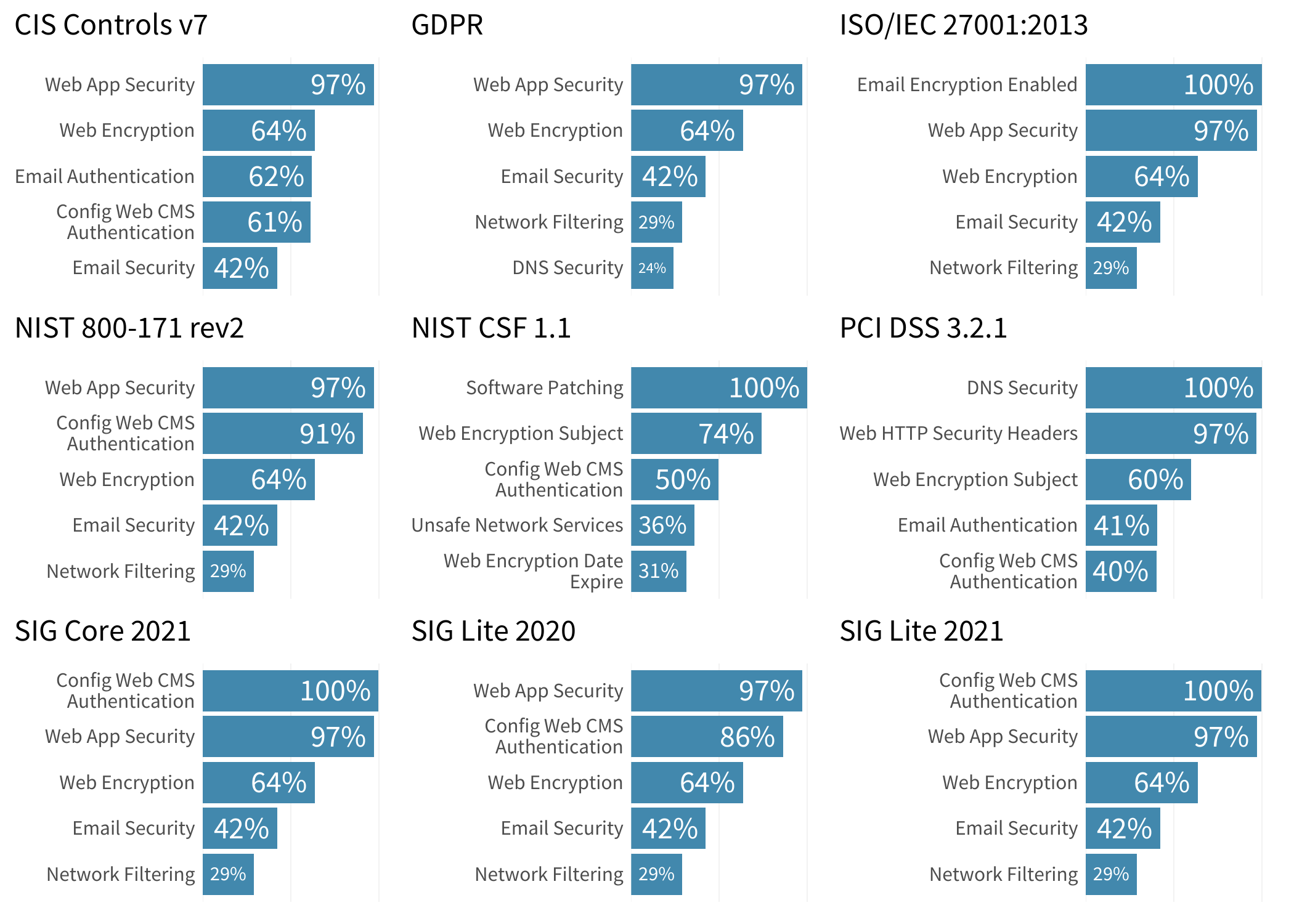
Recently, RiskRecon and the Cyentia Institute launched a research report called, The State of Noncompliance in Cyber Risk, which aimed to understand which regulations related to third-party risk management are the toughest for firms to meet, and what parts of these standards are causing the most issues as seen by the RiskRecon platform. During a blog series that will be published out over the next few weeks, we will examine the details and points from that report, breaking things down in bite sized pieces.
In this blog we will look at the idea of noncompliance vs. actual risk. Although you may not meet a certain element of a compliance standard that we've identified, it is not necessarily true that it leaves your organization at risk.
Just as the business criticality of an asset increases the relevance of a noncompliance finding, so does the severity of a flaw, or weakness, that causes a finding. With that in mind, the next step in our analysis is to examine the noncompliance findings against a dimension that may provide a better link between compliance and actual security. To describe that lofty goal of actual security, we’ll use a measure that we’ve used in several previous studies, finding density. Finding density is an organizational metric that takes the number of important findings found on high value assets, divided by the total number of high value assets at the firm. This provides a stable measure to compare large enterprises with smaller organizations.
