The criminal genius of the SUNBURST campaign not only lies in its technical sophistication but also in the self-selection of entities that were compromised through the breach. Customers of the SolarWinds Orion platform are inherently successful entities, being sophisticated enough to require a robust infrastructure management platform. The SolarWinds platform was the vector to get to the targets the criminals wanted to compromise.
 RiskRecon’s analysis of the SUNBURST signaling entities reveals that the entities compromised represent some of the most successful and important organizations to society’s present and future success – a treasure trove for any nation-state. The data also reveals that supply chain attacks know no boundaries, impacting all entities that rely on the software, spanning industries, and geographies.
RiskRecon’s analysis of the SUNBURST signaling entities reveals that the entities compromised represent some of the most successful and important organizations to society’s present and future success – a treasure trove for any nation-state. The data also reveals that supply chain attacks know no boundaries, impacting all entities that rely on the software, spanning industries, and geographies.
This post summarizes the results of RiskRecon’s analysis. Please visit this page if you would like a detailed listing of the companies identified, along with the associated data. RiskRecon intends to limit access to the detailed information to risk professionals of organizations seeking to understand and act on their ecosystem risk exposure to the SUNBURST campaign.
See Data Sources and Methodology at the end of this post for a description of how RiskRecon compiled this research.
SUNBURST Signaling Entities
The 129 entities RiskRecon has identified are no doubt a subset of the total companies that have signaled to the SUNBURST C2 infrastructure. However, even among this subset, there are a disproportionately large number of entities that a nation-state would desire the secrets of. The signaling entities include:
- a division of the United Nations,
- a rapidly rising electric car manufacturer,
- a company pioneering next-generation battery technology,
- a US defense contractor that provides engineering and technical support for weapons systems,
- a US defense contractor that designs and builds ships for the US Navy,
- and another company that provides cybersecurity and system administration to the US Department of Defense.
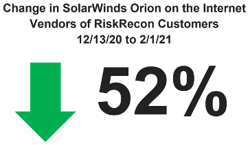
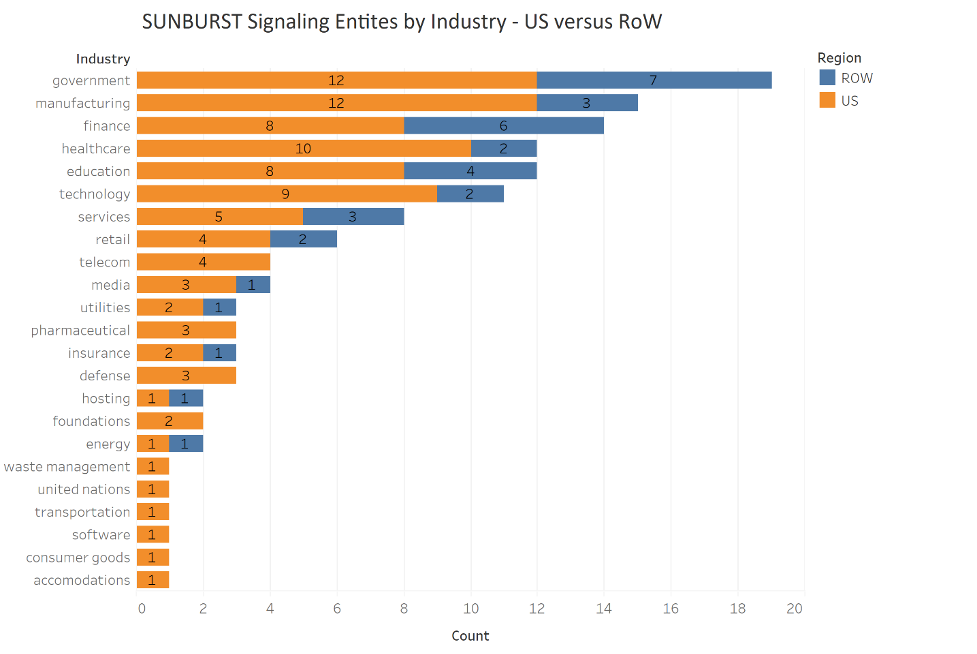
Twenty-three industries are represented among the 129 entities signaling to the C2 infrastructure. The diversity of industries shows that no sector was spared, regardless of their diligence in managing cybersecurity risk well. The large representation of the government and education sectors is no surprise given their large presence in the economy and their lack of cybersecurity regulation, nor the healthcare industry which faces strong headwinds of operational and IT complexity. Finance though, which leads the way in good cybersecurity risk management, represents over 10% of the population.
