 By: Kelly White, Founder, RiskRecon, a Mastercard Company
By: Kelly White, Founder, RiskRecon, a Mastercard Company
Having been a cybersecurity practitioner for 25 years now, I have been around long enough to collect a few unfounded industry anecdotes. One of those that has been oft-repeated is, “The most secure company is the one that recently was breached.” The reasoning was that companies that recently experienced a material breach would naturally make the investments necessary to strengthen their security program to minimize the likelihood of such an event occurring again.
On the surface, this seems that it would be true, particularly for companies experiencing a system-encrypting ransomware event. What could be more motivating to get your cybersecurity house in order than a ransomware event that disrupts your ability to operate?
So, do companies who have experienced a destructive ransomware event observably improve their cybersecurity hygiene? What about different industries? Do some industries respond to ransomware events better than others? In this study we answer that question by comparing the cybersecurity state of 181 victim companies on the day ransomware was detonated in their environment with their cybersecurity state one year later.
The Study
The study population consists of 181 companies whose ransomware event was publicly reported and resulted in disruption of operations due to system encryption. The population is also limited to those companies for which at least one year has passed since the ransomware event.
To measure how companies change their cybersecurity practices following a ransomware event, RiskRecon leveraged its cybersecurity ratings and platform to assess the cybersecurity hygiene of each company at the time of ransomware detonation and one year later. As a leading cybersecurity ratings platform, RiskRecon continuously monitors the cybersecurity quality of millions of companies using passive assessment techniques.
For this study, we focused our analysis on core cybersecurity hygiene practices that are central to defending against ransomware attacks and serve as a proxy for the overall quality of the cybersecurity program. These dimensions are strongly aligned with Coveware’s 2021 ransomware study as essential to defending against ransomware attacks, in which they found that 42% of ransomware attacks were initiated through compromising an unsafe network service, 42% through a phishing attack, and 14% through compromise of a software vulnerability.
Conditions Twelve Months Later – All Organizations
I am sorry to say it, but overall, companies don’t show improvement in the cybersecurity hygiene of their internet presence one year after a system-encrypting ransomware event. At best, they take one step forward and one step back, showing improvement in software patching and degradation in restricting access to unsafe network services.
