Throughout our detailed analysis of 8,892 publicly reported breach events occurring between 2012 and 2021, we've gleaned many insights that can assist risk management professionals as they are looking to secure their organizations from a harmful cyberattack. In this post, we used the RiskRecon platform to look at the cybersecurity hygiene of those firms who experienced a breach event in our research to determine the security standing of the firm at the time of the event.
Cybersecurity Hygiene
Do companies with good cybersecurity hygiene have lower rates of breach events? We answered this question by correlating the RiskRecon cybersecurity ratings and assessment information of each company with the breach event data. The RiskRecon cybersecurity ratings and assessment platform continuously monitors the cybersecurity hygiene of millions of companies, analyzing areas such as software patching, network filtering, and application security.
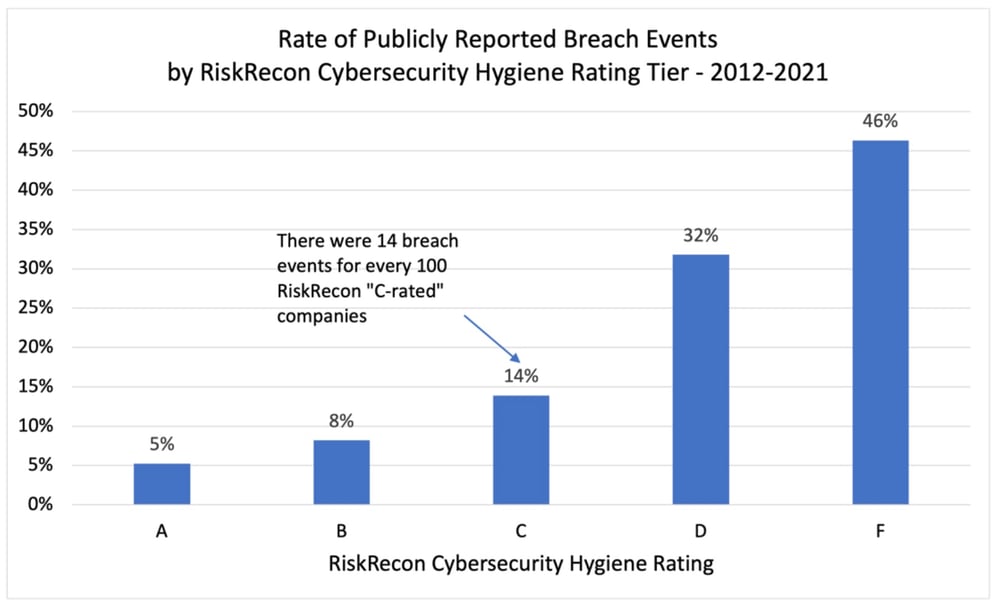
Companies that have very poor cybersecurity hygiene in their internet-facing systems (a ‘D’ or ‘F’ RiskRecon rating) have a seven times higher frequency of breach events in comparison with companies that RiskRecon observes to have very good cybersecurity hygiene (an ‘A’ RiskRecon rating). As shown in the chart below, the rate of breach events for ‘A-rated’ companies is 5 for every 100 companies from 2012-2021, compared with 32 for every 100 ‘D-rated’ companies and 46 for every 100 ‘F-rated’ companies.
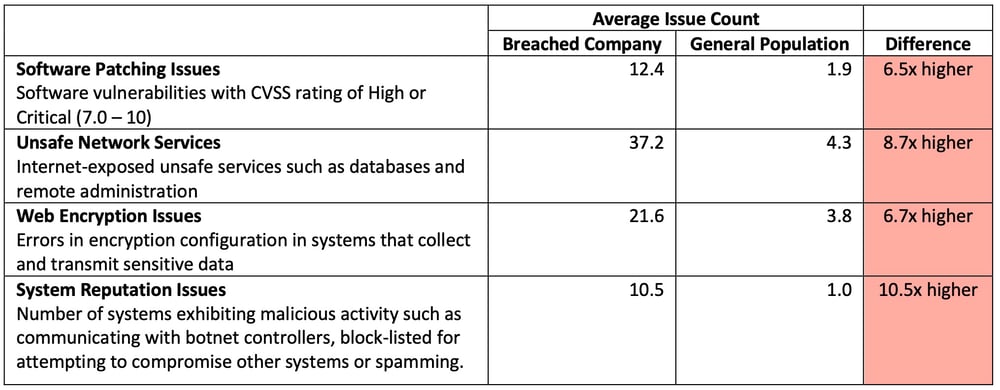
Looking underneath the ratings, the assessment data shows a stark contrast in average cybersecurity conditions of breached organizations compared with the general population. Those that publicly reported a breach event between 2012 and 2021, on average, have:
-
6.5 times more high and critical severity issues in their internet-facing systems.