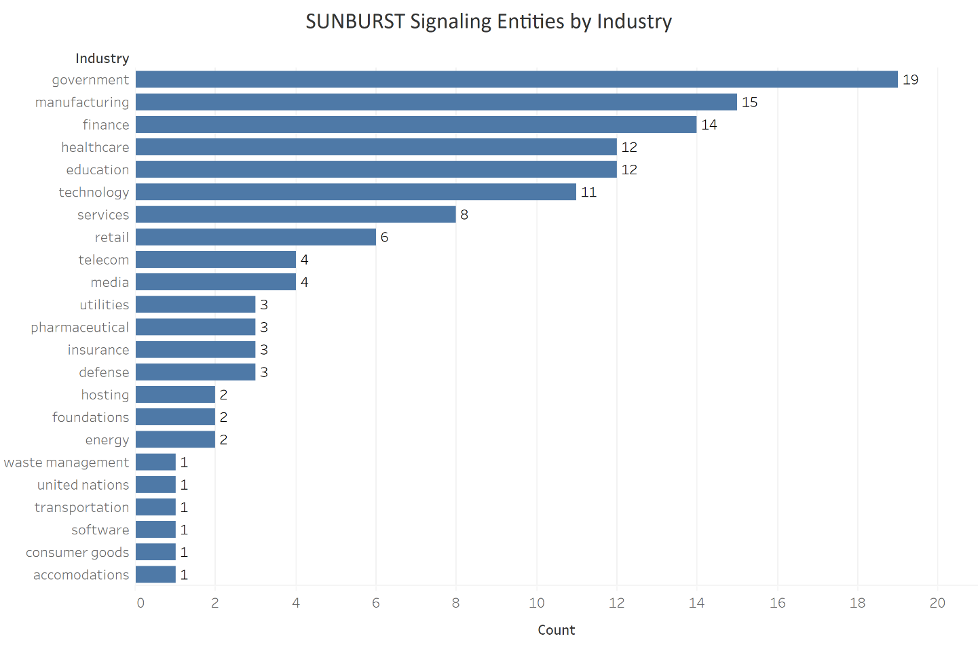
Public versus Private Sector
The public sector was hit particularly hard. Combining the pure government administration group with its other services such as education and transportation, public entities combine for 31% of all entities compromised.
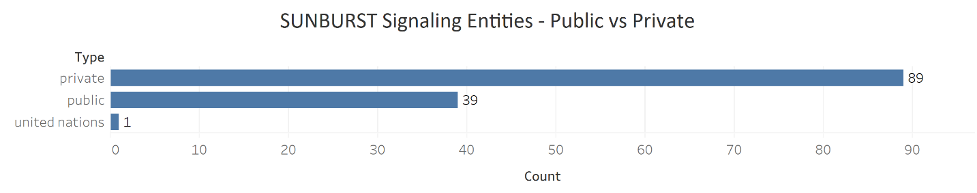
Of the public sector entities compromised, general administration offices of national, state, and local governments were hit particularly hard. Education was the second-hardest hit, with both universities and local school districts signaling out to the SUNBURST C2 infrastructure.
 SUNBURST Geographic Distribution
SUNBURST Geographic Distribution
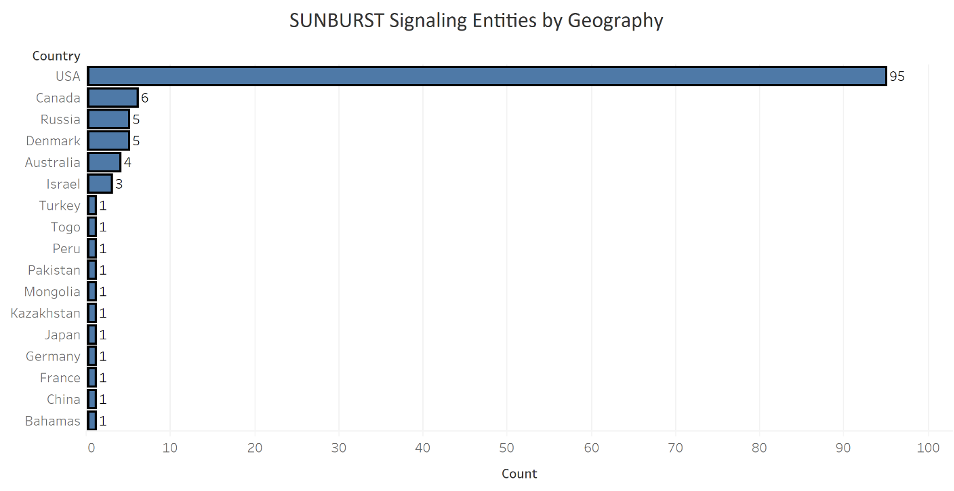
Ranging from Mongolia to Canada, the geographic distribution of SUNBURST-impacted entities shows that the impact of a supply chain attack knows no borders. Even Russia-based entities signaled out to the C2 infrastructure. The United States accounted for the largest number of entities at 74%.
