In May of 2019, the American Medical Collection Agency (AMCA) disclosed a breach of its systems that compromised the personal information of over 24 million individuals. Most of the individuals affected had no direct relationship with AMCA; they provided their data to various other entities and those entities sent the data to AMCA for debt collection. Even though only AMCA’s systems were compromised, those other organizations were caught up in the fallout from the breach.
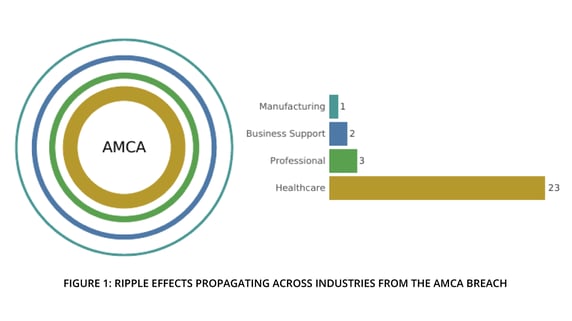
Events like this happen all too often and there’s nothing particularly remarkable about the breach itself. We call these Ripple Events. It’s the ripples propagating outward from AMCA to other firms (and that also crashed back on AMCA) that make it worthy of an example.
In our recent research report, RiskRecon and Cyentia Institute, partnered together to examine the affect of multi-party cyber incidents on organizations downstream from the initial breach. The dataset we examined records 29 organizations1 that have suffered known loss events in the wake of the AMCA breach. We don’t want to take the ripple metaphor too far, but it is a nice way to conceptualize and visualize these events. Figure 1 shows the central victim in the center of the incident with the ripple effects spreading outward across other sectors. The bars on the right give a count of organizations affected by those ripples within each sector.
Letters were sent by several senators to AMCA and multiple companies impacted by the breach, stating concerns about their supply chain management and third-party monitoring processes2. As further evidence of downstream liability, several of these entities face costly lawsuits and investigations. These cascading events caused AMCA’s parent company to file for bankruptcy, stating “enormous expenses that were beyond the ability of the debtor to bear3. ” From this example, we see that multi-party loss events affect not only the central victim firm, but surrounding third parties as well (not to mention the millions of individuals affected). Not all multi-party incidents have a clear single central organization, however.
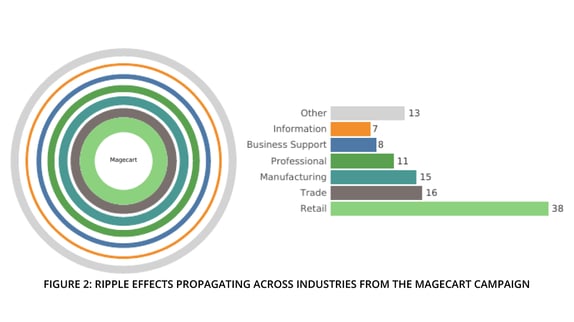
One of the larger examples in our dataset (in terms of affected parties) centered around the cybercriminal collective known as Magecart that infamously hacked Ticketmaster in 2018. Although the breach is often attributed to Ticketmaster, the merchant was not compromised directly. Two third-party suppliers of plugins integrated into Ticketmaster’s website for payment processing were the source of the breach. Code hosted by those suppliers, Inbenta and SocialPlus, was swapped with malicious scripts that skimmed credit cards processed by Ticketmaster and its affiliates during the period.
But the Magecart campaign didn’t stop there. By exploiting code hosted by Inbenta and SocialPlus, the actors backdoored their way into numerous online retailers as well. Figure 2 shows industries experiencing the ripple effects of the Magecart campaign, with retailers and wholesalers closest to the epicenter. Those breaches continued to reverberate through supply chains to affect a wide variety of organizations shown in the figure. This demonstrates the diverse and sprawling nature of third-party relationships and why multi-party incidents like the ones we analyze in this paper are critical to understand.
These are just two examples of recent, well-known multi-party ripple events. In our full study, Ripples Across the Risk Surface, we analyzed a total of 813 ripple events that affected over 5,000 organizations. Our analysis provides ample evidence to make solid recommendations about how organizations can better prepare for multi-party incidents. Download the report now to learn how you can minimize your ripple event risk.
1It should be noted that the Advisen dataset is not an exhaustive record of every organization involved in the incidents we study, but it is representative of loss events that become public knowledge. As such, counts and losses should be viewed as minimum estimates based on “known knowns.”
2Source HealthIT article: https://healthitsecurity.com/news/sens.-demand-amca-quest-labcorp-explain-failure-to-detect-breach
3Source HealthIT article: https://healthitsecurity.com/news/amca-files-chapter-11-after-data-breach-impacting-quest-labcorp








