Sponsored by RiskRecon, a Mastercard Company, and conducted by Ponemon Institute,1,162 IT and IT security professionals in North America and Western Europe were surveyed for a new study, Data Risk in the Third-Party Ecosystem. All participants in the research are familiar with their organizations’ approach to managing data risks created through outsourcing. Over the coming weeks, we will examine and discuss the responses in the study.
In this blog, we dive into the realities of third-party risk management programs through the data collected in the study.
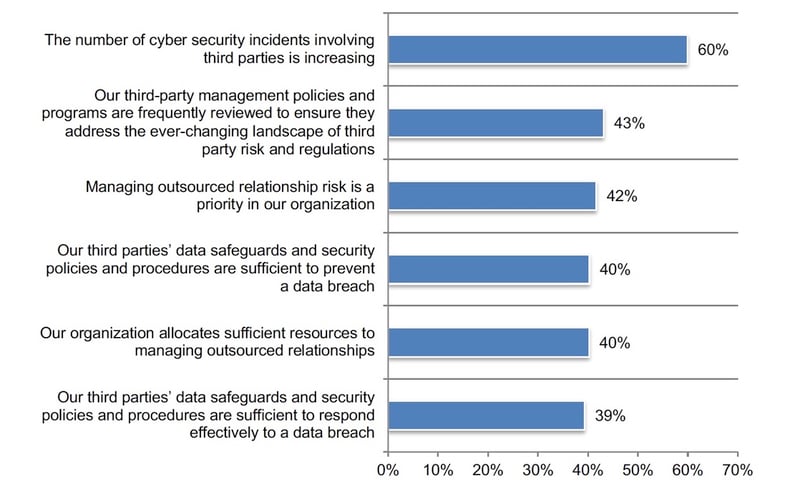
Organizations believe they are at risk because of the failure to take appropriate steps to safeguard sensitive and confidential information shared with third parties. Figure 1 presents a list of reasons respondents believe are the causes of ineffectiveness in detecting, minimizing, and mitigating third-and-Nth party risks. Only 39 percent of respondents say their third parties’ data safeguards and security policies and procedures are sufficient to respond effectively to a data breach. Only 40 percent say they are sufficient to prevent a data breach.
According to the research, organizations also need to improve their third-party risk management practices. Specifically, only 42 percent of respondents say managing outsourced relationship risk is a priority, only 40 percent of respondents say there are sufficient resources allocated to the management of risks and only 43 percent of respondents say there is a frequent review of third-party risk management policies and programs to ensure they address the ever-changing third- party risks and regulations.
Figure 1. Perceptions about vendors’ security policies and procedures
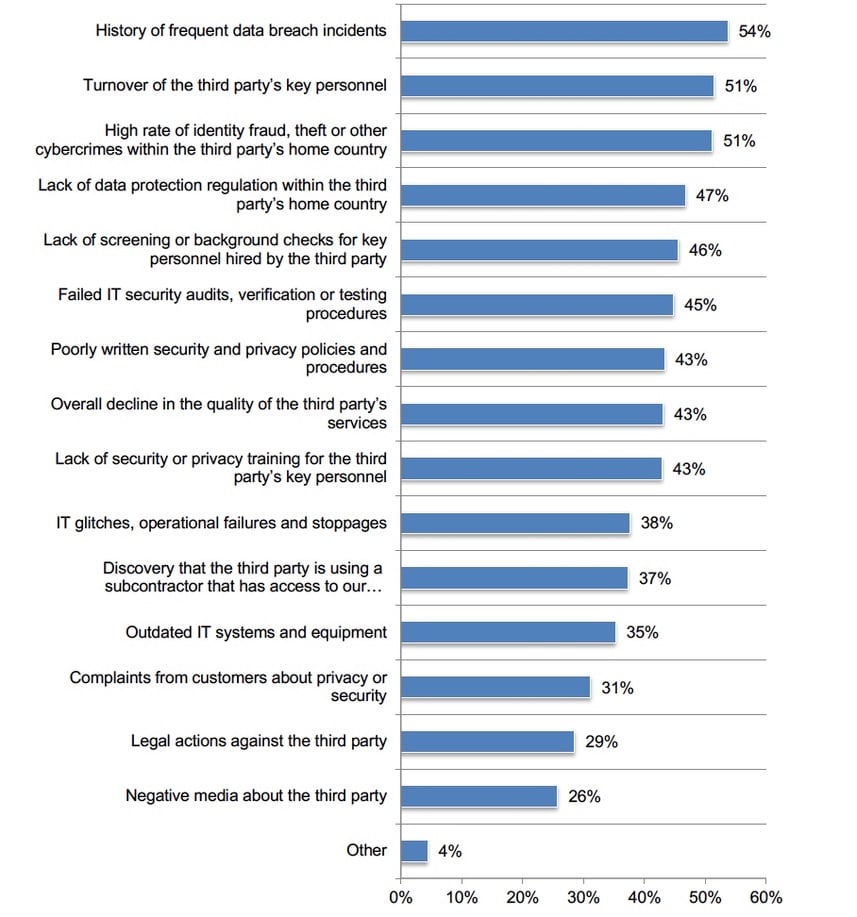
A history of frequent data breach incidents is the top indicator of third-party risk. Fifty-eight percent of respondents say their organizations’ third-party management program defines and ranks levels of risk. Sixty-two percent of respondents say risk levels are updated every six months (33 percent of respondents) or annually (29 percent of respondents). Figure 2 presents an extensive list of indicators of third-party risk. Turnover of key personnel and a high rate of cybercrimes in the third party’s home country are risk indicators according to 51 percent of respondents.
