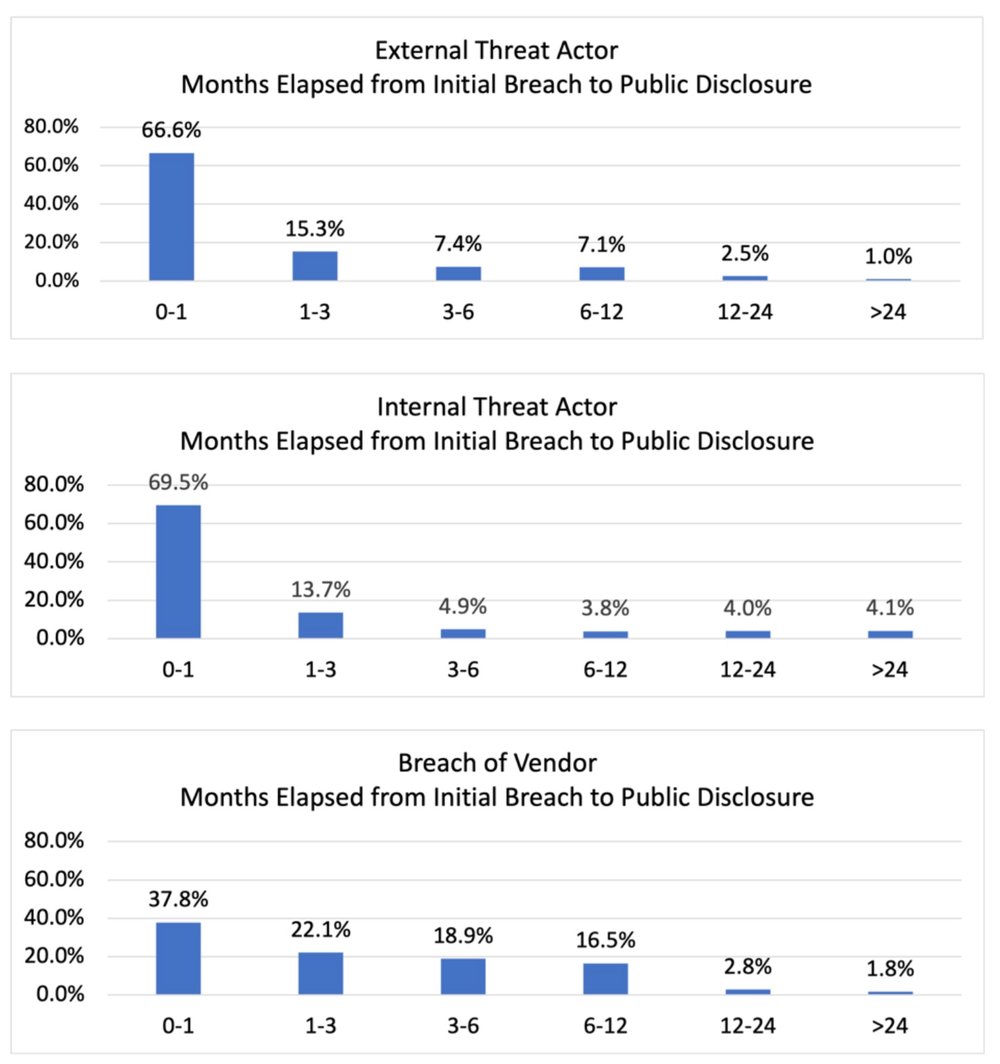
RiskRecon Risk Management Insights: Risk managers should take serious notice of the lags in publicly disclosing vendor-related breach events. Only 38% were reported within 30 days of the breach, in comparison with 68% for all other sources. Even worse, 28% of those vendor breaches took six months or longer to disclose. That is a lot of time for criminals to freely leverage your stolen assets and puts you at risk of violating breach disclosure notification rules.
There is clearly room to improve vendor-related breach notifications. Perhaps there needs to be better lines of communication between customers and vendors and tighter vendor SLAs on reporting breach events. Perhaps companies would be wise to expand their own deep and dark web monitoring to detect breaches of their vendors.
U.S. Holiday Breach Event Frequency
The exact date of the initial compromise was documented in 13% (1,217 of 8,892) of the public breach notifications. At the risk of being overly descriptive, we measured the frequency of breach events occurring during the windows of major U.S. holidays during the 10-year period by:
-
1) Building a single-year calendar containing the holiday windows for the years 2012-2021. This is necessary because some holidays, such as Thanksgiving, vary in date from year to year. The holiday window was constructed to contain three days before and three days after each official holiday, accounting for vacation time surrounding each holiday.
-
2) Assigning all breach events to the month/day date that they occurred. For example, all events occurring on July 21 throughout the 10 years were assigned to July 21 on the single-year breach calendar.
-
3) Comparing the breach event frequency for holiday windows with that of the average day in the single-year breach calendar.
The data shows that five of the nine major U.S. holiday windows have a higher breach rate than the average daily breach rate. The days surrounding Veterans Day had the highest holiday-related breach event frequency, running at 253% above average. Christmas and Thanksgiving also ran hot at 187% and 140% above average. Surprisingly, the big U.S. vacation windows of Independence Day, Labor Day, and Memorial Day ran below average.
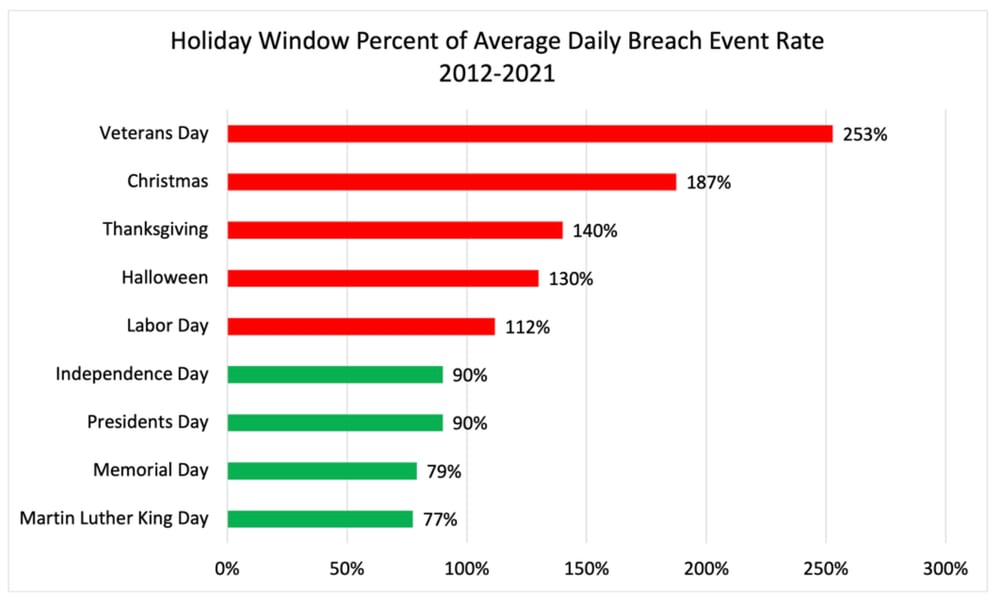
RiskRecon Risk Management Insights: There are no breaks for the information security teams. Criminals are increasing their compromise campaigns on many of the major holidays. Particularly, maintain your capabilities at 100% for the holiday windows of Veterans Day, Christmas, Thanksgiving, Halloween, and Labor Day.
Check back soon for most risk management insights and analysis from RiskRecon!







