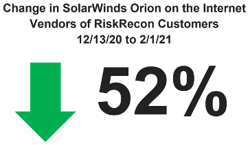
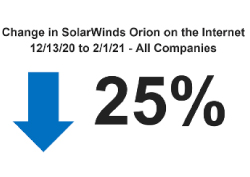
It's already been a couple of months since the bombshell of the SolarWinds supply chain attack came to light and it's becoming increasingly clear that it'll take the better part of 2021—and likely longer—to peel back the onion on its impacts across the enterprise IT world.
But we don't have to wait for a full forensic examination to uncover the most fundamental truth about SolarWinds fallout. Namely, that CISOs and CIOs are having the wrong conversations at the board level about cybersecurity today.
While discussions about driving down critical vulnerabilities in enterprise software do need to happen, SolarWinds highlights why organizations can't let those derail executives from looking at the broader picture of enterprise cyber risk. Today's technology environments are complex ecosystems comprised of far more than internal systems and software. They're cloud-enabled and dependent on multiple partners—who themselves depend on their own technology partners. This risk travels all the way downstream to enterprises with whom they may have never done business directly before.
"Your company or organization is part of a value stream that is a massive web of engagement. It's not a linear value stream where you've got one or two people to the left and one or two people to the right and it's easy to figure out," explained Robert Brese, VP and Executive Partner at Gartner, who recently joined me in an insightful online panel on the wide-reaching implications of the SolarWinds attack. "The traditional way of vetting vendors and partners--having a consulting firm go interview a bunch of people, do some audits, fill out some questionnaires, spend 90 days doing that and make a decision, bring them on board, and maybe checking in with them each year--is a recipe for disaster in today's ecosystem."
As Brese explains, CIOs and CISOs need to up-level the conversations they're having with CEOs and boards to draw greater attention to the critical pieces of an organization's IT ecosystem—not just the software they run in-house. They need to find ways to talk to these executive stakeholders about third-party and Nth party risk and explain why a big part of cybersecurity today is enmeshed with procurement and vendor management efforts.
This means that board-level cybersecurity conversations these days should be focusing heavily on how the organization is going to track and monitor risk levels at their vendors and across their supply chain ecosystem, and how those results should be used to drive down cyber risk. Additionally, the board, CEOs, and CFOs need to be made aware that as digital transformation efforts keep pushing forward and it becomes ever easier for lines of business to procure their cloud services and tools, there needs to be a better level of governance to make sure everything lines up with risk policies and architectural goals.
"It becomes incumbent on CIOs and CSOs to partner with their chief financial officer and their procurement office to build a strong partnership so people don't bring things into the ecosystem without aligning to the architecture and to supply chain risk management processes," Brese says, explaining that getting cybersecurity-related clearance should be baked into procurement processes for many more projects and services than is currently the norm within the typical enterprise. "The CFO is issuing dollars and looking at expenditures and can raise those kinds of issues. It's critical (for security leaders) to create a partnership with procurement and finance so that this stuff doesn't just arrive in your ecosystem."