 By: Kelly White, Founder, RiskRecon, a Mastercard Company
By: Kelly White, Founder, RiskRecon, a Mastercard Company
Having been a cybersecurity practitioner for 25 years now, I have been around long enough to collect a few unfounded industry anecdotes. One of those that has been oft-repeated is, “The most secure company is the one that recently was breached.” The reasoning was that companies that recently experienced a material breach would naturally make the investments necessary to strengthen their security program to minimize the likelihood of such an event occurring again.
That tale isn’t true. Based on our analysis of the cybersecurity hygiene of victims of destructive ransomware attacks on the day of the attack compared with the cybersecurity hygiene of the same companies one year later, there is not much observable improvement. On average, a year after the event, many of the same and new critical software vulnerabilities are present in victim environments, unsafe network services remain invitingly open for criminals to compromise, and the communications encryption of many sensitive systems remains insecurely configured.
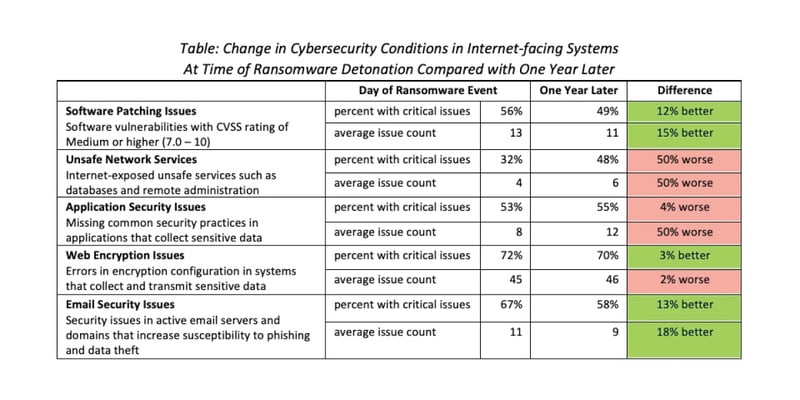 So, don’t assume that a recent victim of ransomware is getting their cybersecurity house in order. The data doesn’t bear it out. Looking at it on an industry level, half of the industries have worse cybersecurity hygiene one year after a ransomware event. As a risk practitioner, stick to your program. Stay after all the companies in your portfolio. Perhaps for those companies who have had a recent event, you should increase your assessment depth and frequency for multiple years.
So, don’t assume that a recent victim of ransomware is getting their cybersecurity house in order. The data doesn’t bear it out. Looking at it on an industry level, half of the industries have worse cybersecurity hygiene one year after a ransomware event. As a risk practitioner, stick to your program. Stay after all the companies in your portfolio. Perhaps for those companies who have had a recent event, you should increase your assessment depth and frequency for multiple years.
Click here to download the complete paper and get the full details on lessons learned from ransomware attacks.







