In a perfect world, third-party risk managers would be able to accurately and continually assess expected losses associated with each vendor in their supply chain. Sadly–that is not our reality. In turn, what we do have is a reasonable proxy for organizational cyber risk posture that meets the needs of this analysis and risk managers.
While we all know that firms with strong security defenses can still suffer major losses (and the weak but lucky ones might squeak by with none), experience shows that firms that manage risk well perform better over the long term. For our research report, Uncertainty to Understanding, we chose to use the density of high and critical security findings affecting high-value assets as a measurable proxy for organizational cyber risk posture in our prediction models.
This measure of risk posture incorporates two key dimensions from RiskRecon’s dataset:
1. Security Findings: Detection of security-relevant issues that expose hosts to various threats. We focus on findings rated high or critical in severity according to the Common Vulnerability Scoring System (CVSS).
2. Asset Value: Relative sensitivity and criticality of hosts based on multiple indicators. We focus on high-value assets, which collect sensitive data, authenticate users, run critical services, etc.
Notably, this approach isn’t just an empty marketing scheme; it’s consistently reinforced by our research with RiskRecon. For example, our investigation of Internet of Things (IoT devices) from 2020 found a 70x jump in the rate of critical security issues in high-value assets between organizations that expose vulnerable IoT devices to the internet vs. those that do not.
Organizations that cannot manage the critical security issues affecting their most valuable assets are almost certainly struggling with many aspects of managing their cyber risk posture. The idea here is simple. We ultimately want to answer the question “How risky is this vendor relative to others?” If a vendor isn’t addressing the most severe security issues in their most valuable assets, they’re probably not managing risk posture in a way that sustains good performance. At the very least, they wouldn’t be your first choice for entrusting privileged access to your systems and data.
But there’s one more thing we need to do to enable proper comparisons of risk posture across all organizations. We must calculate the density of high and critical security findings in high-value assets on a per-host basis, normalizing firms of varying size and findings. Then we can examine how organizations in our sample perform according to our risk posture measure in the figure below.
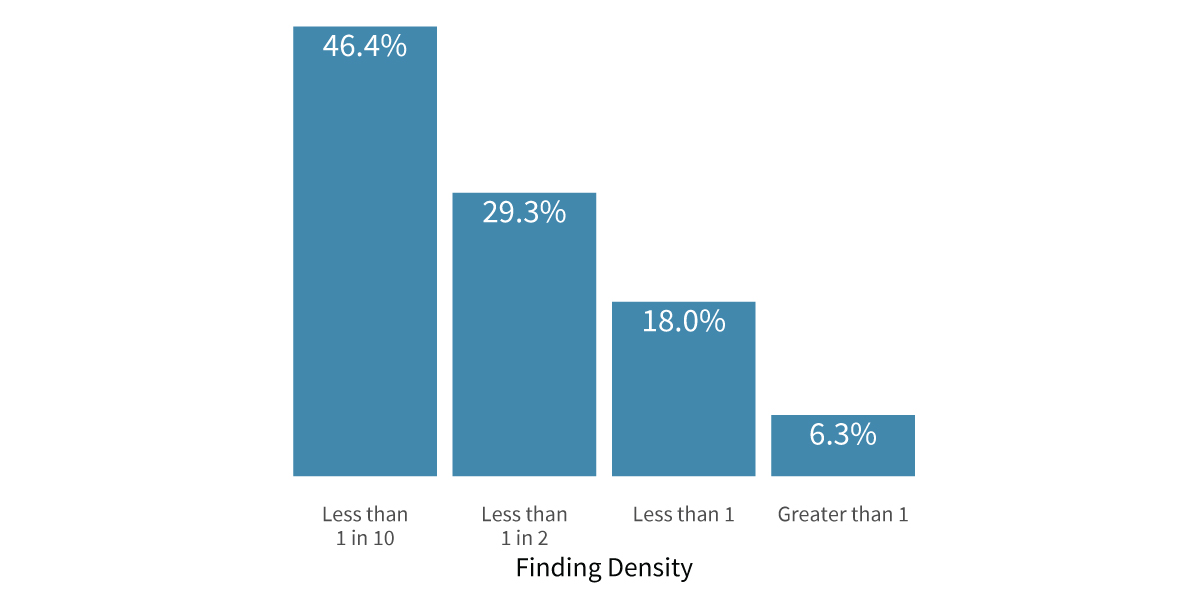
Here we see most organizations have less than one high or critical finding per high-value host. But there’s a subset of firms that have a much higher risk density. It’s this subset of high-risk vendors that we want to identify in our TPRM portfolio.
To get full details into our research, download our Uncertainty to Understanding report here.




.png)
