By Kelly White | May 31, 2018
While security vulnerabilities are found in many technologies, their presence doesn’t necessarily equal risk. Borrowing the FAIR Institute’s definition, risk is the probable frequency and magnitude of loss. Knowing what security vulnerabilities are present in your infrastructure can help you understand the probable frequency, but it offers no indication of loss magnitude. Rather, solving risk requires two foundational data points: what security vulnerabilities your technology has, and the value of the assets in which those vulnerabilities exist. Without that context, a given vulnerability is the same as any other.
To illustrate, let’s look at two remediation scenarios:
Scenario 1: Risk analysis of 2 vulnerabilities
Consider the threat of domain hijacking. Assume you have two domains: exampledomain.com and exampledomain.sucks. Both are missing the domain setting clientTransferProhibited which helps prevent domain hijacking. Which vulnerability is the higher risk? Additional context is needed to differentiate and prioritize. Exampledomain.com is used to host high value web properties including an online banking portal; whereas exampledomain.sucks is a near-zero value asset that’s been defensively registered to prevent malcontents from smearing the company's reputation. This context makes clear that exampledomain.com presents the greater risk.
Scenario 2: Risk analysis of 32,829 vulnerabilities
Yes, this is a real number. RiskRecon continuously assesses and monitors the information risk performance of thousands of companies; we discovered 32,829 issues in the internet-facing systems of just one of them. With so many, which ones represent the highest risk? Which ones don't matter? Why? This assessment is the heart of risk analysis. We can use issue severity and asset value to help.
Issue Severity
Opening 32,829 trouble tickets is simply a non-starter. So how do you prioritize? A practical starting point is to consult the vulnerability CVSS ratings provided through the MITRE-operated Common Vulnerabilities and Exposures program. The CVSS ratings directionally inform us of the severity of each vulnerability, a key part of the risk equation.
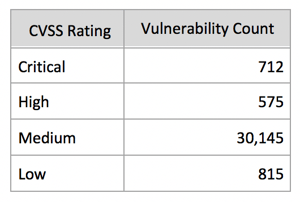
CVSS rating information is helpful. You can readily see the Critical and High severity vulnerabilities to address. It’s also pretty safe to ignore those that are Low severity. But with 30,145 Medium severity issues, some of those will definitely matter. Which ones? When I was a CISO of a large financial institution, managing the high number of Medium severity issues was always a struggle.
Asset Value
The CVSS rating information gets us at best half-way through the risk equation – understanding issue severity. Let’s go ahead and add asset value using the following rating scheme:
- High value assets are transaction portals that require authentication to access or that collect non-public information such as tax IDs and email addresses;
- Medium value assets are systems that are brochureware sites, but that are network neighbors to high value assets;
- Low value assets are systems that are brochureware sites that are not network neighbors to high value assets;
- Idle value assets are simply parked domains.
By adding asset value context to the assessment, we get a much more useful prioritization of issues based on actual risk. The visualization provides a ready roadmap for action.
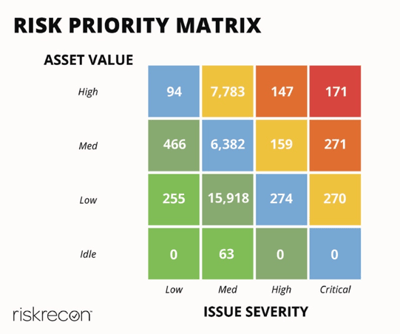
The issues in the top right of the matrix stand out; those 171 critical vulnerabilities that exist in high value assets (the red box). Once those are addressed, we'd likely pursue the 147 high severity vulnerabilities in high value assets and the 271 critical severity vulnerabilities in medium value assets (the orange boxes). Importantly, we also know what not to pursue? the nearly 17,000 issues in the lower left part of the matrix (the green boxes).
How RiskRecon helps
Knowing the value of hundreds and often thousands of systems is seemingly unapproachable. Typically, asset value is determined manually by an analyst and recorded in an asset tracking database – a very long and labor-intensive process. RiskRecon has invented algorithms that automatically discover systems, identify system vulnerabilities, and determine asset value based on analysis of system content, code and configurations. Automating this assessment saves untold hours of work and provides more accurate, reliable results.
Remember that information risk management is about managing risk― the probable frequency and magnitude of loss― not managing vulnerabilities. Knowing the magnitude of loss requires understanding asset value. Adding the context of asset value to security vulnerabilities enables you to know what to do and what not to do. And that is the essence of risk management.