The table below details the mixed bag. On the positive side, one year after the breach, the number of victims with important software patching issues exposed to the internet decreases by 12% and, for those that still have material software vulnerabilities, they reduced their issue count by 15%. On the downside, the number of victim companies exposing commonly exploited network services increased by 50%. Remember that Coveware stat – percent of ransomware events start with a compromise of an unsafe network service?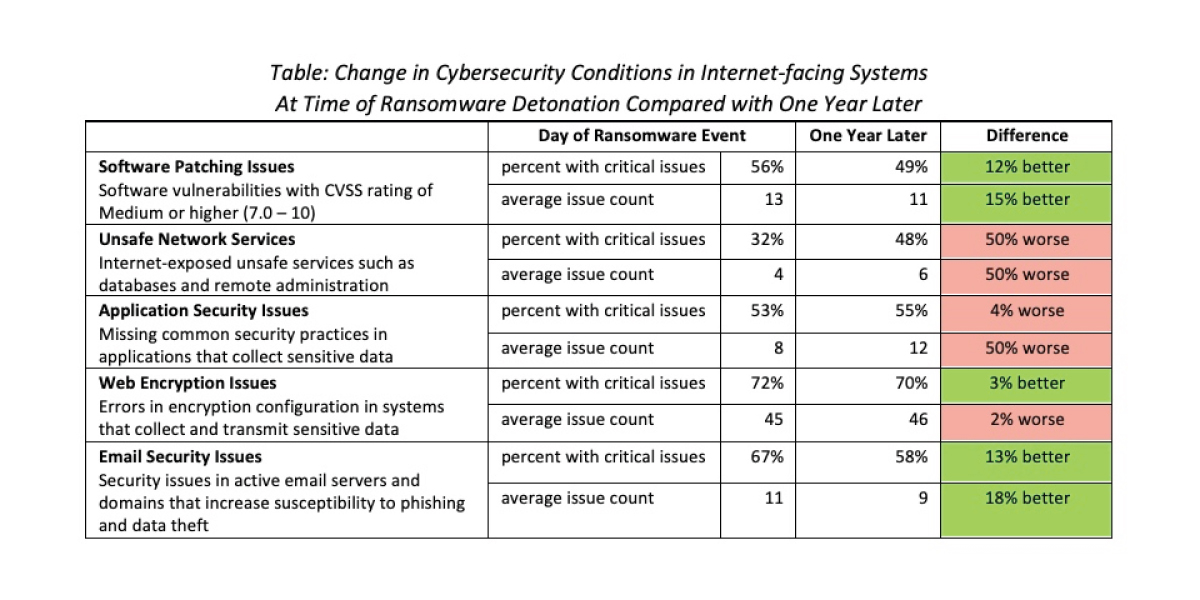
Conditions Twelve Months Later – By Sector
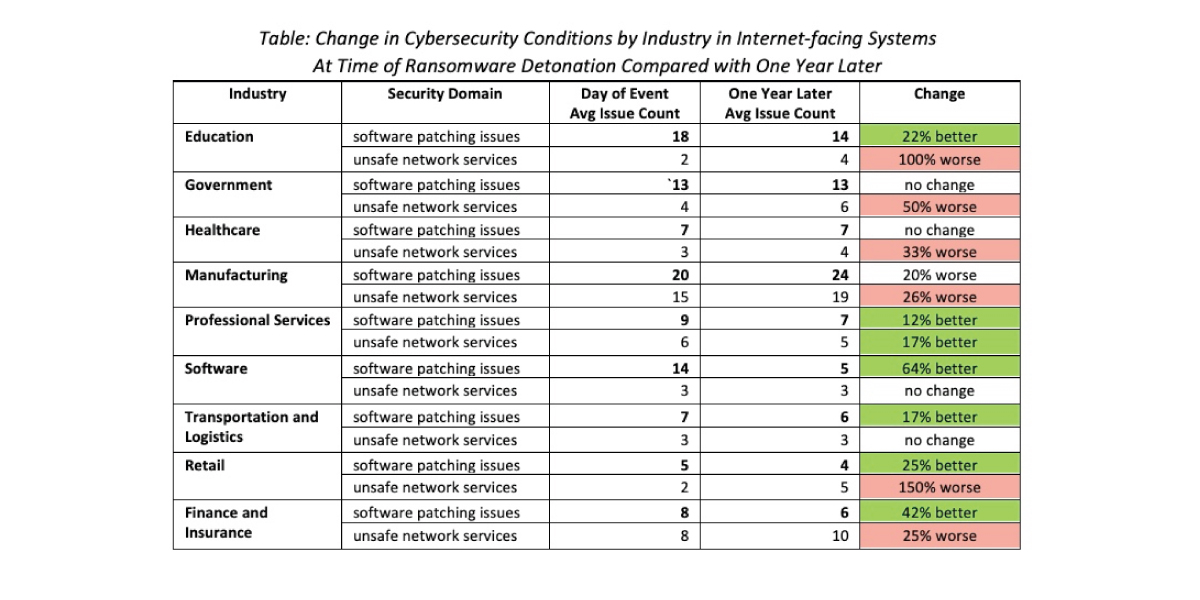
For our analysis of cybersecurity hygiene at the industry level, we chose to look only at two dimensions – software patching and unsafe network services. Presenting all five security dimensions is just too much data for this summary paper. We have reserved detailed industry analyses for a separate piece.
By our research, the healthcare, education, and government sectors together accounted for 52% of all publicly-reported ransomware events occurring in the last few years. Given the pressure on the sectors, you would think their cybersecurity hygiene would markedly improve post-attack. Not so. The hygiene of victims in the government and healthcare sectors declined across both measures, increasing the amount of vulnerable software and unsafe network services exposed to the internet. While the education sector reduced their software vulnerability exposure count by 21%, they increased the number of unsafe network services that criminals commonly compromise.
Professional services improved their software vulnerability management and network filtering practices. The software and transportation/logistics industries also improved their software patching practices while holding steady on controlling exposure of unsafe network services. Retail and finance were a mixed bag, improving in software patching while degrading in the other.
Conclusion
It seems that experiencing a major ransomware event, one significant enough to be newsworthy, would motivate an organization to markedly improve its cybersecurity posture. The evidence does not support that conclusion. At best, it is a mixed bag, with organizations improving their software vulnerability management discipline while still struggling to control the network services they expose to the internet.
It seems odd that this is the case. During our research, we noted that many companies were increasing their cybersecurity spending in response to the attacks. Yet the results of the reported increase in funding don’t appear to materially improve their conditions. Perhaps it is true that good cybersecurity isn’t something that you can just buy; it takes strong, consistent prioritization and support from the top that drives a change in the way the organization operates. That is hard.
This paper is accompanied by another RiskRecon research paper titled “The Cybersecurity Hygiene of Ransomware Victims.” In this paper, we reveal the cybersecurity conditions of ransomware victims at the time of detonation. We also benchmark their cybersecurity performance against that of the larger population.







