Many cyber breaches today impact organizations far beyond the initial victim. Depending on the incident, the effects can ripple across numerous other parties, wreaking havoc along the way. And while the ramifications of these ripples cut across all industries and sizes of organizations, these multi-party cyber incidents do tend to cluster more frequently in certain industries than others.
 As part of our series of research on enterprise risk surfaces, we engaged with the data analysis gurus at Cyentia Institute to examine the impact, the causes, and the probabilities around cyber ripple events. Our study, Ripples Across the Risk Surface, showed that multi-party incidents damage an average of seven different organizations, but sometimes they can affect as many as 131 distinct parties. The widespread fallout means that cyber ripple events cause 13x the damage of the typical single-party breach.
As part of our series of research on enterprise risk surfaces, we engaged with the data analysis gurus at Cyentia Institute to examine the impact, the causes, and the probabilities around cyber ripple events. Our study, Ripples Across the Risk Surface, showed that multi-party incidents damage an average of seven different organizations, but sometimes they can affect as many as 131 distinct parties. The widespread fallout means that cyber ripple events cause 13x the damage of the typical single-party breach.
Amidst the findings, our research showed that the bulk of cyber ripple events were triggered at organizations in just a handful of industries.
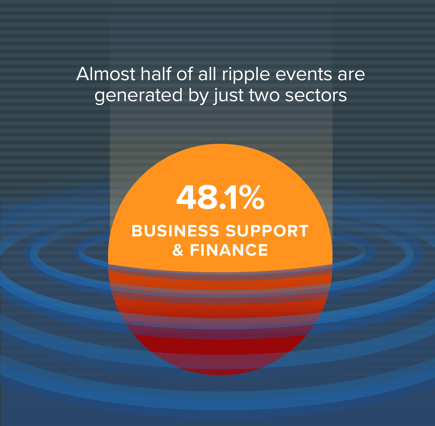
The top two sectors at the center of multi-party incidents--business support and finance—set off 48% of ripple incidents. Add in the public sector, information and professional organizations, and the top five industries are at the root of nearly 72% of multi-party cyber incidents.
Looking at the results, it's clear that business support and finance sectors dominate the top of the heap. Given the financial industry's push toward open-banking and the preponderance of information sharing and multi-institution transactions, that sector is a gimme for this kind of placement. But what of business support?
The vague designation of business support as categorized by the North American Industry Classification System (NAICS), includes a range of different kinds of administrative and support services, including office admin, document prep, and hiring services. But for the sake of this report, the category was a little less imprecise as it was overwhelmingly represented by two major sub-industries: credit bureaus and collection agencies.
While NAICS puts them in a different industry category, many people almost think of those two types of organizations as part of the financial ecosystem. At the very least, they're closely related to financial and insurance supply chains. So the business support category very well may be a reflection of the long-arm of risk that extends from the intricate digital supply chains of the financial services field.
Interestingly, in previous risk surface reports, we've found that the financial sector is not in bad shape compared to its peers. However, what we likely see at play here is that the law of averages is doing its work and that in an industry that is so highly interconnected and which runs such a high volume of multi-party transactions, it's inevitable for it to generate a substantial number of ripple events. The Ripples report data shows that when it comes to the connectivity of digital ecosystems, risk cuts both ways. Organizations in finance and business support not only cause the most ripple events, but they also tend to also be more likely to be impacted by ripple events.
Now, this isn't to say that there aren't a lot of other types of organizations that get wrapped up into ripple events as well. The research shows a wide range of other organizations that both cause ripples and are affected downstream by these multi-party cyber incidents. Once our analysis got beyond the common collection agencies, commercial banking outfits, and credit bureaus, we witnessed dozens of subindustries involved in these ripple events. Some other commonly associated organizations include hotels, computer systems designers, software publishers, and management consulting services.
It was often difficult to untangle the web of relationships and supply-chain dependencies just using the lens of industry categorization. The commonality that our research uncovered among those central to ripple events was that they tended to be organizations:
- in possession of gobs of sensitive personal data, usually aggregated from numerous other sources;
- that typically have large digital footprints; and
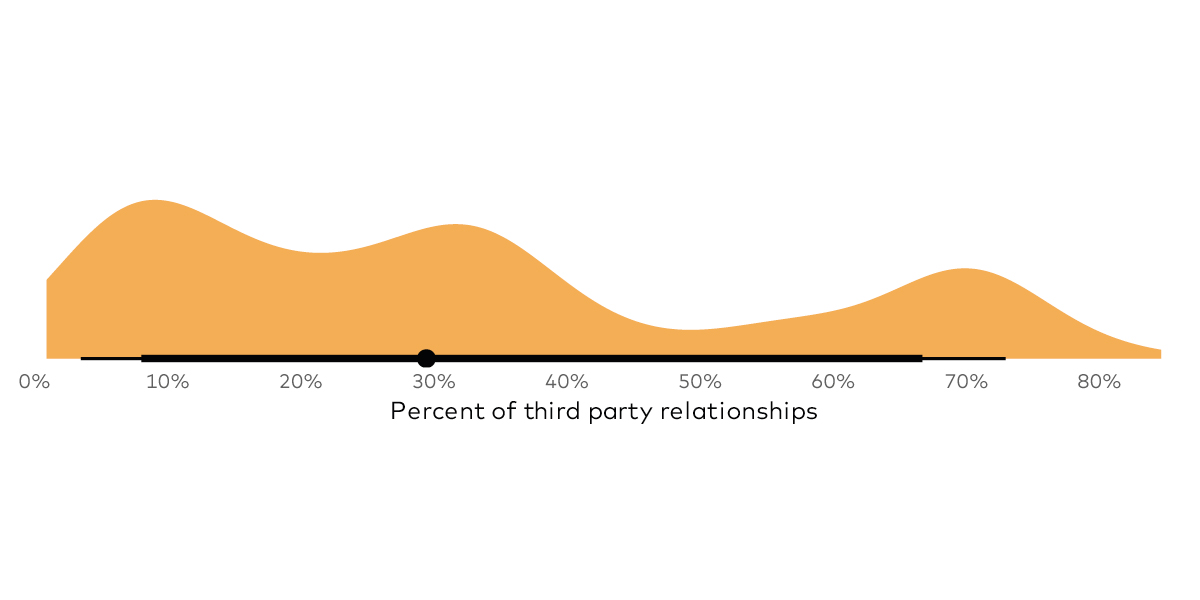
- which maintain extensive third-party relationships.
This brings a good point to perhaps draw further exploration and analysis from us and the rest of the security industry. In the light of the interconnected nature of modern business, it may make sense to think fresh about how we categorize third-party risk and risk of multi-party breaches. In the future, risk managers may need to think about developing some kind of risk classifiers or benchmarks for organizations that gets beyond the typical industry designations.
These kinds of organizations tend to be target-rich environments for attackers to set their sights on, and the bad guys are already seeking them out with increasing regularity. Events like the Equifax breach and the 2019 breach at the American Medical Collection Agency are a harbinger of more to come.
The point here is that regardless of industry, organizations that work with third-parties in highly-connected relationships need to think about the potential blowback that can come from ripple events. Organizations involved in a high degree of digital co-creation, information sharing, and complicated integrations should take measures to minimize their exposure to these kinds of incidents.