 In part one of this blog, we discussed how many companies are continuing to operate any version of SolarWinds Orion directly on the Internet as seen by the RiskRecon platform. In this post we will look how many organizations are continuing to run SolarWinds without applying the recommended security updates.
In part one of this blog, we discussed how many companies are continuing to operate any version of SolarWinds Orion directly on the Internet as seen by the RiskRecon platform. In this post we will look how many organizations are continuing to run SolarWinds without applying the recommended security updates.
Number of Entities Patching SolarWinds Orion
Shortly after disclosure of the breach, SolarWinds advised customers to upgrade to Orion 2020.2.4 to address the SUNBURST and SUPERNOVA issues. Based on RiskRecon’s analysis, only 8% of companies that continue to operate SolarWinds on the Internet have followed the security advisory and upgraded to Orion 2020.2.4.
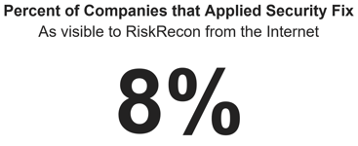
Given that Orion SUNBURST and SUPERNOVA are such highly visible and active threats, it is discouraging to see such a small number of instances being patched. Of all Orion systems, these systems exposed directly to the Internet are arguably the most vulnerable, with less compensating controls to mitigate risks.
SolarWinds Orion Vulnerability Exposure
Of the companies operating SolarWinds Orion directly on the Internet, 4% are operating a version that contains the SUNBURST malicious code that automatically provides miscreants remote control of the environment. Another 33% are operating a version that is vulnerable to SUPERNOVA exploit.
 Unfortunately, the organizations running these vulnerable instances on the Internet are not insignificant. They include universities, state and local governments, Fortune 500 companies, and system hosting providers.
Unfortunately, the organizations running these vulnerable instances on the Internet are not insignificant. They include universities, state and local governments, Fortune 500 companies, and system hosting providers.
Observed Versions of SolarWinds Orion
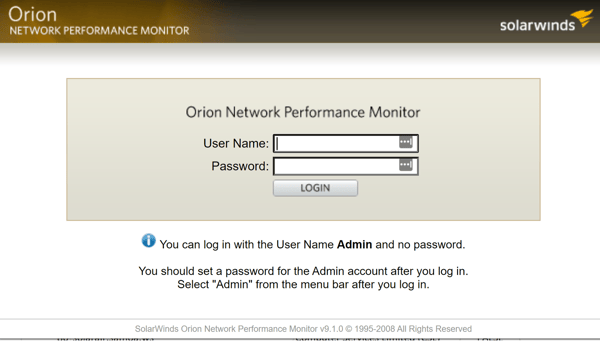
The Orion versions operating directly on the Internet are as old as version 9.0.0, released circa 2008. The most common version observed version was 2020.2.1 HF2 at 31%. The screenshot below is an example of a particularly ancient instance running SolarWinds Orion 9.1.0, shown at the bottom of the screenshot. Even worse, notice the information tip advising that “You can log in with the User Name Admin and no password.”
Conclusion
Observed from the Internet, shutting down instances of SolarWinds Orion is the most significant measure that enterprises have taken to reduce their risk exposure, with a 25% decrease in Internet-visible instances between December 13, 2020, and February 1, 2021. Particularly exciting to see is the impact that third-party risk teams have on reducing their exposure, as measured by a 52% decrease in Internet-facing SolarWinds instances among companies monitored by RiskRecon third-party risk management customers. That said, the data shows that a large majority of companies have taken no action to address their SolarWinds exposure – not shutting down their Internet instance or even applying the security patches essential to preventing a significant breach.
One would think that in the face of such a widely known and significant security issue as SolarWinds Orion SUNBURST and SUPERNOVA that all companies would have taken quick action to address the risks. Unfortunately, that is not the case. Companies that are subject to third-party risk management by their customers were more responsive in dealing with the risk, but many remain exposed. In the end, the response to the SolarWinds breach serves to show that so many companies remain negligent in managing risk well.







