Continuing to explore the key findings from our latest research report, Third-Party Security Signals, this post will look at how you can put the findings from this report into use to enhance your third-party cyber risk management program.
The services discussed in the report form the foundational fabric of network infrastructure in the modern era. It would be nigh impossible to maintain IT-dependent business operations without them. That said, such services pose a serious threat when exposed directly to the internet without security controls to shield them from unauthorized use. Furthermore, we’ve shown that the organizations that tend to be laxer in controlling these services also tend to exhibit wider security issues.
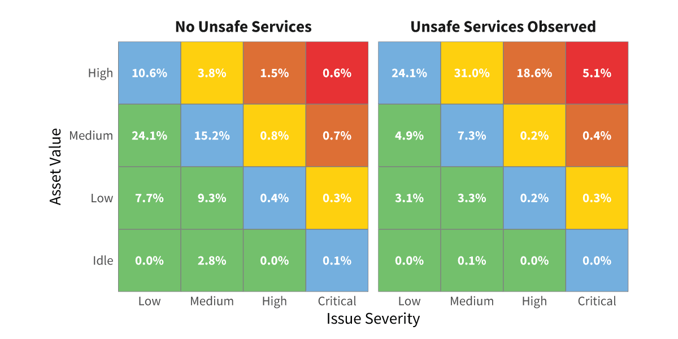
The figure below presents a view of this topic, unsafe network services, through the lens of RiskRecon’s risk priority matrices. The upper right is where your eye should be drawn. Assets rated as high-value support sensitive and/or critical business functions. That’s why the nearly 9x jump in critical security issues among high-value servers running unsafe services is a major red flag that you don’t want waving prominently across your infrastructure and third parties.
You may be wondering how you can take action from the findings within this report. Below is a description of how three key areas in cybersecurity can utilize and apply the research results.
Enterprise Risk Management
RiskRecon’s continuous IT profiling and security analytics give you intimate visibility into your Internet-connected systems, where they’re hosted, what their configuration is, and if it meets security requirements. RiskRecon’s analytics discover the IT profile of every system and analyze each one against 41 security criteria like those examined in this report. Combined with RiskRecon’s ability to automatically determine asset value at risk, your teams can easily identify issues, prioritize response, and act efficiently.
Third-Party Risk Management
Performing third-party assessments without objective data put you at a huge disadvantage, leaving you only the ability to review unsubstantiated questionnaire answers. Which of your third parties are exposing unsafe network services? Do your vendors patch software vulnerabilities? RiskRecon objectively verifies vendor cybersecurity risk performance, enabling your analysts to see how well your vendors implement and operate their risk management program.
Mergers and Acquisitions
Know exactly what you’re acquiring. RiskRecon delivers objectively gathered information about any company’s information security program. You’ll gain full knowledge of the environment and risks of an acquisition beforehand, enabling you to establish merger costs and potential liabilities with the Board and enter into the M&A process with greater peace of mind.
Download the new report, Third-Party Security Signals: Exposing the reality of unsafe network services, to read the full findings from this exclusive research study and find out how you can apply these findings to your third-party risk management program.







