In October 2020, we will be releasing an update to our cybersecurity risk rating model founded on our platform's unique ability to automatically assess cybersecurity risk performance. In the coming weeks, we will be publishing a series of blog posts around this new methodology, including information on how this update can help to enhance your third-party security risk management program.
Is your cybersecurity risk management “good”, like a bank? Or is it poor, like a university? RiskRecon’s rating model is founded on observed real-world risk management practices, rather than being based on “expert opinion”, or one that is intentionally engineered to map ratings to past data loss events. It is based on analysis of entire industries in which those widely accepted to excel at managing risk (Banks) reflect the upper end of the ratings scale, and industries widely known to be very weak at managing risk (Universities) reflect the lower end of the ratings scale.
RiskRecon can clearly differentiate between enterprises and industries that manage risk well and poorly because of RiskRecon’s ability to not only determine the rate of issues and their severity within an environment, but also the value at risk for each system in which the issues exist. Of this unique capability, Jack Jones, Chairman of the FAIR Institute and co-founder of RiskLens stated:
“Far too much energy in information security is wasted on resolving issues that don’t matter. As the FAIR model promotes, effective risk management requires understanding the probable frequency and magnitude of loss; that depends on understanding asset value. I am really pleased to see RiskRecon bring the ability to automatically determine asset value to market.” [1]
Assessing Risk
Managing risk requires knowing 1) the rate of issues and their severity and 2) the value at risk for each system in which the issues exist. While identification of security issues and related severity is common, automatic determination of a system’s value at risk is not. RiskRecon analyzes both dimensions and folds them into the rating model.
Issues
RiskRecon discovers issues present in an enterprises’ Internet-facing systems and their operations through open-source intelligence and analytics. RiskRecon assigns each issue a severity rating of Critical, High, Medium, or Low using the Common Vulnerability Scoring System (CVSS). RiskRecon assigns its own severity rating for issues where a CVSS rating is not available.
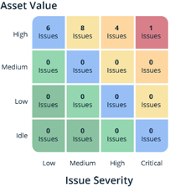
Knowing the rate of issues and their severity in an environment provides visibility into how effective an enterprise is at managing issues. However, knowing the issues does not reveal how well it manages risk. Consider two different organizations that operate the exact same number of systems, each system having the exact same data and functionality. Both environments have the same number of issues of the same severity, as shown in the graphic below.
Question: Which organization is better managing risk?
|
Company A |
Company B |
 |
 |
Answer: You cannot answer the question.
Why? Because you do not know the value at risk of the systems in which each issue exists. Do the issues exist in a brochure site that is rarely visited? Do the issues exist in a customer transaction portal where they are authenticating and submitting sensitive data? This kind of information is necessary for assessing risk. Enter RiskRecon’s ability to automatically determine asset value.
Asset Value
RiskRecon automatically determines the value at risk of every system it analyzes. Combined with knowing the rate of issues and their severity within an enterprise, it enables RiskRecon to assess the quality of risk management.
Question: There are two systems, each with the same issue – invalid HTTPS certificate subject. Which issue is higher risk?
Answer: It is impossible to answer without additional information.
Let’s add some more information.
Question: There exists a brochure site and a banking portal, each with the same issue – invalid HTTPS certificate subject. Which issue is higher risk?
Answer: Of course, the higher risk issue is in the banking portal.
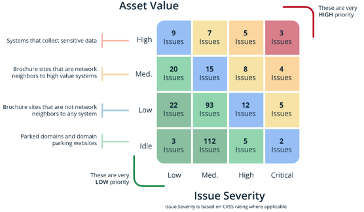
RiskRecon determines the value at risk (asset value) of a system based on deep analytics of the code, content, and configuration of each Internet-facing system. Through these analytics, RiskRecon discovers the types of data each system collects. The primary analytics are focused on identifying the form fields of every web page and using machine learning models to determine the types of data each collects. Systems that collect sensitive data such as user credentials, email addresses, credit card numbers, and so forth are rating as High asset value. Systems that collect no sensitive information are given a lower rating. RiskRecon uses other characteristics for determining asset value which are not described here.
Risk Prioritization
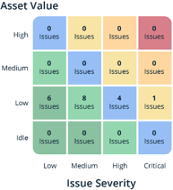
Combining issues and their severity with the asset value information we get a much more colorful picture through which we can assess risk. To illustrate this point, let’s revisit Company A and Company B. Remember, they operate environments of the same size the provide the exact same functionality. They have the same security issues.
Again, the Question: Which organization is better managing risk?
|
Company A |
Company B |
|
|
|
Answer: Company B manages risk better.
With only knowledge of the count and severity of issues it is impossible to tell which better manages risk. However, adding the dimension of asset value changes the entire game. The issues of Company A all exist in systems that process sensitive data. In comparison, Company B only has issues in low-value brochure systems.
You may download the full white paper here or feel free to request a product demonstration to gain a deeper understanding of how the new risk rating model can help you understand and act on third-party cyber risks.
[1] https://www.prnewswire.com/news-releases/riskrecon-invents-ground-breaking-asset-risk-valuation-algorithms-transforming-how-enterprises-manage-third-party-cyber-risk-300730415.html