Sponsored by RiskRecon, a Mastercard Company, and conducted by Ponemon Institute,1,162 IT and IT security professionals in North America and Western Europe were surveyed for a new study, Data Risk in the Third-Party Ecosystem. All participants in the research are familiar with their organizations’ approach to managing data risks created through outsourcing. Over the coming weeks, we will examine and discuss the responses in the study.
In this blog, we examine the lack of visibility the majority of organizations have into risks from their vendor ecosystem.
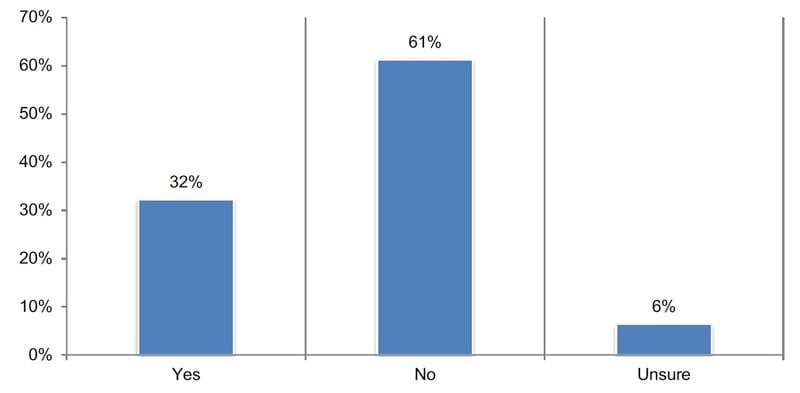
Few companies maintain a comprehensive inventory of all third parties with whom they share information. As shown in Figure 1 below, 67 percent of respondents say they do not have (61 percent) or are unsure (6 percent) if their company has such an inventory.
Of the 32 percent of respondents who say their organizations have a comprehensive inventory, it is estimated that an average of 2,103 third parties are in this inventory. Within the third-party inventory, it is estimated that an average of 48 percent of all third parties are sharing sensitive and confidential information with Nth parties.
Of the 32 percent of respondents in companies with a third-party inventory, 68 percent admit that the inventory does not include all third-and Nth-parties their organizations have a relationship with that might have access to their sensitive and confidential information.
Figure 1. Does your company have a comprehensive inventory of all third parties with whom it shares sensitive and confidential information?
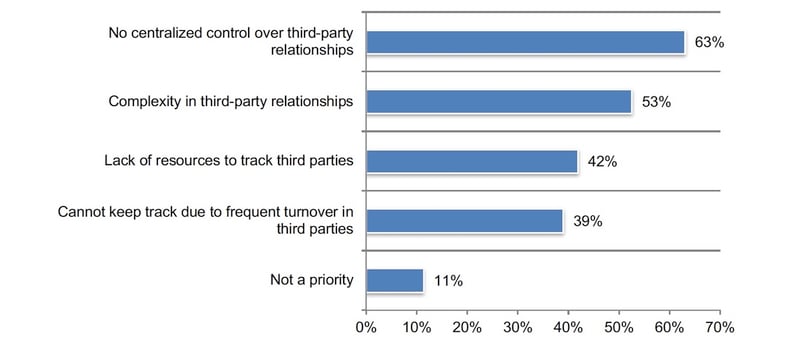
 To have a comprehensive inventory, centralized control over third parties is critical. As discussed previously, accountability for third-party risk management programs is dispersed throughout organizations. This lack of centralized control over third-party relationships (63 percent of respondents) is the primary barrier to determining how many third parties have access to their sensitive and confidential information, as shown in Figure 6.
To have a comprehensive inventory, centralized control over third parties is critical. As discussed previously, accountability for third-party risk management programs is dispersed throughout organizations. This lack of centralized control over third-party relationships (63 percent of respondents) is the primary barrier to determining how many third parties have access to their sensitive and confidential information, as shown in Figure 6.
This is followed by the complexity of these relationships (53 percent of respondents) and the lack of resources (42 percent of respondents). The inability to keep track because of frequent turnover in third parties (39 percent of respondents) may be improved by centralizing control.
Figure 2. Reasons companies do not have a comprehensive inventory of all third parties
Companies lack visibility into Nth parties that have their sensitive or confidential data.
Only 36 percent of respondents say their organizations are notified when third parties share their information with Nth parties with whom they have no direct relationship. Only 29 percent of respondents say their organizations have visibility into Nth parties that have access to sensitive and confidential information.
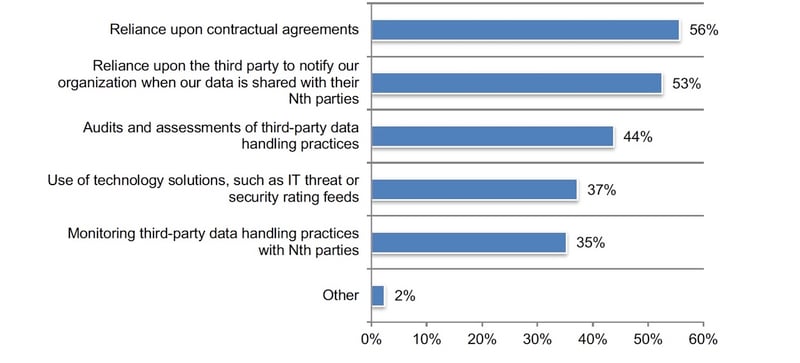
According to Figure 4, of the 29 percent of respondents who say they have such visibility, 56 percent say visibility is due to reliance upon contractual agreements and 53 percent of respondents say they trust the third party to notify their organizations when their data is shared with their Nth parties. Only 44 percent of respondents say their organizations conduct audits and assessments of third-party data handling practices and only 35 percent monitor third-party data handling practices with Nth parties.
Figure 4. How does your organization achieve visibility into vendors your company does not have a direct relationship with?
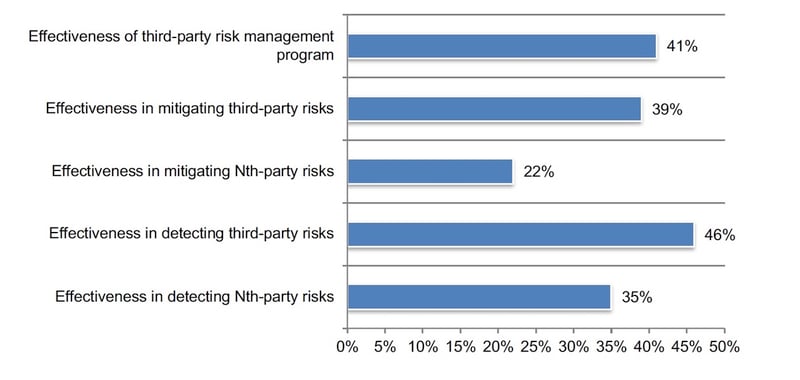
Most organizations are unable to mitigate third-party and Nth-party risks. We asked participants to rate the effectiveness of their third-party risk management program and in dealing with third-party and Nth party risks on a scale from 1 = not effective to 10 = highly effective.
Figure 5 presents the highly effective responses (7 + on a scale of 1 = not effective to 10 = highly effective). Only 39 percent of respondents rate their companies’ effectiveness in mitigating third-party risk as highly effective. Regarding Nth party risk, only 22 percent rate their effectiveness as high. Forty-six percent of respondents say their organizations are effective in detecting third-party risks. Only 35 percent of respondents say their organizations are effective in detecting Nth-party risks.
Figure 5. How effective is your organization in mitigating and detecting third-party and Nth party risks in your organization’s third-party risk management program?