You might wonder just how widespread the problem of unsafe services is. “Unsafe” refers to instances where companies exposed data storage, network admin, or remote access services to the internet. There are two ways of analyzing the data: The first looks at the proportion of internet-facing hosts running these services, and the second looks at the percentage of companies that expose unsafe services somewhere across their infrastructure.
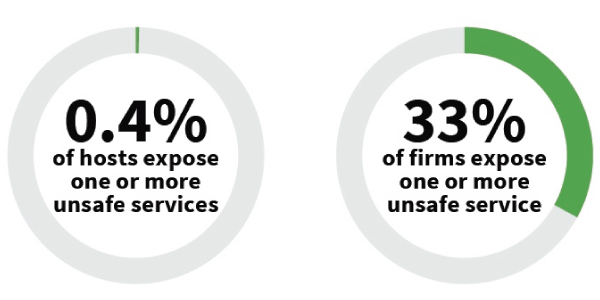
FIGURE 1: PERCENTAGE OF HOSTS (LEFT) AND FIRMS (RIGHT) EXPOSING UNSAFE SERVICES
Given the preponderance of errors we read about in other security reports, you might assume both categories tell a woeful tale. But our data shows that less than half a percent of commercial internet-facing systems expose one or more unsafe services. At first blush, this seems like everyone is doing OK. Keep in mind, though, that a half percent of millions of hosts is still a large number. Plus, each of these systems, if compromised, presents a potential foothold for gaining access to many others.
While the prevalence of unsafe services at the host level is relatively low, 33% of organizations expose one or more unsafe services across hosts under their control. That may seem lower than expected, depending on your perspective. But look at it like this—a full third of firms risk landing on attackers’ radar simply by virtue of exposing these services. In that light, it is well worth admins’ time to eliminate direct Internet access or deploy compensating controls for when/if such services are required.
At this point, you might be curious as to which of the services listed at the beginning of this report are most commonly exposed. Per Figure 2, datastores lead by a large margin. If that brings to mind all the exposed S3 buckets, databases, and other events that frequent the headlines, it should. A simple web search will tell you why direct internet access to database services should be prohibited or secured.2
Remote access and network admin services certainly have legitimate uses, but threat actors love to exploit them for illicit purposes. These services offer ne’er-do-wells direct paths to system consoles and datastores, which they can directly pilfer and use as staging points for tunneling deeper into their victim’s network. Thus restricting accessibility of those services to legitimate users (i.e., limiting to internal or partner IP space) is an essential practice.
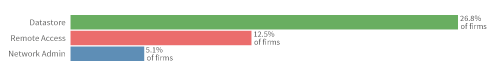 FIGURE 2: PREVALENCE OF UNSAFE SERVICES CATEGORIES EXPOSED BY FIRMS
FIGURE 2: PREVALENCE OF UNSAFE SERVICES CATEGORIES EXPOSED BY FIRMS
5.1% of firms 12.5% of firms 26.8% of firms Network Admin Remote Access Datastore
Examining which specific services are most frequently exposed in Figure 3, MySQL is clearly the biggest offender. Let’s just pause for a moment here to consider the seriousness of this. MySQL databases store data. Over 24% of companies expose one or more MySQL databases directly to the Internet. The only thing standing between a hacker and the data in the MySQL database is an authentication credential or a database vulnerability. So much for defense-in-depth...
And while we saw that 27% of unsafe services are datastores, two out of the top three fall in the remote access category. If exploited, RDP or PPTP (or any of the others) could provide easy entrance into an organization’s internal network. Needless to say, such doorways shouldn’t be advertised and open to the broader population of Internet users.
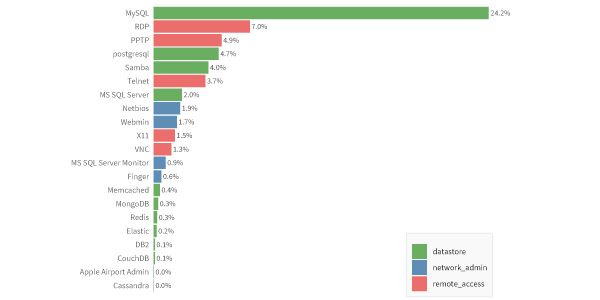
FIGURE 3: PREVALENCE OF UNSAFE SERVICES CATEGORIES EXPOSED BY FIRMS
Download the new report, Third-Party Security Signals to read the full findings from this exclusive research study.







