Where do ripple events stem from? This question may well be top of mind now more than ever, as these types of events become commonplace. That is why we made it a point to learn as much as we could about how these incidents, or their impacts, spread from the initial victim organization to downstream parties.
While reviewing the findings in this article, it is important to remember that the nature of what we call “ripples” varies substantially among incidents. For some events, ripples may come in the form of threat actors that move from the systems of one organization into those of another. For others, ripple effects may take the form of operational or financial impacts to partners and customers. This concept of ripples is probably best exemplified by the categories we derived from studying these cyber tsunami events, so let’s jump right into the figure below.
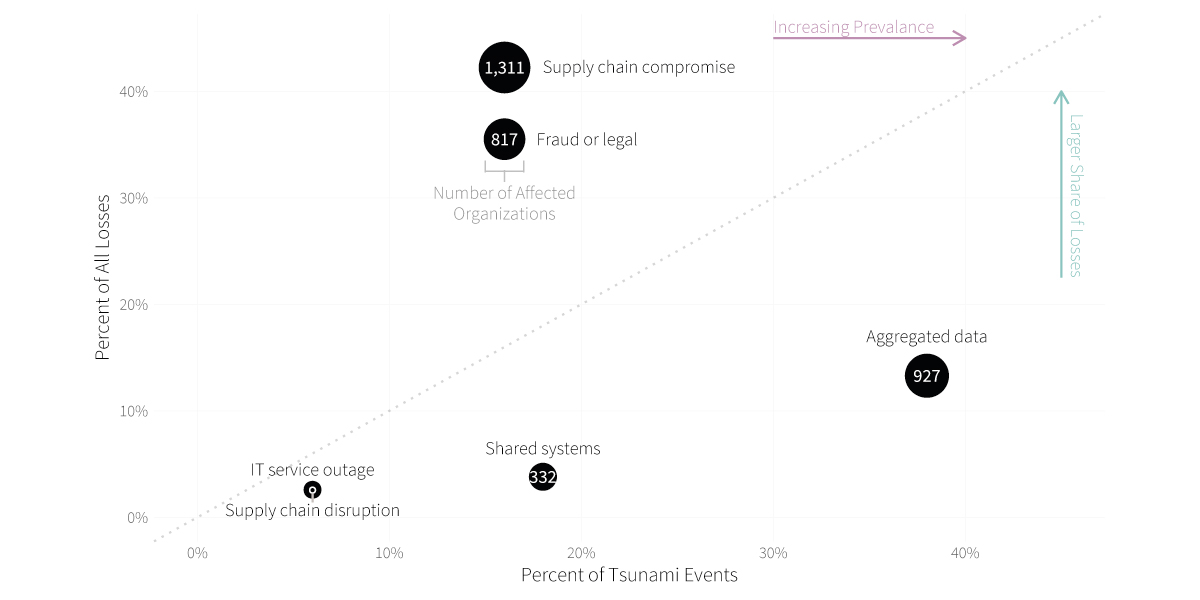
The most common form of ripple propagation that we observed is the compromise of multi-party data aggregated by the initial victim organization. The systems of downstream parties are not breached in this scenario, but those organizations nevertheless suffer various consequences as owners of the disclosed data. This is doubly unfortunate for the original data owners because they have little ability to protect the data once it has been shared. The best protection is to choose data custodians wisely and check regularly to ensure that they uphold their end of the bargain.
The ripple vector of shared systems comes next on the list in terms of frequency. This scenario does involve the compromise of systems owned or used by downstream parties. In some cases, all organizations share centralized applications such that a breach of one escalates to become a breach of many. But in others, interconnectivity and trusted access enable propagation to additional systems and organizations. The lesson here is that trusted systems easily become busted systems without proper 3rd party access controls.
Ripples taking the form of supply chain compromises led to the biggest share of recorded financial losses ($7.4 billion) and the largest number of secondary victim firms. This seemed rather important, so we leveraged sub-techniques defined by ATT&CK to dig deeper into this ripple propagation vector. This breakdown can be found in the table below.
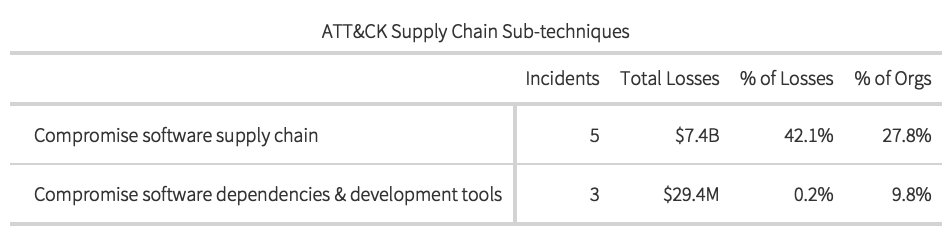
We came across no examples involving compromised hardware components moving through the supply chain prior to receipt by the end customer. Of the eight supply chain attacks we identified, five targeted software distribution mechanisms and three exploited third-party or open-source software dependencies. Nearly all losses were associated with the former, and it was this sub-technique that was leveraged in the recent high-profile breaches of SolarWinds and Kaseya. The need to distribute and update code as well as leverage the benefits of third-party dependencies is fundamental to modern software development practices. Cyber adversaries, of course, are well aware of this, meaning this trend is likely to get worse before it gets better.
While on the topic of supply chains, we’ll go ahead and mention ripples that take the form of disruptions flowing downstream from the central firm. The key difference here is that no hardware or software distribution channels were compromised. Instead, think of scenarios where an incident hampers a firm’s ability to deliver goods and services to its partners and customers.
Those organizations will experience impacts and losses because of delays or disruptions. The other big-ticket item among ripple vectors is fraudulent activity or legal action. All of these stem from large data breach events in which impacted parties sought compensation for damages incurred. As Figure 8 makes plain, these damages can be quite hefty. Ripples of this kind can propagate more slowly, sometimes taking years to fully manifest.
Last, but not least, IT service outages made our set of ripple vectors. Of them all, this is the quickest and most direct method of propagation. As soon as the central organization (typically a hosting or SaaS provider) experienced the outage, so too did all parties relying on those services.







