While the types of organizations covered in a previous post officially fall under the Healthcare designation according to NAICS, it’s important to realize that the broader healthcare ecosystem spans numerous industries. Hospitals, for instance, have extensive supply chains that include equipment manufacturers, pharmaceutical producers, insurance providers, IT services, government agencies, and many more. Such entities often have deep connections to the healthcare provider’s facilities, operations, and information systems. This, of course, has significant ramifications for third-party risk management.
A sampling of these non-Healthcare industries is given in the figure below, and it tells a pretty interesting story for those who follow the threads. “Big Pharma” has the largest footprint in terms of hosts, 3rd party service providers, and countries of operation. They appear to have discovered the right prescription for keeping that large Internet footprint relatively hygienic. Manufacturers of various types of healthcare apparatus and instruments show a similar profile of extensive assets yet fewer findings. It’s rather interesting, therefore, that the remaining industry in the manufacturing sector—Medical Equipment—exhibits an inverted ratio for exposure and Internet surface area. Something to consider for healthcare firms that are integrated with third parties that manufacture medical equipment.
COMPARISON OF RISK SURFACE DIMENSIONS ACROSS THE BROADER HEALTHCARE ECOSYSTEM
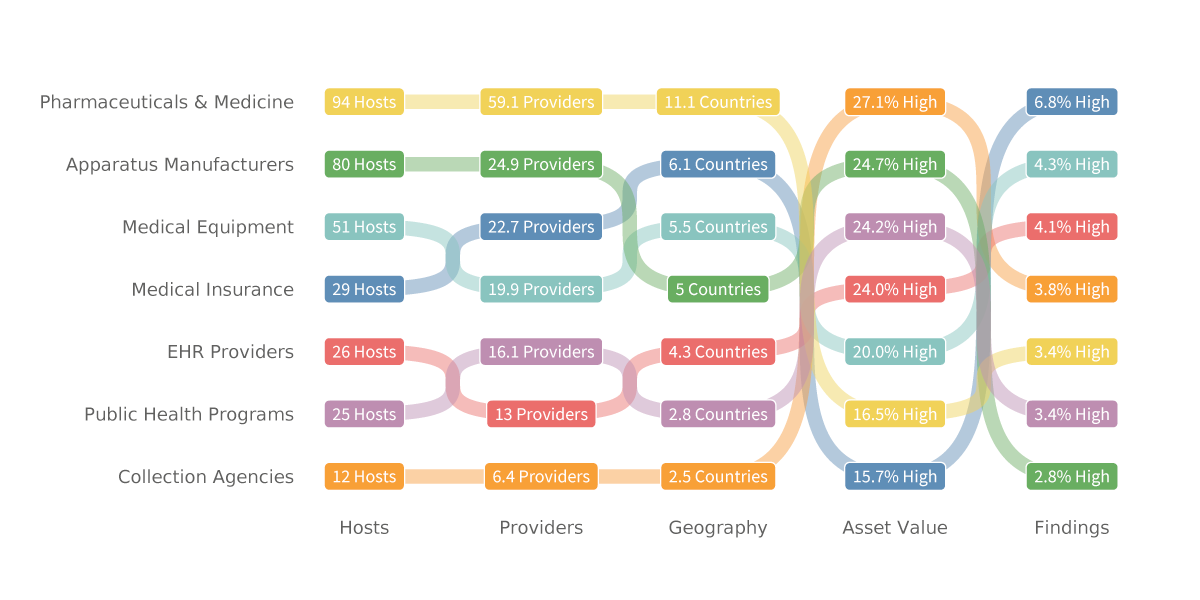
As a reminder that not all supply chains are physical, the digital supply chain is well-represented in Figure 7. The information-heavy industries of medical insurance, electronic health records (EHR) systems providers, and collection agencies occupy three of the top four slots for the highest rate of security findings. And lest one doubt that Collection Agencies deserve to be on the list, consider the example of the American Medical Collection Agency (AMCA). A breach of its systems in May 2019 compromised the personal information of over 24 million individuals. Most of the individuals affected had no direct relationship with AMCA; they provided their data to other healthcare entities, and those entities sent the data to AMCA for debt collection. Even though only AMCA’s systems were compromised those other organizations suffered substantial financial fallout from the breach.
Bottom line: when considering where the next breach might strike, don’t neglect to assess the supply chain and broader third-party networks. Healthcare is much more than meets the eye.
Two Things to Consider
1 Change the way you think about managing third-party risk. Consider the rigor that goes into assessing and mitigating cyber risk internally. Then compare that to how third-party risk is handled. Would you base your internal risk assessments on surveys and attestation? Of course not. Why then has this become the standard for third parties?
2 Managing risk—whether internal or third-party—requires focus. There are too many things to assess and do, giving rise to the endless “hamster wheel of risk management.” A better approach starts with obtaining an accurate picture of your risk surface and the exposures across it (which includes third-party relationships).
To learn more about the risk surface of healthcare firms, download the full report here. You will see the full results from the research and will find out how you can use the information to enhance your third-party cyber risk program.







