 By: Jonathan Ehret, Vice President of Strategy & Risk, RiskRecon
By: Jonathan Ehret, Vice President of Strategy & Risk, RiskRecon
The onset of the COVID-19 pandemic has brought many changes to our world. Schools are closed, businesses are shuttered, and those that do remain open have largely moved their workforce to work from home. To accomplish this monumental feat of moving the workforce remote in short order, many organizations have been forced into an all-hands-on-deck scenario where the staff is being asked to perform roles outside of their norms. Security professionals are not immune to this. In a recent study published by (ISC)², 47% of security professionals indicated that they were being asked to perform non-security functions during the pandemic. Essentially, companies have been put in a situation where they are prioritizing other functions over security just to keep the business operating.
Never one to miss the opportunity to make the most of a bad situation, the bad actors are doubling down on their efforts while security professionals are being sidetracked into other roles. Our team here at RiskRecon started analyzing the data that we collect, and we saw plenty of evidence to support this assertion.
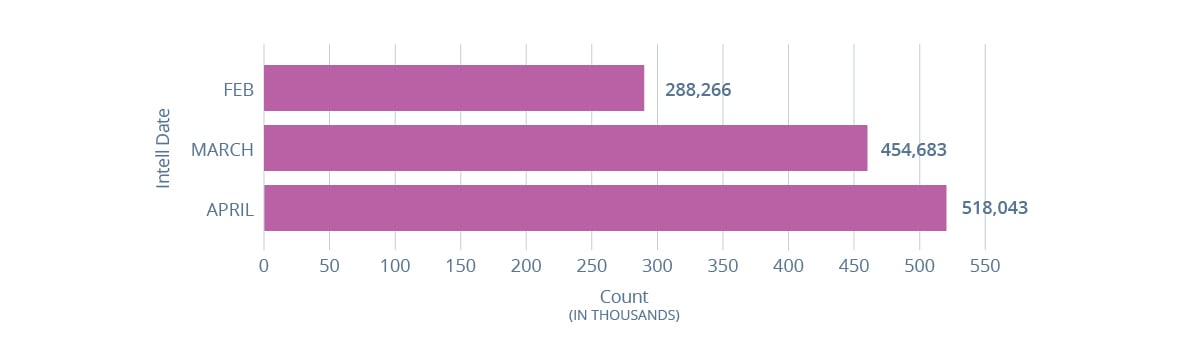
Phishing Sites – Total number of phishing sites observed operating daily by month
The number of phishing sites RiskRecon observed operating globally increased by 79% for April 2020 compared to February 2020.
This metric is in line with anecdotal evidence and other data that suggests phishing activity has increased during the COVID-19 era.
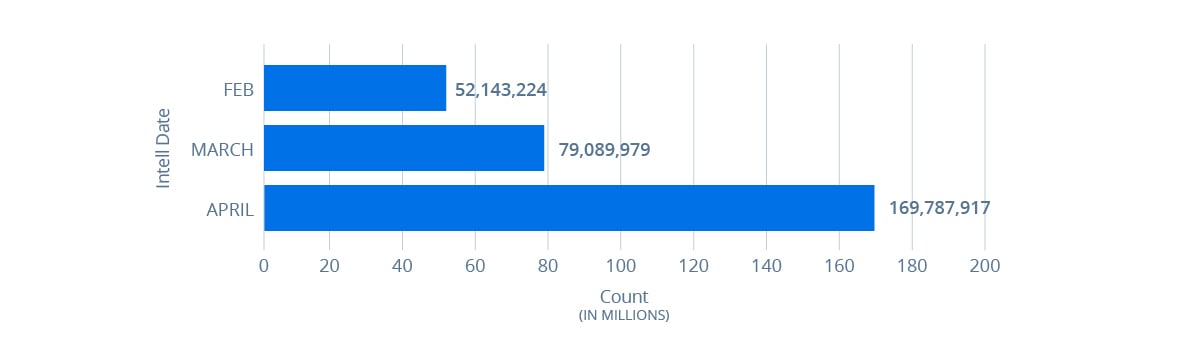
Bot Activity – Total number of bots observed operating daily by month
The number of bot infected hosts RiskRecon observed operating globally increased by 225% for April 2020 compared to February 2020.
This metric is within the context of the COVID-19 era mass rapid migration to work from home in which many more new systems are coming online, not having the benefit of internal network security infrastructure, and increased targeting by miscreants.
