Knowing the prevalence of IoT devices and where they are most likely to be found is a good place to start as we continue to examine how IoT devices are impacting enterprise organizations. But the next question is to ask is what types of devices they are and what can be determined about their level of security or insecurity. After all, it may be the intent to have the device accessible from anywhere, and it may be running secure software. Let’s interrogate those possibilities.
First what types of devices are out there? In terms of the Internet-facing enterprise infrastructure assessed by RiskRecon, it’s mostly cameras (54%), “management interfaces” (30%), and printers (16%). For that middle category of devices, the waters are a bit murky. These management interfaces are running generic IoT software such as the “Boa Web Server for IoT,” but it’s difficult to determine exactly what they are. In the case of the Boa example, it’s a platform on which to build IoT device functionality but may not immediately reveal anything about the underlying device itself.
FIGURE 1: TYPES OF FINDINGS ASSOCIATED WITH EXPOSED IOT DEVICES
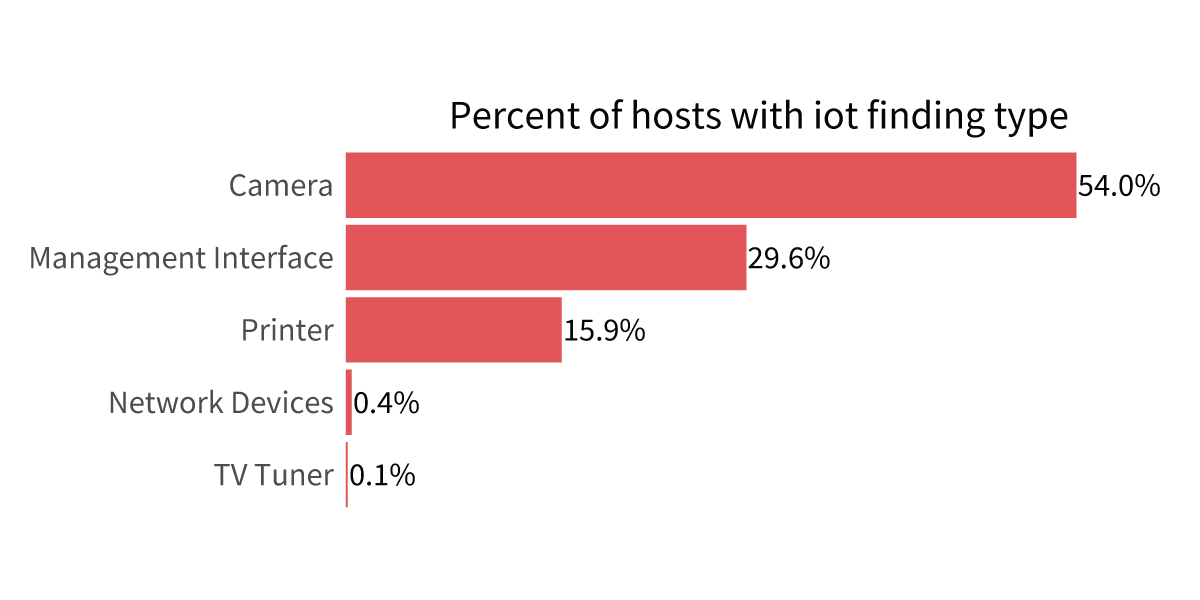 Cameras and printers are self-explanatory. The ‘Management Interface’ category consists of myriad devices using various development platforms.
Cameras and printers are self-explanatory. The ‘Management Interface’ category consists of myriad devices using various development platforms.
IoT software is not exactly known for being a bastion of security, and we find confirmation of that here. Nearly 86% of IoT devices have security findings rated as critical. To put that in perspective, only 2% of non-IoT hosts have critical findings. That means that the vast majority of IoT devices have flaws that are likely to result in serious compromise if exploited.
FIGURE 2: PROPORTION OF IOT DEVICES WITH CRITICAL SECURITY FINDINGS
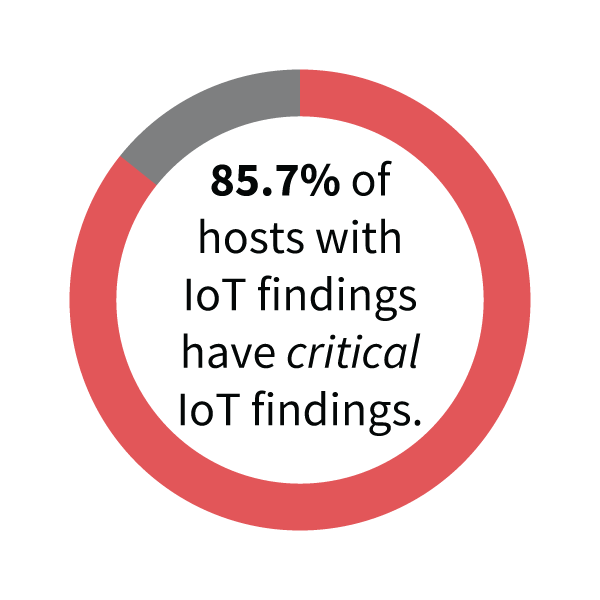 The vast majority of security issues affecting IoT devices are rated critical. Non-IoT devices have a critical finding rate of 2%.
The vast majority of security issues affecting IoT devices are rated critical. Non-IoT devices have a critical finding rate of 2%.
The takeaway here, is that IoT devices are extremely vulnerable to threats and pose massive risks to firms across the globe, so the data being presented here should be ignored at your own peril.
In the final blog in our series on the cyber risk posed by exposed IoT devices in the enterprise, we will look at the correlation of IoT findings with other cybersecurity issues. You can also download our IoT device study to get the full details of our research.