 As organizations examine their vendor relationships with an eye toward cyber risk, there's rarely a single factor that would tell a decision-maker that any given third-party is too risky to do business with. Risk is contextual, there are always positive business trade-offs for maintaining certain relationships, and many risk factors can be countered with timely mitigation and management.
As organizations examine their vendor relationships with an eye toward cyber risk, there's rarely a single factor that would tell a decision-maker that any given third-party is too risky to do business with. Risk is contextual, there are always positive business trade-offs for maintaining certain relationships, and many risk factors can be countered with timely mitigation and management.
Nevertheless, certain technical indicators can serve as very valuable red flags for enterprises seeking to actively manage the risk posed by their portfolio of third-party vendors. There are some security measures or controls that are so fundamental—and sometimes so easy to enact—that when they're missing the gap is usually symptomatic of much deeper cybersecurity failures.
We undertook a new research project utilizing the RiskRecon platform for millions of web scans and worked with the data scientists from Cyentia Institute to examine the findings. The findings indicate that adherence to the latest TLS encryption protocol standards may well be one of these cybersecurity litmus tests. The study's data shows that when organizations are missing the latest TLS protocol, they're also highly likely to be missing other critical cybersecurity controls as well.
Encryption of sensitive personal and financial information exchanged over the internet is table stakes for online security today, and the TLS 1.2 protocol offers the most secure route to pay those stakes. Previous versions of TLS and its precursor SSL are vulnerable to highly publicized flaws and are very exploitable by criminals seeking to carry out man-in-the-middle attacks and other assaults on sensitive information. This is why regulators and standards bodies alike—everyone from the Payment Card Industry Security Standards Council to National Institute for Standards and Technology—have all worked to mandate that operators of web servers are using TLS 1.2 by the end of the year.
The good news is that TLS 1.2 is fairly easy to configure and update compared to other harder tasks necessary for maintaining solid security hygiene. And the examination by Cyentia Institute of unique scan data from millions of web servers around the world shows that the majority of the Internet has already made the shift to TLS 1.2.
However, further examination of the numbers show that a significant number of web servers are still missing TLS 1.2—many of which deal in sensitive data for major organizations around the world.
Furthermore—and this is important for those tasked with managing risk across their vendor portfolio—the data indicates that this TLS status makes a good stand-in metric to assess these organizations' overall security posture. When an organization doesn't fully implement TLS 1.2, then it is also 70% more likely to exhibit more serious security findings within its network.
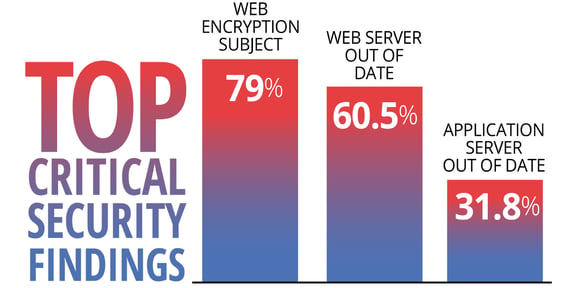
Some of the negative findings the report found to correlate with out-of-date TLS protocol use included heavy use of expired TLS certificates and other weak protocols, out-of-date web servers and application servers, out-of-date operating systems, and bad HTTP security headers. Approximately 67% of servers running older TLS versions also had some kind of patching problem present.
The relationship between TLS and other poor security practices is correlational rather than causational. Simply updating the TLS protocol isn't going to fix everything else. However, the absence of something so simple can point to greater problems under the surface.
The study we've done shows that sometimes the simplest security tests can offer up a great gut-check as to how an organization is doing when it comes to handling the security basics. If the organization passes these simple tests, more digging may be warranted. But if they can't even pass these ones then all signs point to trouble ahead. If third-party risk management stakeholders see this kind of red flag, there may be further action warranted.
Download our latest research report now to see the full results of the study and learn about the critical security areas that could be impacted by a lack of TLS 1.2 support.