Figure 2. What are indicators of risk?
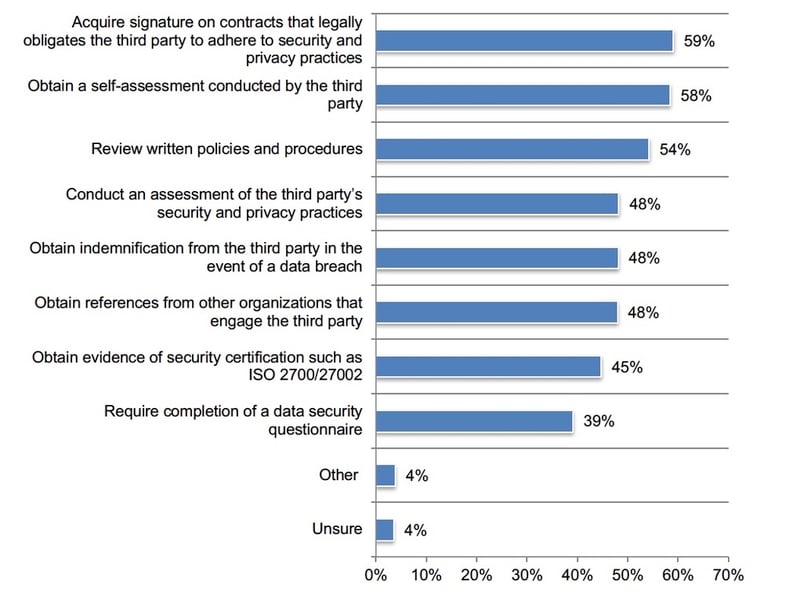
Companies rely on contractual arrangements to evaluate third parties. Only 36 percent of respondents say that before starting a business relationship that requires the sharing of sensitive or confidential information their company evaluates the security and privacy practices of all vendors.
Figure 3 shows the steps taken to perform such an evaluation. Fifty-nine percent of respondents say their organizations acquire signatures on contracts that legally obligate the third party to adhere to security and privacy practices followed by a self-assessment conducted by the third party (58 percent of respondents). Only 39 percent of respondents say the completion of a data security questionnaire is required.
Figure 3. How do you perform this evaluation?
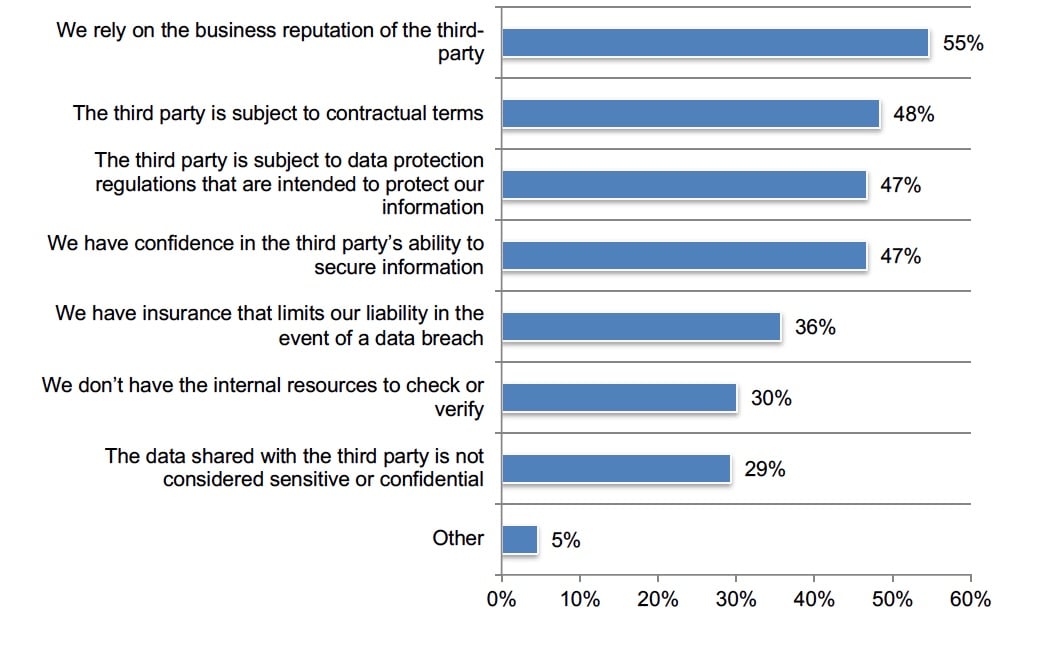
Reliance on business reputations and contracts is the primary reason for not performing an evaluation of potential third parties. As shown in Figure 4, about half (47 percent) of respondents say they do not conduct assessments because of third parties’ requirement to comply with data protection regulations or because they have confidence in the third party’s ability to secure information.
