As evidenced by the continuous flow of news headlines detailing new victims and real-world consequences, the trend of cyber vulnerabilities being exploited is only continuing to grow. As a result, government agencies are taking more active roles in helping both government and private industry address cybersecurity issues.
On July 28, 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC), the United Kingdom’s National Cyber Security Centre (NCSC), and the U.S. Federal Bureau of Investigation (FBI) released a Joint Cybersecurity Advisory detailing the top vulnerabilities exploited by malicious actors over the past year.
Organizations must employ cybersecurity programs that ensure a strong security posture. A robust cybersecurity program requires organizations to look beyond their internal systems and at third parties who could provide vulnerable points of entry enable the loss of sensitive data.
To address the ever-evolving cybersecurity threat landscape, RiskRecon continuously monitors it for trends and responds by enhancing the platform’s ability to detect vulnerable systems. We have reviewed the Joint Cybersecurity Advisory and want to showcase how our customers can gain insights into third party and vendor systems used by their own organizations. This can help customers understand if they may be susceptible to the top vulnerabilities mentioned in the Joint Cybersecurity Advisory.
RiskRecon employs passive, non-invasive techniques to discover an organization’s public systems and analyze those systems’ cybersecurity risk posture. RiskRecon’s passive analysis relies on open-source intelligence assessment methodology and focuses on publicly accessible systems observed from the Internet. RiskRecon assessments are risk-based; every issue is contextualized based on the severity of the issue and the value of the system in which the issue exists.
Using our passive scanning techniques, we enable our customers to identify the following software products, versions, and specific vulnerabilities as mentioned in the Joint Cybersecurity Advisory.
-
Atlassian Crowd – CVE 2019-11580
-
Drupal – CVE 2018-7600
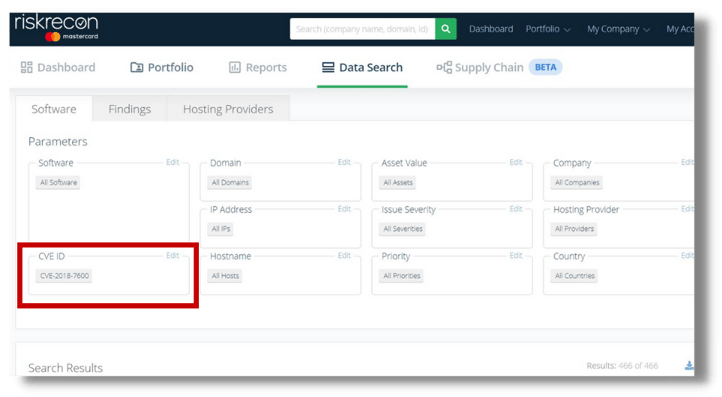
Using our passive scanning techniques, we also enable our customers to identify the following software products as mentioned in the Joint Cybersecurity Advisory.
-
Citrix Application Delivery Controller (ADC)* - CVE 2019-19781
-
Citrix Gateway* - CVE 2019-19781
-
F5 BIG-IP* - CVE 2020-5902
-
Microsoft SharePoint
-
Fortinet
* Vulnerability identification is available by requesting a custom report through the RiskRecon support portal
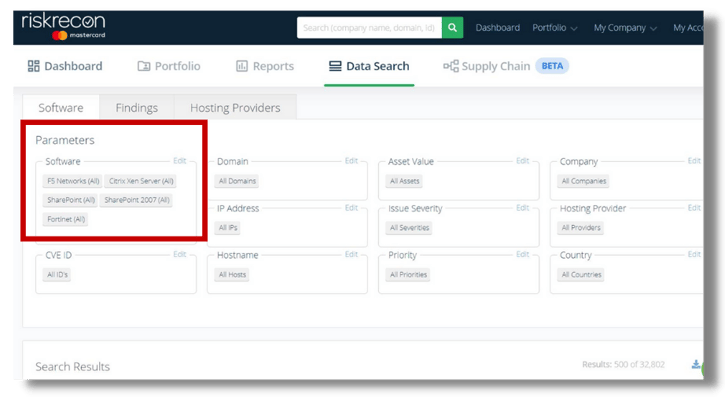
Beyond the Joint Cybersecurity Advisory, we are constantly evaluating ways to increase our visibility and help our customers manage their third-party risks. This includes the ability to detect additional products, versions, and vulnerabilities. Passive scanning provides varying levels of insights into an organization’s infrastructure (for example some systems are typically internal to an organization and not internet-facing). In other cases, passive scanning may not yield full visibility into the specific vulnerabilities of a product; however identification of a product and information system provides critical awareness and insight for risk management.
We are currently working to establish greater visibility and identification capabilities for several products. Below is a sample of our pipeline, with many more to come.
-
MobileIron Core & Connector
-
Pulse Connect Secure
-
SonicWall
-
SD-WAN
To learn more about RiskRecon’s platform and how you can get the most out of it, schedule a demo today.




