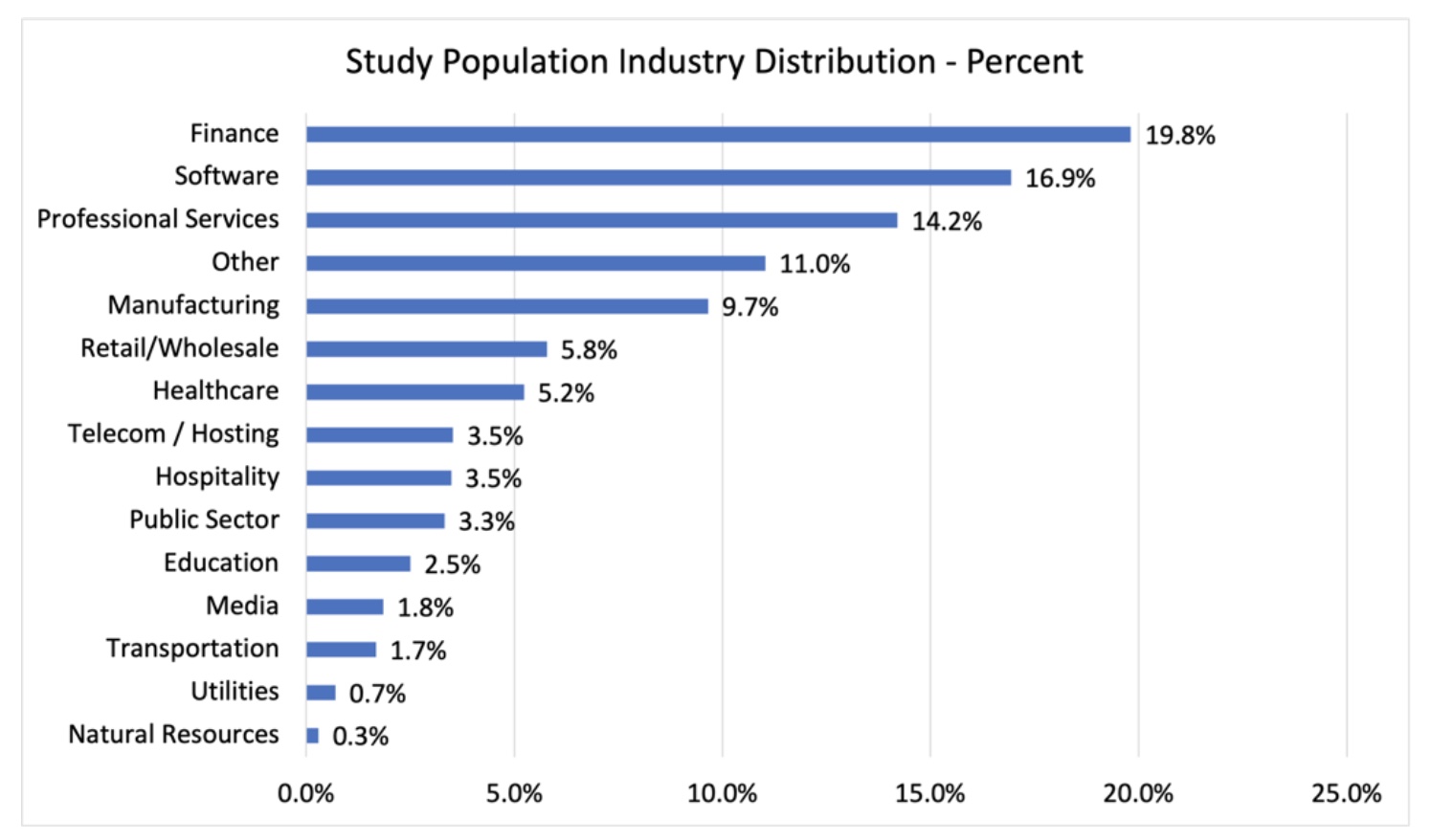
Health information is regarded as highly private data by many individuals. The unauthorized disclosure of health data can, and has, caused individuals to suffer personal embarrassment, identity theft and worry. In an effort to keep health information private, especially as health records have become digitized, the US government has enacted two laws over the past 25 years: HIPAA and HITECH.
 We’ve covered these regulations in three previous articles. In this series’ fourth and final article, we discuss third-party risk management in relation to HIPAA & HITECH.
We’ve covered these regulations in three previous articles. In this series’ fourth and final article, we discuss third-party risk management in relation to HIPAA & HITECH.