Figure 4. Reasons for not performing an evaluation
 Companies are not monitoring the privacy and security practices of third parties. Fifty percent of respondents say their companies do not monitor the security and privacy practices of vendors with whom they share sensitive or confidential information or are unsure.
Companies are not monitoring the privacy and security practices of third parties. Fifty percent of respondents say their companies do not monitor the security and privacy practices of vendors with whom they share sensitive or confidential information or are unsure.
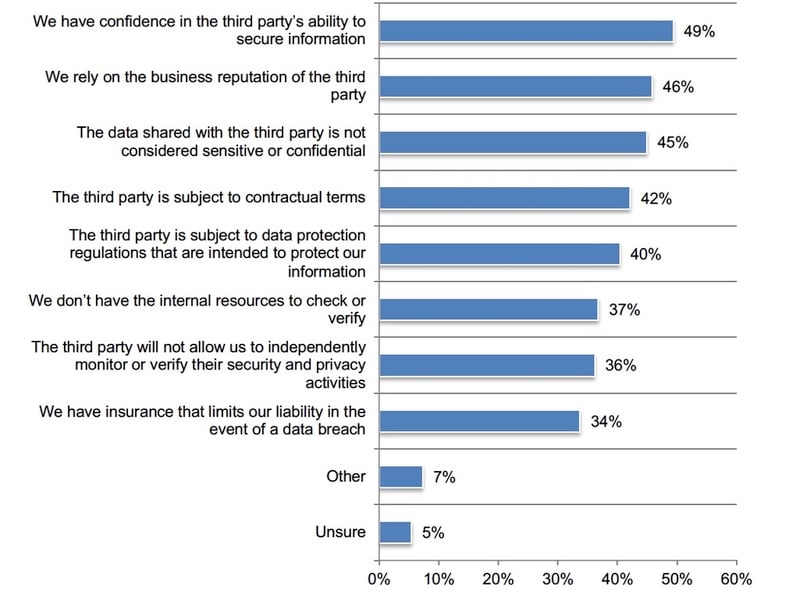
As shown in Figure 5, the primary reasons for not monitoring are: confidence in the third party’s ability to secure information (49 percent of respondents), reliance on the business reputation of the third party (46 percent of respondents), data shared with the third party is not considered sensitive or confidential (45 percent of respondents) and contracts (42 percent of respondents). These are similar to reasons for not evaluating third parties before engaging them.
Figure 5. Reasons for not monitoring security and privacy practices
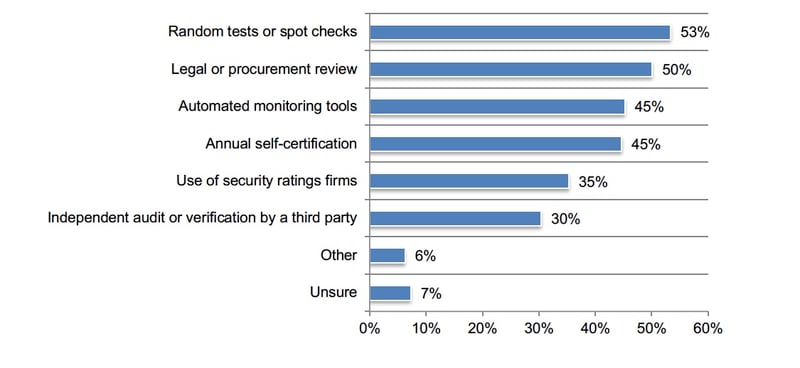
Fifty percent of respondents say their companies monitor the security and privacy practices of third parties to ensure the adequacy of these practices. Figure 6 reveals that 53 percent of respondents say their organizations conduct random tests or spot checks. Only 30 percent of respondents say they depend upon independent audits or verification by a third party.
Figure 6. Third-party monitoring procedures are used to ensure the adequacy of security and privacy practices