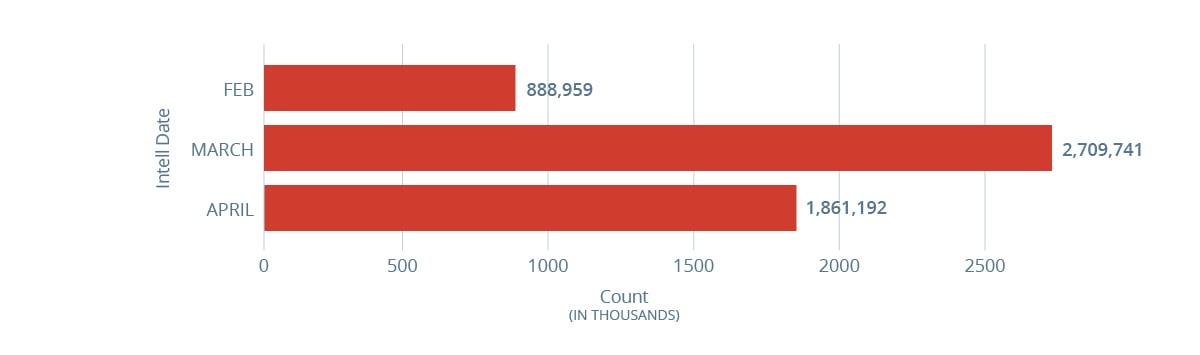
Bot Controllers – Total number of botnet controllers observed daily by month
The number of botnet controllers RiskRecon observed operating globally increased by 109% for April 2020 compared to February 2020.
This metric is within the context of the COVID-19 era mass rapid migration to work from home in which miscreants increased COVID-19 and work-from-home-exposed systems.
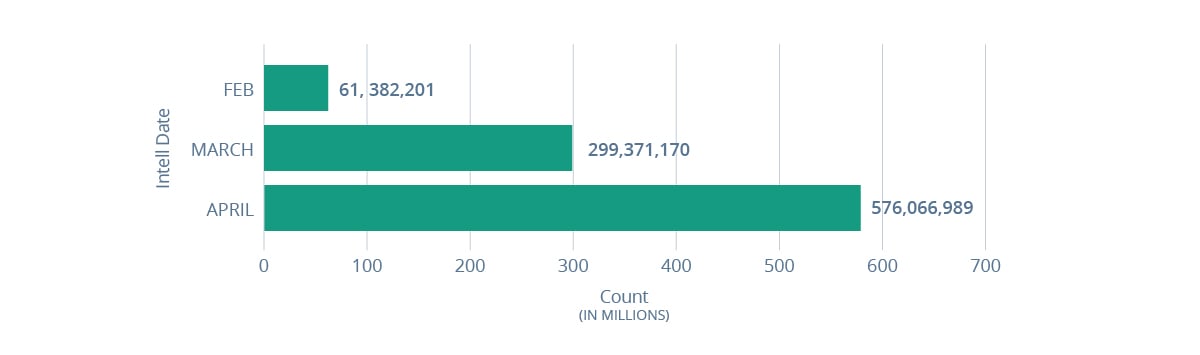
Darknet Probing – Total number of systems probing darknets daily by month
The number of probes to darknet infrastructure RiskRecon observed globally increased by 838% for April 2020 compared to February 2020.
Darknet systems are systems that passively reside on the Internet that provide no reason for anyone to interact with. As such, any connection to a darknet system is an indication of active foot printing and probing, a leading indicator of forthcoming attacks.
All of this puts third party risk practitioners in a difficult spot. First, they may very well be a part of the 47% being asked to perform new tasks and they simply don’t have the time to assess and monitor their vendors. Second, what they may know about the security posture of their vendors may not be relevant any longer.
For instance, perhaps organizations performed a review pre-COVID where a vendor stated that they did not allow remote working and had no mechanism in place to facilitate it.
When the pandemic started, they were forced to allow it hastily and perhaps without the proper security controls in place. The result is a situation where your data no longer resides on an endpoint with adequate protection in place. Or, perhaps the vendor’s security staff tasked protecting your data is a part of that 47% being asked to do tackle other priorities.
Ultimately, the uptick in bad actor activity coupled with staffing changes in your organization and security changes at your vendor can spell bad news for your hosted data.
For maximum situational awareness, third party risk practitioners need to utilize all the tools in their arsenal to keep tabs on what is happening with their vendors. A once-yearly security questionnaire alone will not suffice at a time like this. Rather, a layered approach of the following will help practitioners triage their vendor lists and focus appropriate attention where it’s needed:
- data from a questionnaire (for general context)
- data from a continuous monitoring tool (for current security posture changes and potential threats)
- the simple knowledge of knowing what data a vendor has from your organization and how much of it
In The Art of War, ancient Chinese military strategist Sun Tzu said that “If you know the enemy and know yourself, you need not fear the result of one hundred battles.”
As TPRM practitioners, we should already know ourselves, and with the right strategy of tools and tactics, we can do our best to know our vendors. Hopefully, that results in a winning approach.
1 “(ISC)² Survey Finds Cybersecurity Professionals Being Repurposed During COVID-19 Pandemic.” (ISC)² Survey Finds Cybersecurity Professionals Being Repurposed During COVID-19 Pandemic, 28 Apr. 2020, www.isc2.org/News-and-Events/Press-Room/Posts/2020/04/28/ISC2-Survey-Finds-Cybersecurity-Professionals-Being-Repurposed-During-COVID-19-Pandemic.







