Question: How do supply chain attacks like the SolarWinds incident work?
Answer: Traditional attacks compromise the desired target directly. In a supply chain attack, the criminal compromises a supplier of the target rather than compromising the target. Criminals have two primary motives for compromising a supplier, rather than the target directly. The first motive is that the supplier may have weaker security controls than the target, which decreases the risk and cost of the operation. The second motive is that in targeting a supplier, the criminals not only compromise their target but also potentially other customers of the supplier, magnifying the yield of their compromise.
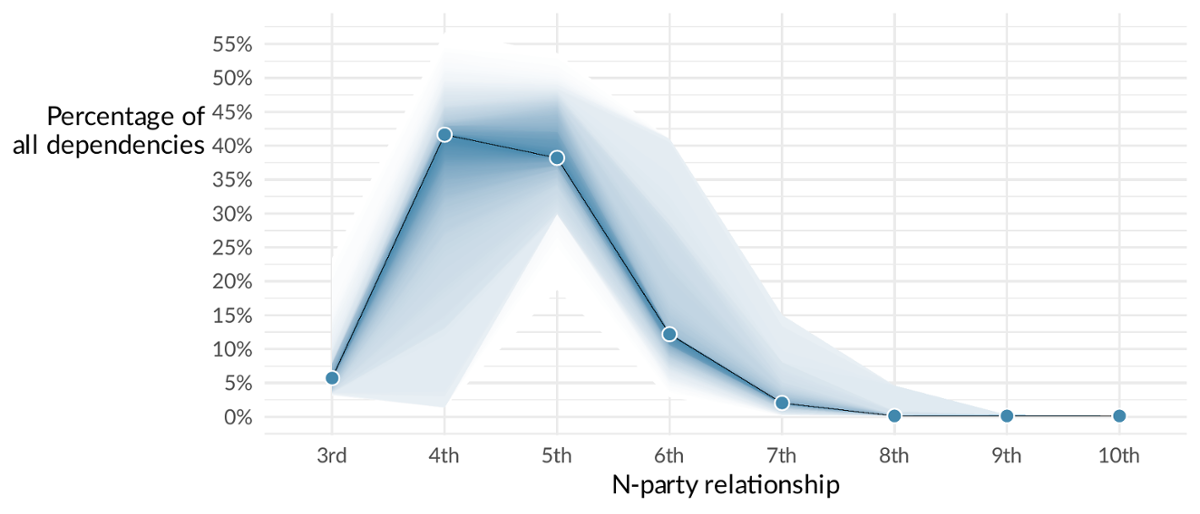
The prime suppliers that miscreants compromise are ones that host sensitive customer data and ones that yield access to the target environment. In June 1999, the American Medical Collection Agency was compromised, resulting in the theft of detailed medical records of over 30 customers of AMCA. In compromising SolarWinds, the SUNBURST operation compromised thousands of the most important organizations.
The SUNBURST operation was unique in that it compromised the software supply chain, inserting a command and control infrastructure inside SolarWinds Orion software. Once completed, all the criminals had to do to compromise some of the most important institutions and companies in the world was to wait for customers to update to the latest version of Orion.
Question: How did the SolarWinds attack get through everyone’s defenses?
Answer: To be clear, the SolarWinds SUNBURST campaign did not compromise everyone's defenses. RiskRecon works closely with hundreds of organizations across the world, many of which use the SolarWinds Orion software. While the malicious code did get into these organizations, some had restricted the ability of the SolarWinds software to communicate out to the Internet, limiting communication to command and control servers.
That said, many organizations did not expect this type of attack and thus did not constrain SolarWind's ability to communicate to the Internet, enabling the breach to execute unrestrained.
Question: What steps should enterprises be taking to beef up IT supply chain security?
Answer: There are three strategic initiatives that organizations are undertaking to reduce the likelihood of being impacted by another SUNBURST-like incident. First, organizations are reassessing the inherent risk of their software suppliers to identify the vendors that use software that has privileged access to their assets. For those vendors, companies are expanding their assessment criteria to examine the integrity of the software development process to ensure that controls are sufficient to prevent the introduction of malicious code.
Second, organizations are doubling down on the principle of least privilege. For example, during my time as CISO of a large financial institution, any software that required communication with the Internet was limited in its web access permissions to only accessing pre-determined update sites. Such a policy blocks the software from communicating with command and control infrastructure. It provides the additional benefit of raising alerts when the software unsuccessfully attempts to reach its C2 servers.
Third, knowing that despite their suppliers manifesting strong control over the integrity of their software, companies are revisiting their security monitoring capabilities, with a particular focus on detecting unexpected communications emanating from IT infrastructure.