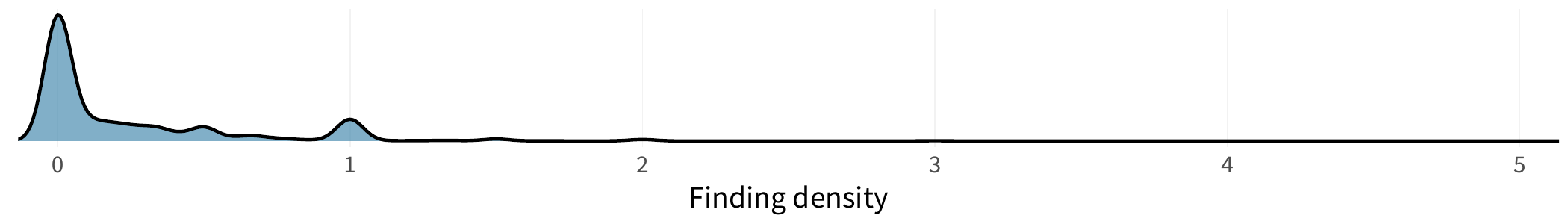
Looking across all standards, the finding density is relatively uniform. The overall density is displayed below in the figure here.
We get interesting results when we examine the relationship between organizations with compliance-specific issues, and finding density, as seen below.
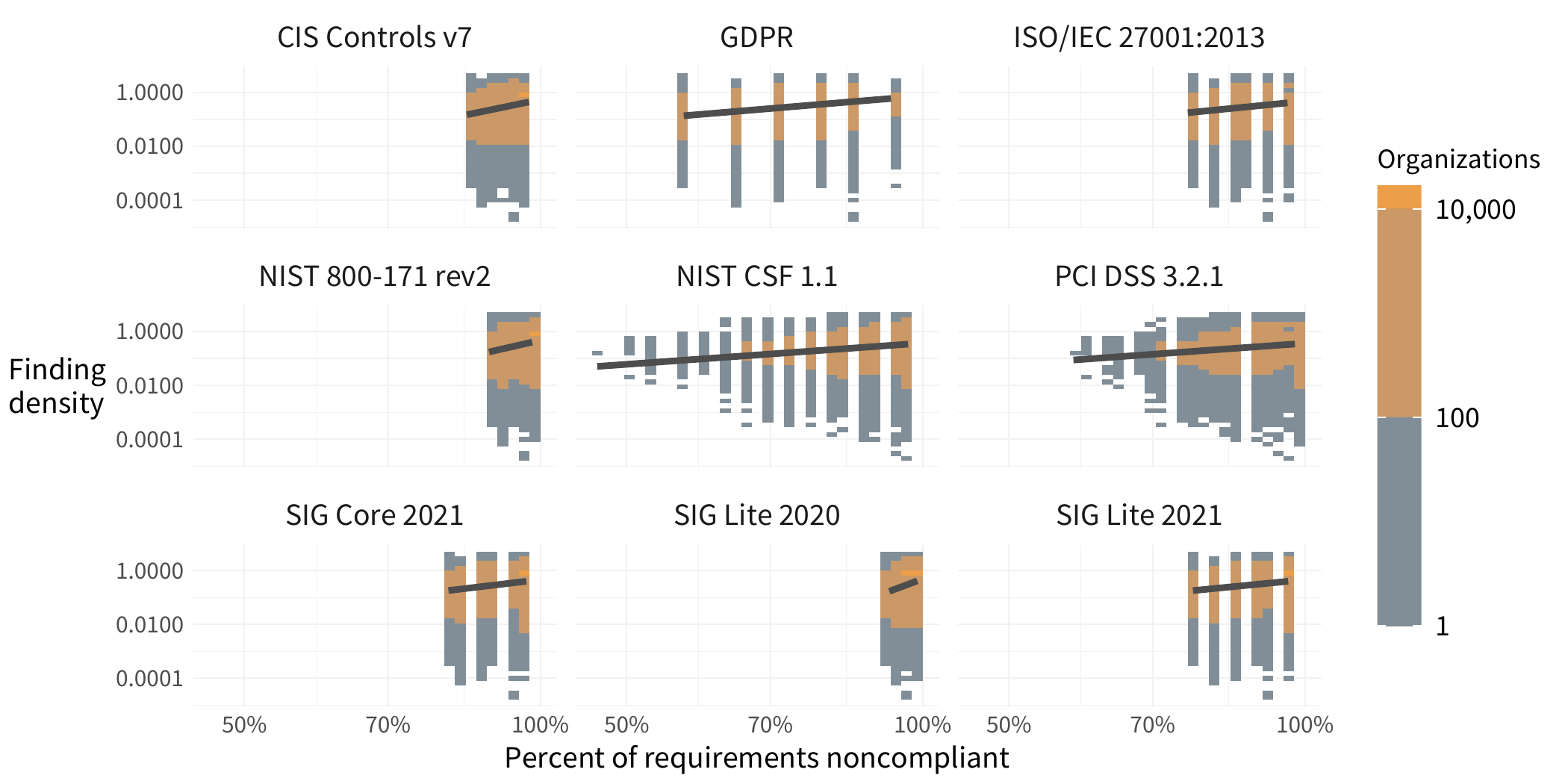
Broadly, as more requirements test as noncompliance there's an upward trend in finding density. Finding density increases with an increase in the percentage of noncompliant items within an organization. Finding density can also offer some insight into which requirements cause the most trouble within each compliance standard. Each standard contains a different hierarchy of requirements, we’ve simplified this down to each major category of requirements in these standards and show them in this chart.