-
8.7 times more unsafe network services exposed to the internet, such as RDP, telnet, database listeners, NetBIOS, and SMB.
-
10.5 times higher rate of malicious activity such as botnet communications emanating from their systems to the internet.
-
6.7 times higher count of web applications that collect sensitive data that has HTTP encryption issues such as expired certificates, weak encryption algorithms, or invalid certificate subjects.
Table: Comparison of the count of security issues in internet-facing systems on the day of detonation
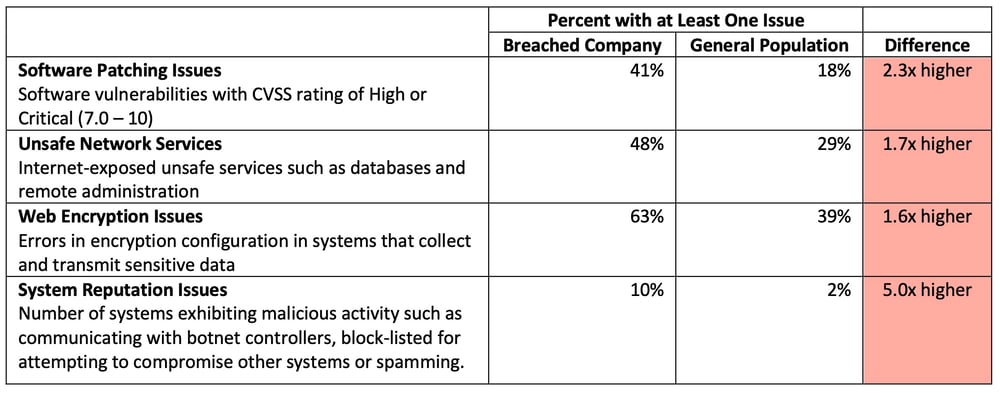
Ignoring issue counts and just looking at the percent of companies with one or more issues across the cybersecurity domains, the companies publicly reporting a breach between 2012 and 2021 stand out as having very poor hygiene in comparison to the general population. In comparison with the general population, the breached company population has:
-
2.3 times more companies with at least one high or critical severity software vulnerability in their internet-facing systems.
-
1.7 times more companies with at least one unsafe network service exposed to the internet.
-
5 times more companies with at least one system exhibiting malicious activity such as botnet communications.
-
1.6 times more companies with at least one sensitive web application that has HTTP encryption issues such as expired certificates, weak encryption algorithms, or invalid certificate subjects.
Table: Comparison of percent of organizations with at least one issue in their internet-facing systems
No doubt, companies with good hygiene get breached, but, as a group, they are breached much less frequently. They are simply more difficult to compromise, and they are more likely to have detective and response controls that detect the compromise before it escalates to a publicly reportable breach event.
RiskRecon Risk Management Insights: Do business with companies that have good cybersecurity hygiene. The data shows that those with good hygiene have a seven times lower rate of publicly reported breach events relative to companies with poor hygiene. RiskRecon cybersecurity ratings can help you quickly sort those with good hygiene from those with poor hygiene.
Where do we go from here?
This study of 8,892 publicly reported breach events occurring within 109,000 closely monitored companies from 2012 to 2021 yields numerous valuable insights. First and foremost, it shows just how much the threat pressure has increased, with the number of publicly reported events increasing 314% over the decade. The peak breach year, 2020, was 505% higher. During the ten years, 5.5% of companies reported at least one breach event, with the peak year seeing nearly 2.3% reporting.
The second startling insight is the stunning growth in the percentage of companies breached in each industry. Industries such as utilities, hospitality, and natural resources, which were previously passed by are now common targets. Risk models that use industry-specific breach event frequency data should be updated frequently – things are changing fast.
External and internal threat actors obviously remain active, targeting both enterprises directly and the vendors to whom companies have outsourced systems and services. While no threat actor or breach method can be ignored, the data shows that external threat agents and partners represent a growing dimension of breach events. And the data shows that threat actors do not rest on major holidays, requiring enterprises to maintain their guard 24x7x365.
Correlating the RiskRecon cybersecurity ratings and assessment data with the breach events, the data clearly shows that companies with good cybersecurity hygiene have dramatically fewer breach events. Companies with good cybersecurity hygiene have a seven times lower frequency of breach events than companies with very poor hygiene. If you are managing supply chain risk, do business with companies that have good cybersecurity hygiene. If you are managing internal cybersecurity, be a business that you would count on to protect your risk interests.
Remember, you can outsource your systems and services, but you can’t outsource your risk. RiskRecon makes it easy to understand and act on your third-party cybersecurity risks.







