RiskRecon Empowers Security and Risk Teams to Move Beyond Static Assessments with Continuous Third-Party Risk Monitoring; One Platform, Many Uses
The rapid shift to remote work amid a quickly expanding digital world resulted in the hurried adoption of new cybersecurity tools and technologies by security teams working around the clock to keep pace with the dynamic digital world.
Fast-forward to today, and despite record cybersecurity investment in the last few years, many security and risk professionals are struggling with managing cyber risk in their current environment and extended ecosystem. Teams are stuck with overflowing security stacks full of tools and technologies that don’t work together or simply aren’t the right fit for their business. In addition, the ongoing cybersecurity skills shortage coupled with our rapidly increasingly connected digital ecosystem has exposed new cyber risks, while supply chain attacks and other multi-party incidents continue dominate the headlines.
RiskRecon Use Cases
Third-Party Portfolio Diagnostic and Prioritization
Supply Chain Monitoring and Visualization
Own Enterprise and Subsidiary Monitoring
Managing Cyber Risk Across the Extended Ecosystem
An organization’s internet surface area is often larger and more complex than it may seem, which makes things difficult when a third-party vendor wants to know more about an organization’s cybersecurity rating and performance. Research shows that choosing a partner with a poor security posture makes that organization 360 times more likely to be at risk of being exposed to security findings. This challenge is compounded for the 57% of organizations that have internet assets or hosts in other countries. Without a complete picture of their own risk surface, organizations are severely disadvantaged in the event of a data breach, and face losing both potential and existing business deals, vendors, or partners.
Cyber Risk Fuels Cybersecurity Spending in 2023
Catastrophic third-party breaches like the Solar Winds attack and Kaseya attack served as a wake-up call for anyone responsible for managing cyber risk. Despite the uncertain economic landscape, business leaders and risk executives know they can’t afford not to invest in third-party risk management. A study by the Cyentia Institute and RiskRecon, a Mastercard company, shows that a data breach affecting multiple parties causes 26X the financial damage of the worst single-party breach.
Cybersecurity spending in 2023 is expected to continue on its tremendous growth trajectory. According to Gartner, spending on information security and risk management products and services is forecast to grow 11.3% to reach more than $188.3 billion in 2023. However, factors fueling that record growth will shift as business leaders and risk executives prioritize managing cyber risk.
A Swiss Army Knife for Managing Cyber Risk
A facilities manager can spend lots of money on a fancy toolbox to fill with an assortment of tools they’ll never even use just to lug it around and still find themselves missing the tool they really need. It’s a relatable scenario for lots of risk professionals today who are saddled with far too many expensive cybersecurity tools and technologies that can’t collaborate and don’t serve a purpose.
With its sleek and compact design, the Jackknife can fit in your pocket and is more versatile than most tools and doesn’t compromise on quality or results. RiskRecon is like a Jackknife for cyber risk: one platform with multiple uses that’s easy to use and encourages collaboration across your extended ecosystem.
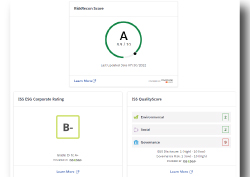
RiskRecon continuously monitors the cybersecurity risk of 13 million+ companies across the most highly regulated industries, including financial services and healthcare. RiskRecon provides organizations with the most comprehensive view of their risk surface in real-time through automated, continuous cyber risk monitoring. With RiskRecon, cybersecurity and risk professionals can better manage their digital ecosystem, detect risks, and understand how businesses view their organization’s cyber hygiene.
One Platform, Many Uses
Below are key use cases driving the success for RiskRecon customers to help you better understand how we can help you achieve better risk outcomes for your enterprise and your supply chain.
Third-Party Portfolio Diagnostic and Prioritization – Most organizations entrust third parties with their most sensitive data and operational functions, but these additional business relationships increase the scale and complexity of an organization’s extended risk surface. Research reveals that 35% of organizations have externally hosted assets with high or critical issues/findings.
To help safeguard your digital ecosystem from third-party risk, cybersecurity and risk professionals need simple, real-time visibility of third-party partners’ cyber performance. RiskRecon discovers and monitors third-party risk and quickly acts on the threats that pose the most damage to the organization. Key features include:
- Executive Summary Report -- Obtain high-level snapshots and continuous view reporting of supply chain vendors that show portfolio overall rating, performance breakdown by criticality, recent breach events, and other important information.
- Risk Priority Matrix (Risk Prioritization) -- Automatically view prioritized (high-medium – low) third-party findings based on issue severity and value at risk, including the magnitude of impact if the system is compromised.
- Vendor Action Plans -- Provide third parties with risk-prioritized action plans that guide them in addressing tactical and systemic risk.
Supply Chain Monitoring and Visualization -- Catastrophic multi-party breach events show that cyber risk can originate in supply chain layers beyond your immediate third parties. In fact, 65% of an organization's assets sit on infrastructure owned by an external entity or supply chain vendor. However, cybersecurity analysts are less likely to know who those supply chain vendors are, let alone receive rights to audit or risk assess them directly – leaving your organization exposed to a potential backdoor supply chain cyberattack.
With RiskRecon extend your visibility and gain insight beyond third parties, without additional approvals or permissions. Key benefits:
-
- Further reduce overall security risk through fourth-party monitoring.
- Minimize the time and effort required to research and understand extended supply chain risk.
- Improve visibility and reporting of security risk throughout the organization.