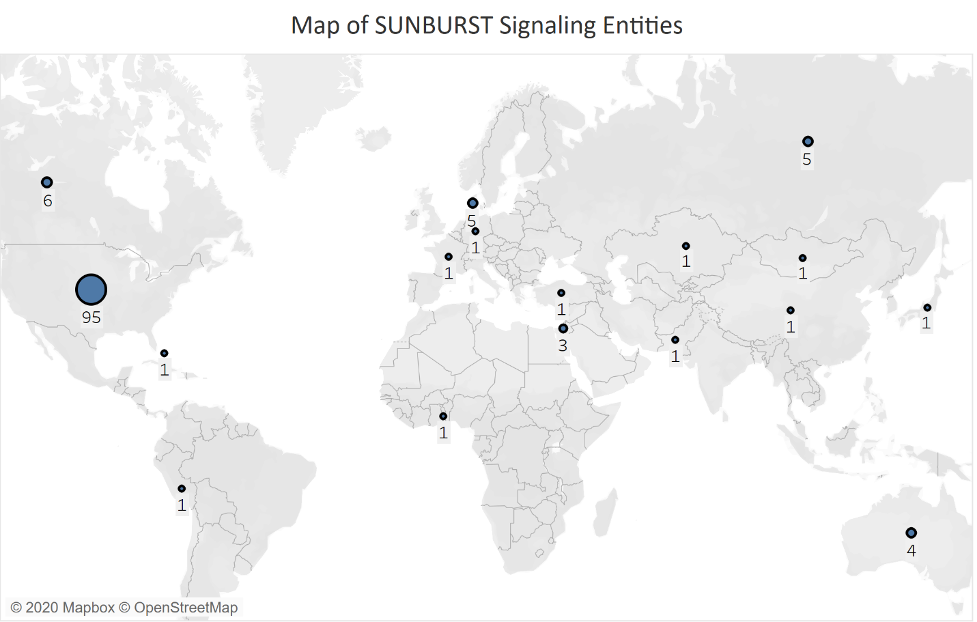
The graphic below shows the same SUNBURST geographic distribution as a chart.
 The industries impacted also differed by geography. The chart below compares the US versus the rest of the world.
The industries impacted also differed by geography. The chart below compares the US versus the rest of the world.
Data Source and Methodology
It is well understood that SUNBURST encodes part of the victim's internal hostname as part of the subdomain used in communication with the command and control (C2) infrastructure. These decoded subdomains can be helpful in revealing SUNBURST victims. RiskRecon collected 139,514 unique subdomains that were part of the primary SUNBURST C2 domain (avsvmcloud[.]com) using passive DNS monitoring. RiskRecon decoded these subdomains using the algorithm first published by the cybersecurity firm RedDrip Team. RiskRecon then separated the results into sensical and non-sensical results. For each sensical decode (has the appearance of a hostname or of an entity name), RiskRecon attempted to attribute the subdomain to an entity using the following methods:
- Determine the owner of the domain revealed in the decoded subdomain using WHOIS domain registration queries.
- For domains that were incomplete, RiskRecon inferred the given domain and then performed WHOIS domain registration queries. For example, a domain might be XYZ.c. RiskRecon would infer XYZ.com, XYZ.co, and XYZ.co.uk as part of the analysis.
- Google search result analysis of subdomain strings.
- Website analysis to augment the domain ownership analysis or just website analysis where domain ownership was anonymized in registration records.
For each entity flagged by RiskRecon as signaling to the C2 infrastructure, RiskRecon assigned a “guess strength”. The guess strength was either high, medium, or low, depending on the strength of the attribution. For example, a high rating was assigned for companies where the decoded subdomain revealed the full domain and the domain was registered to the company and the domain websites confirmed the attribution.
A Word of Caution
Determining definitively that an entity was compromised requires direct evidence. While opensource intelligence (the basis of this analysis) may strongly indicate a specific entity signaling to the SUNBURST C2 infrastructure, it does not guarantee that the organization was in fact compromised or that any data was stolen. An internal host can technically be assigned any name. As such, a decoded subdomain may not reveal the true source of the signaling. Further, even if an entity has signaled to the C2 infrastructure, the criminals may not have leveraged their position to pilfer the systems.
Description of the RiskRecon SUNBURST Data File
RiskRecon has enumerated the entities in a data file that it identified as signaling to the SUNBURST C2 infrastructure, along with other attributes such as the decoded subdomain string, the attribution indicators, and entity geography. RiskRecon is making this file available to any risk professional to use for the benefit of their employer in understanding and acting on their SUNBURST risk exposure. To request access to this file please submit the form on this page. Requests must be sent using the email address of your employer.
The data file contains the following attributes:
- C2 subdomain (not decoded)
- Decoded C2 subdomain
- Guessed entity
- Signal count – the number of times the entity appeared in C2 subdomains
- Evidence – the factors used to attribute the decoded subdomain to the guessed entity
- Guess strength – the rating of the strength of the evidence
- Industry
- Type – public or private
- Country
- State