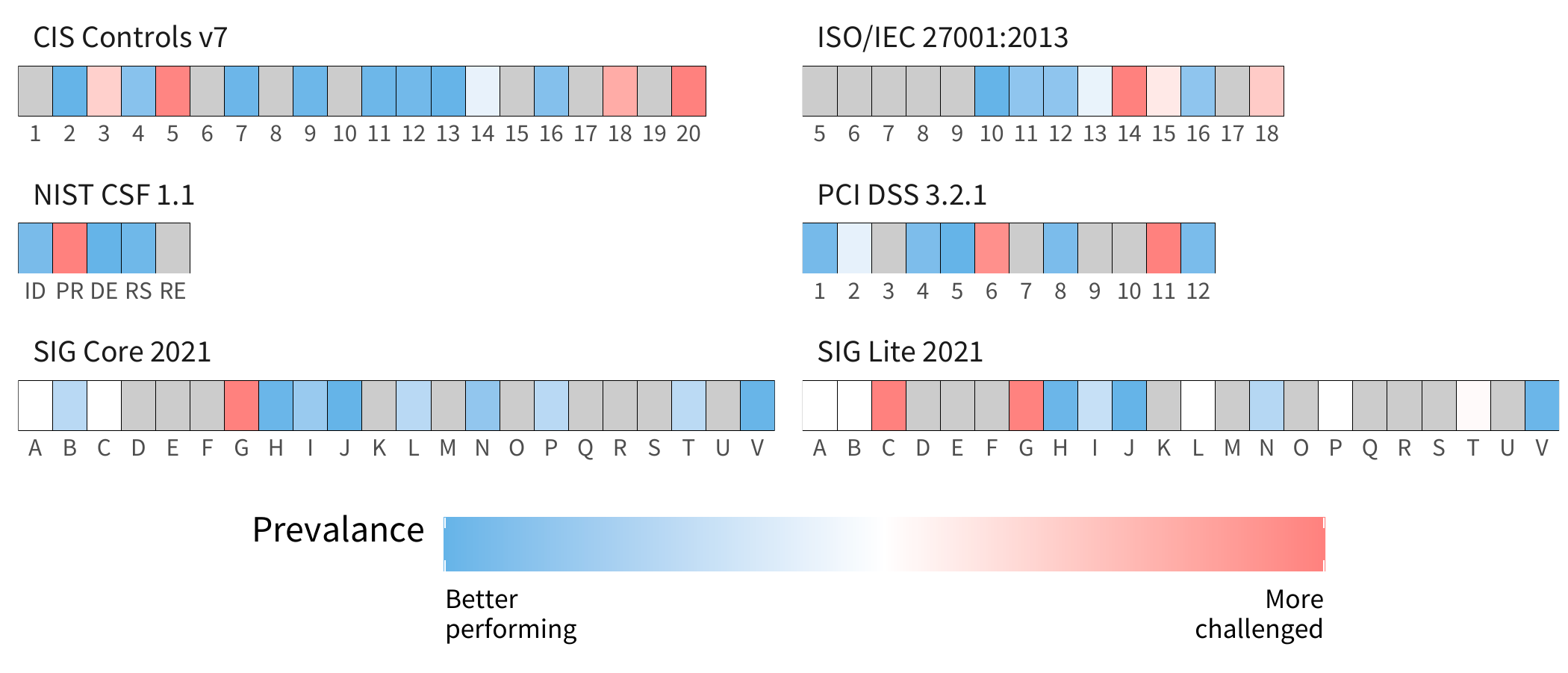
Now, let’s take a look at NIST CSF. The PR (Protect) requirement, with its extensive collection of technical measures (including patch management) seems to be the requirement that presents the most challenges. For the CIS Controls framework requirements 5 (Secure Configuration) and 20 (Penetration Tests and Red Team Exercises), tend to have the most challenges. Hopping down to PCI, it’s perhaps no surprise that the technical demanding requirements 6 (Develop and maintain secure systems and applications) and 11 (Test security systems and processes regularly) are the ones that give organizations the most trouble. ISO 27001 requirement 14 (Ensuring that information security is an integral part of information systems across the entire lifecycle) is the one that is most challenging.