Own Enterprise and Subsidiary Monitoring -- An organization’s internet surface area is often larger and more complex than it may seem, which makes things difficult when a third-party vendor wants to know more about that organization’s cybersecurity rating and performance. Without a complete picture of their own risk surface, organizations are severely disadvantaged in the event of a data breach, and face losing both potential and existing business deals, vendors, or partners.
With RiskRecon you can better manage your digital ecosystem, detect risks, and understand how businesses view your cyber hygiene. Key features include:
- Executive Summary Report -- Obtain high-level snapshots of potential vendors.
- IT Profile -- Automatically discover, filter, and sort through IT assets within your owned ecosystem to detect risks.
- Data Search -- Explore, sort, and filter through asset and host information.
Situational Awareness -- Large-scale vulnerabilities and attacks like SolarWinds, Kaseya and Log4J can quickly wreak havoc within an organization’s digital supply chain. The median cost of extreme multi-party data breaches is $90 million, compared to $200,000 for a typical breach incident. When faced with such catastrophic potential risk, being able to quickly identify and act on impending exposure is crucial. However, without complete visibility into your third and fourth parties, it’s nearly impossible to triage the risk and protect your organization.
With RiskRecon quickly detect, isolate, and act on critical vulnerabilities before they can be exploited. Key features include:
- Situational Awareness Module -- View and download reports analyzing your IT landscape both inside and outside your firewall. IT Profile
- Asset Inventory -- Automatically discover, filter, and sort through IT assets within your owned ecosystem to detect risks.
- Supply Chain Module -- Proactively monitor your organization’s greater supply chain posture through instant discovery and visualization of fourth parties without additional research or permissions.
Vendor Onboarding -- Only 14% of organizations are confident that vendor security postures meet their requirements, yet 81% of organizations say they rarely require vendors to remediate findings. A nonexistent or unorganized third-party onboarding process can immediately establish a poor working relationship with vendors, decreasing their engagement and leading to reduced cyber risk visibility. This friction can decrease a vendor’s willingness to adhere to contractual performance standards and support the remediation of cyber risk.
RiskRecon works to streamline your onboarding process, increase third-party visibility and improve vendor engagement. Key features include:
- Executive Summary Report -- Obtain high-level snapshots and continuous view reporting of supply chain vendors.
- Trend Reporting -- Discover how well growth targets consistently trend including over time and past three years.
- Vendor Action Plans -- Provide third parties with risk-prioritized action plans that guide them in addressing tactical and systemic risk. Track remediation processes directly within the RiskRecon vendor portal, at no cost and without time restrictions to your third-party vendors.
Request for Proposal (RFP) -- Selecting the right vendor for your organization is critical but conducting full manual assessments on multiple vendors before a selection is even made can be time-consuming. This is particularly challenging for 87% of programs who report having inadequate staffing. While manual assessments do provide an understanding of the investments a vendor has made in people, process and technology to achieve good risk outcomes, they can’t show you how well a vendor implements and operates its risk management program.
RiskRecon automates your vendor assessment process, which results in faster, more confident vendor selections. Key features include:
- Executive Summary Report -- Obtain high-level snapshots and continuous view reporting of supply chain vendors.
- Benchmarking -- Compare and contrast potential vendors with side-by-side views of overall performance and domain performance.
- Trend Reporting -- Discover how well growth targets consistently trend over time and the past three years.
Mergers & Acquisitions (M&A) – Mergers and acquisitions (M&A) can take months or even years to materialize due to lengthy due diligence processes – and that’s before factoring in today’s heightened concerns around cybersecurity. The average time taken to close an M&A deal has risen 30% in the last decade.
Having to internally orchestrate a manual assessment with respect to confidentiality only increases the time required – and manual assessments still aren’t fully equipped to tell how well an organization implements its cyber risk management program.
RiskRecon assess growth targets at the speed of business with greater clarity, insight, and confidentiality. Key features include:
- Multi-Portal Logins -- Monitor M&A targets confidentially by designating and assigning user permissions to limit or restrict data viewing.
- Executive Summary Reports -- Obtain high-level snapshots and continuous view reporting of supply chain vendors that show portfolio overall rating and recent breach events, among other important information.
- Trend Reporting -- Discover how well growth targets consistently trend over time and for the past three years.
Vendor Due Diligence -- A lot can happen between vendor assessments since they only show a specific moment in time, especially when you consider that 84% of organizations host critical and/or sensitive assets with third parties. Data breaches may occur, and critical vulnerabilities in vendor environments could end up going unaddressed. Without live visibility into your vendor ecosystem, your organization loses precious time to act on cyber threats – potentially compromising your dependent operations and data.
RiskRecon enables you to view vendor cyber performance in real-time to better manage and reduce third-party risk. Key features include:
- Executive Summary Report -- Obtain high-level snapshots and continuous view reporting of supply chain vendors that show portfolio overall rating, performance distribution summary, and performance breakdown by criticality, among other critical information.
- Benchmarking -- Compare and contrast potential vendors with side-by-side views of overall performance and domain performance.
- Trend Reporting -- Discover how well growth targets consistently trend including: over time, overall rating, critical issues, past three years, and breach event occurrence and exposure.
Trying to patch gaps in your cybersecurity posture with new tools is futile. Stop building your stack and start streamlining with RiskRecon. Kick off the New Year right and sign up for a 30-day trial of the RiskRecon platform to get the cybersecurity risk ratings of up to 50 vendors in your portfolio, get started here: riskrecon.com/know-your-portfolio.