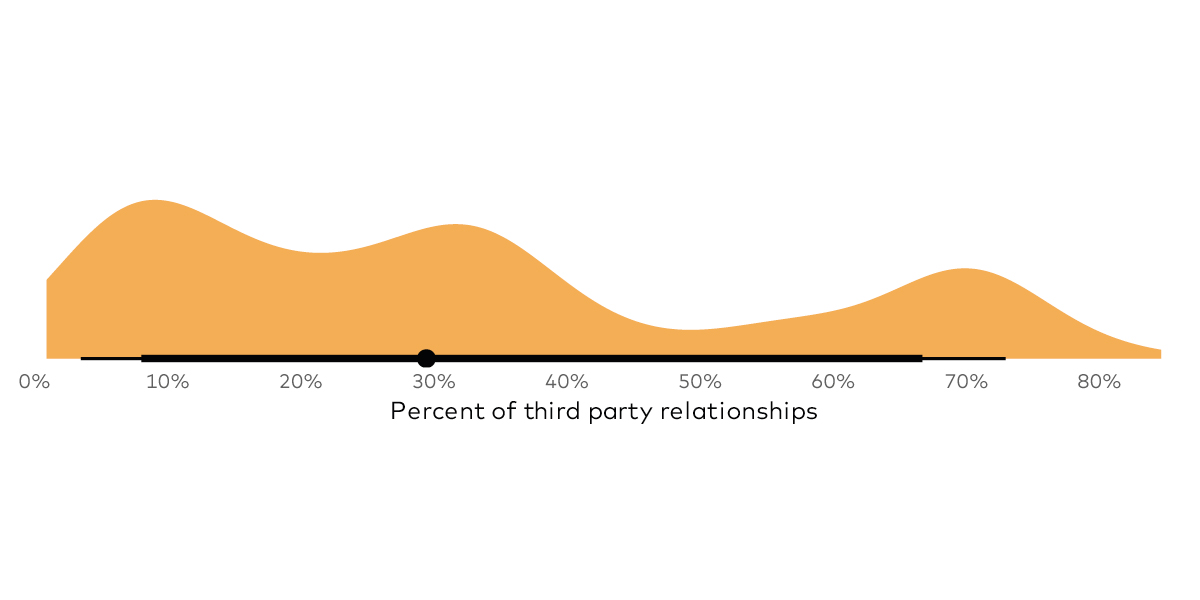
One risk facing organizations’ security & privacy programs are their third-parties. Many third-parties have access to sensitive data, including health data, and if these entities don’t have good security programs, they can present unnecessary risks to your organization. In this article, we discuss both what HIPAA & HITECH require of third parties and what you can do to proactively protect the health data your organization has been entrusted with.
Important Definitions
Covered Entity
A covered entity is any health plan, healthcare provider who transmits any health information in electronic form in connection with a transaction or healthcare clearinghouse (i.e., an organization that processes health care-related transactions or non-standard data).
PHI
PHI stands for “protected health information.” PHI is individually identifiable health information that is transmitted or maintained in any medium, physical or digital; however, PHI is excluded from education records covered by FERPA, in employment records held by a covered entity in its role as an employer and regarding any person who has been deceased for over 50 years.
What Counts as a Third-party
Under HIPAA & HITECH, a third-party is referred to as a “business associate” (we will use “third-party” and “business associate” synonymously throughout this article).
Under these laws, a business associate is defined as any health information organization, e-prescribing gateway or other person that provides data transmission services involving PHI to a covered entity on a routine basis; a person that offers a personal health record to at least one other individual on behalf of a covered entity; or a subcontractor that creates, receives, maintains or transmits personal health information on behalf of a business associate. A business associate, however, does not include health care providers in regards to disclosures by a covered entity to a health care provider regarding an individual’s treatment; a plan sponsor in regards to disclosures to the plan sponsor by the group health plan, health insurance issuer or health maintenance organization; a government agency that determines eligibility for, or enrollment in, a government health plan or the collecting of health information related to determining eligibility for or enrollment in a government health plan; or a covered entity if it participates in an organized health care arrangement that provides a function or services as described above.
Requirements
In short, your third-parties must comply with both HIPAA & HITECH if they meet the requirements (as defined above) for a business associate. There are, however, some important requirements to note:
Violations, Data Breaches and Notifications
Both your organization and your third-parties are required to take reasonable steps to detect breaches. This means an organization can’t justifiably claim a notification wasn’t made because the breach was undetected if there were reasonable steps the organization could have taken that would have led to the discovery of the breach.
If either your organization or your third party suffers a data breach involving PHI, the organization that suffered the data breach must notify each affected person whose PHI has been (or is reasonably believed to have been) impacted by the breach within 60 calendar days.
Notwithstanding, both your organization and your third-parties will be held liable for any violations (including data breaches) and potentially subject to fines (e.g., if one of your third parties has a data breach involving PHI, both your organization and your third party could be fined).
Disclosure or Use of PHI by Third Parties
Third-parties are to only disclose or use PHI as is allowed in the contract with your organization and required by law. Law requirements include disclosing PHI when an individual requests their PHI and when the Secretary of the Department of Health and Human Services (who is responsible for enforcing HIPAA and HITECH) requires such disclosure or use.
The Sale of PHI
Neither your organization nor your third parties may sell PHI, except when disclosing PHI for public health purposes; for research purposes where the only money received is a reasonable cost-based fee to cover the costs to prepare and transmit the PHI used in the research ; for treatment and payment purposes; for the sale, transfer, merger and acquisition or consolidation of all (or part of) a covered entity, including for the purposes of due diligence; either to or by a business associate for activities it’s undertaken on behalf of a covered entity and the only money received is given by the covered entity for the performance of those activities; to an individual when requested; as required by law; and for any other purpose permitted by and in accordance with the requirements of HIPAA & HITECH so long as the only compensation received is a reasonable, cost-based fee to cover the cost to prepare and transmit the PHI.
What Your Organization Can Do
There are several things your organization can do to comply with HIPAA & HITECH, including consulting with appropriate legal counsel and other experts to determine how HIPAA & HITECH apply to your organization; ensuring your organization only works with third-parties who are able to adequately protect PHI and comply with both of these regulations; reviewing vendors’ security posture on at least an annual basis; for vendors who are critical to your organization in complying with HIPAA and HITECH, conducting more frequent but less-intensive reviews than the annual review (but still doing annual, in-depth reviews) of the third-parties’ compliance & security programs such as continuous assessments, quarterly or semi-annually; and partner with your vendors and work together to improve both of your organization’s security and compliance programs.