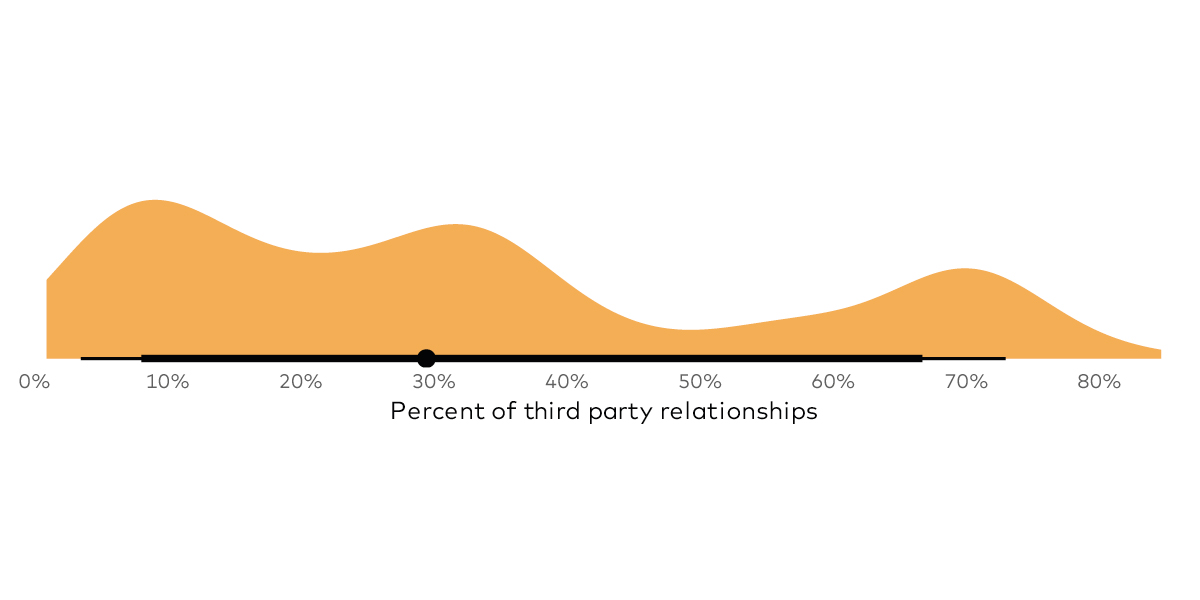
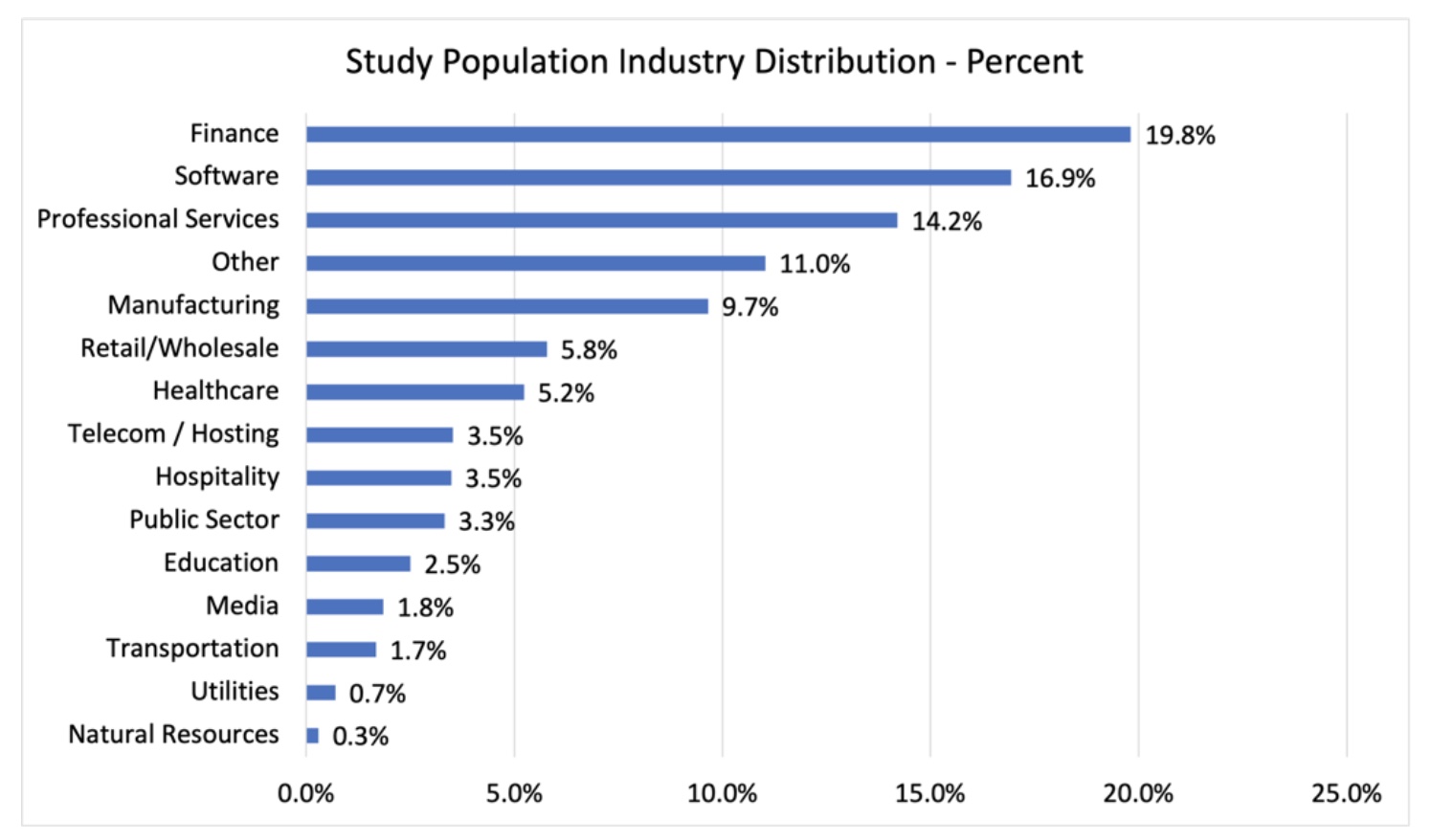
Unfortunately, too many enterprises today are completely blindsided by down-stream impact from ripple events at their third parties. They never see the threat coming because they simply do not have the mechanisms in place to monitor how well their vendors and partners are managing risk in shared or connected systems.
Most organizations remain relentlessly hyper-focused on cybersecurity internal controls, without looking to very relevant external systems. Companies that do spend money to help with vendor risk only spend an average of about 17% of that security budget third-party risk management—and that money is often spent on ineffective remedies.
The truth is that many third-party risk management programs rest on accountability mechanisms that were devised in a very different technology era. When the field of third-party risk management arose a couple of decades ago, the standard for checking up on external parties was via vendor questionnaires, documentation, and the occasional visit to a larger third-party vendor’s data center.
This worked okay when there were a relatively small number of vendors to be assessed, the company data still resided on-site, and the vendors themselves. had large, sophisticated security teams (e.g., Microsoft, Oracle, EMC, etc.). Of course, this world no longer exists—but the third-party risk management process has not changed. As a result, many enterprises are flying blind with regard to third- party risk. They’re sharing crown jewels without any assurance that moment-to-moment, day-in, and day-out, ALL of their vendors are reliably protecting their risk interests.
The question is, how much of your business viability can you afford to rest on unverified trust? Do you trust:
- That your most critical vendors have a 10% internet system software patching failure?
- That all of your vendors consistently focus threat intelligence operations on internet points of presence that matter?
- That vulnerabilities in your vendor's systems can’t be exploited to attack systems where your data resides?
In cybersecurity, it’s not good enough to simply trust.
No other area of security relies almost entirely on the “honor system” to manage risk. It would be like sending email to all employees, asking them a long list of security questions about their computer. And then entirely relying on their answers without any testing, monitoring, or verification.
You must verify third-party risk posture, too. Because if the vendor performs poorly as an enterprise, eventually that poor performance will show up in systems relevant to you.
Download our latest white paper, Why Third-Party Risk Matters, to read more about minimizing third-party risk.