A couple of months ago RiskRecon partnered with the data scientists at the Cyentia Institute to begin measuring the ripple effects that can extend from a single security incident to impact many organizations beyond the initial victim. The goal was to start to gain a greater scientific understanding of the true financial impacts associated with third-party risk when breaches strike.
The principle behind cyber ripple events is one that many understand implicitly. But until our report there's been little quantitative evidence to back up what rational minds have already deduced:
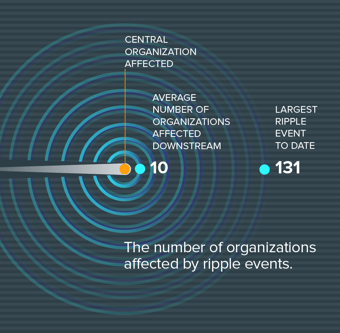
The more organizations expand their digital footprint across numerous third-party and Nth-party connections, the more they increase their risk of being impacted by downstream data breach consequences
We recently interviewed the data scientists (David Severski and Dr. Wade Baker) who did the analysis for our report, so that we can shed some light on where they got their data, how they developed their models, and where limitations in the data set might be hiding even more evidence of the cyber ripple effects in play today.
RiskRecon: Can you tell us what the impetus was behind digging into the analysis of the Cyber Ripple report?
Wade Baker: As we've worked through our Risk Surface report series with RiskRecon we've been showing all of the interconnections between organizations and the exposures involved. For us, that left us with an open question: Does the higher rate of severe exposures in cloud-based assets matter? Does it have any financial ramifications?
And so, it set us looking for an incident dataset with which to examine and vet some of the financial impacts of things that we were seeing in the first couple of reports.
RiskRecon: And this is what led you to the Loss Insight database from Advisen, an insurance data provider. You saw this as one of the most comprehensive sources of publicly available information about security-related incidents. Can you explain a little bit about the nature of events coming from that feed?
David Severski: Broadly speaking, the event categories come into two categories. There are cyber breaches and there are privacy-related events. Those are the two big buckets, and those account for almost all of the events. There are a substantial number of privacy-related events in there, on the order of 40% to 45%. We included both of those types of events, so the incidents included privacy misuse, privacy disclosure, or the broader category of "cyber events," which would include hacking, denial of service, inadvertent disclosure, and so on.
Wade Baker: Just being fully honest with you, coming from writing about breaches and analyzing them from the DBIR legacy, I'm used to having a lot more descriptive information about how the incidents went down. In the Advisen data set, that's just not the focus there. There are no distinguishing incidents caused by weak credentials versus SQL injection, or anything like that.
It was really broad, semi-vague categories that they put in there. So, there were a lot of events where nobody's systems necessarily got hacked, but information was exposed or released
David Severski: But we do feel confident in including those into this ripple conversation because when we're talking about privacy disclosures, that really goes to the heart of what we're talking about with these third-party, and Nth-party relationships.If you are giving access to your data, to a vendor, and they, in turn, give them access to their vendors, and so forth, and that data is 'Oops!' accidentally posted, that has real consequences upon the upstream and downstream organizations.







