Security questionnaires are one of the most prevalent and recognizable tools used to gauge and manage risks in third-party IT environments. Unfortunately, the popularity of questionnaires is more of a function of familiarity and expedience than a testament to their efficacy as a risk management tool.
When the rubber meets the road, most risk professionals admit they have very little confidence in security questionnaires. They don't think that these assessments provide an accurate view of risk exposure or give them an effective route for requesting remediation from third-party vendors. But running questionnaires is usually a straightforward, budget-friendly process. Vendors may not always like them, but they typically know what to expect from them. And more importantly, most regulators accept questionnaires as a means to checking many of the boxes for third-party risk management (TPRM).
 And so, like firewalls and antivirus, they persist as a not-so-well-loved but de facto standard for their security domain.
And so, like firewalls and antivirus, they persist as a not-so-well-loved but de facto standard for their security domain.
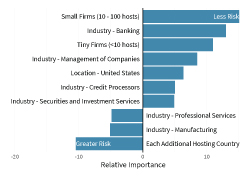
According to the recent State of 3rd Party Risk survey compiled by Cyentia Institute on behalf of RiskRecon, as things stand today some 84% of enterprises today employ security questionnaires. That's approximately twice the rate at which they use more advanced means of assessment like cybersecurity ratings to verify the security status of their third-party vendors.
The good news is that many organizations are innovating away from sole reliance on questionnaires. The study showed that 16% of vendors use a combination of security questionnaires, documentation review, remote assessments, cybersecurity ratings, and onsite assessments to round out their TPRM programs. Many others use a combination of two or three of those methods, with the most common backstop being documentation review, an assessment method used by 69% of organizations.
Nevertheless, a not insignificant ratio of TPRM programs—more than one in ten--still only assess via questionnaire. Additionally, digging into alternative assessment methods showed us that those are often only employed for a very small percentage of vendors. For example, while one in three TPRM programs incorporate onsite security evaluations, 60% of those do it for less than 10% of their vendors. So even when alternatives are employed, questionnaires are still the leading method for most assessments.
This is extremely problematic considering the results that TPRM professionals say they yield from these self-assessments. The survey showed that only about 34% of them say they believe questionnaire responses. That's likely because despite anecdotal industry evidence to the contrary and daily data breach headlines dominating the news cycles, some 81% of organizations report that the vast majority of their security questionnaires with no exceptions, claiming perfect compliance with requirements. Meaning that among that 81%, the net result is that their assessment rarely offered any kind of actionable insight to spur security improvements or remediations from vendors.
Questionnaires are starting to feel like a rubber stamp, as very few TPRM professionals believe that vendor security performance truly meets their security standards outlined in the questionnaire. Only about 14% of organizations today say they're highly confident that vendors are performing security requirements.
Now, maybe part of that may be a function of how good of a questionnaire assessment most programs are putting in front of their vendors. Our study showed that under 20% of programs leverage an industry-standard question set and the majority of the questionnaires are usually under 100 questions in length. For about 11% of programs, the questionnaire is 10 questions or fewer. But the suspicion on the believability of answers remained consistent no matter how many questions were asked. So it seems that many organizations are starting to recognize that the only thing that can give them more confidence is to layer in more assessment methods and continue to deprecate the over-reliance on questionnaires.
By moving to a data-driven third-party risk program, and by combining data from a wide range of sources-- from a wide range of sources -security rating services, news feeds, financial ratings, and questionnaires—organizations can start taking their TPRM programs to a higher level of maturity.




.png)