This article continues our series on a recent research report, that examined nearly 50,000 security assessments to better understand the cybersecurity status of B2B relationships.
In this blog, we look at a comparison of the security posture of first and third parties. As you might suspect, these partnerships are not always productive. Researchers from Cyentia Institute leveraged RiskRecon’s continuous security assessments of organizations’ internet-facing systems and related intelligence. The main interest is to understand how balanced these business relationships are from a cyber risk perspective. We’ll explore a few different ways of assessing security posture, including prior breaches, ratings, and the density and type of findings.
Breaches of Third Parties
Beyond continuously monitoring cybersecurity hygiene, RiskRecon analysts catalog breach events occurring in organizations around the world. Analysts source data loss events from channels such as public media, regulatory filings, and dark web monitoring. We published a study analyzing 10 years of incidents discovered through these methods, which provides in-depth information.
We’ll leverage that breach signals intelligence here to examine the “nearness” of security incidents within third-party relationships. And just like your rearview mirror warns: breaches are closer than they may appear. Every primary organization in our sample has at least one vendor in their portfolio with a detected breach in the preceding 36 months.
That stat certainly has some shock value, but it doesn’t do a lot to inform third-party risk management decisions. Knowing the proportion of vendors with breaches would be a lot more useful. So, let’s do that. 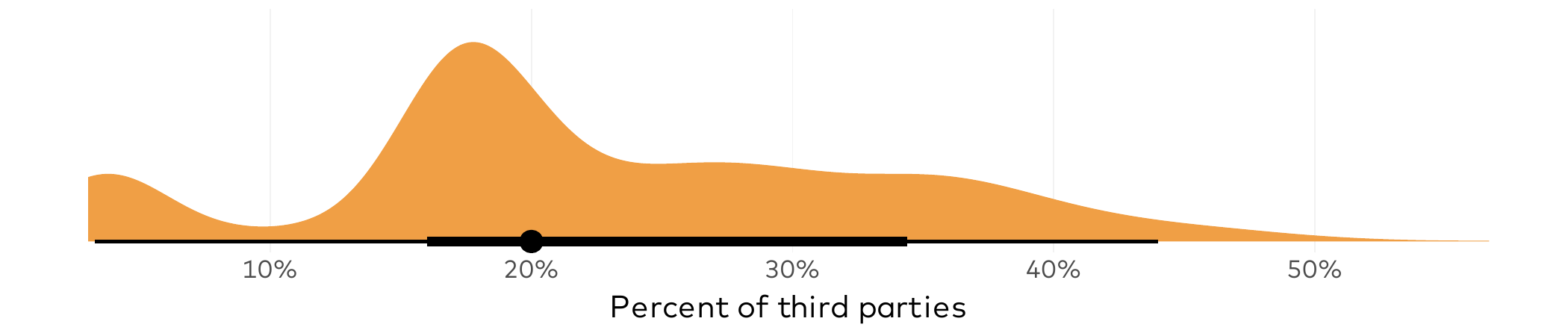
Percent of monitored third parties with probable breaches in the last 36 months
About 20% of the third parties in a typical organization’s vendor portfolio showed signs of experiencing a breach in the preceding three years. As seen in the figure above, there’s quite a bit of variation among firms on that proportion, ranging from 5% to over 50%. Breaches of third parties under management doesn’t mean the source organization was harmed in any way, of course. But there’s presumably a risk-relevant reason those firms were being monitored through a platform like RiskRecon. Most third-party risk management teams would like to see that ratio as low as possible.
Since we’re exploring the concept of security equity in B2B relationships, we found it prudent to widen the spotlight to cover not just third parties but also the first-party firms monitoring them. Which party is more prone to breaches? To answer this, we examined the historical breach information collected on both parties in each of the 50,000+ relationships.
In 14% of those relationships, we found evidence that both parties experienced a breach within the preceding 36 months. Third parties were the only side breached in 45% of partnerships, while first parties were the sole breached entity 41% of the time.
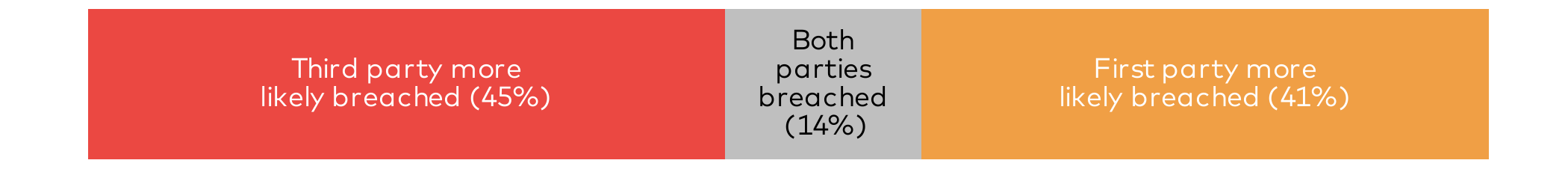
Comparison of historical breaches between between first and third parties
On the surface, that seems remarkably equitable. Though it probably doesn’t feel that way if you’re in a relationship where the other party has a bad track record, and yours is a clean slate. Looking at it from that perspective, 86% of B2B relationships involve parties with imbalanced breach histories (one’s had a breach, while the other hasn’t).
You can download the full report here to get access to all of the key learnings from our research. Additionally, if you would like to gain insight into the cybersecurity hygiene of the vendors in your ecosystem, you can get a free 30-day trial of the RiskRecon platform.
Stay tuned for the next piece in our blog series on Balancing Third-Party Risk.