In our latest analysis, we thoroughly explored a treasure trove of nearly 900 ripple events from the past, with the goal of unraveling the prevailing techniques employed by MITRE ATT&CK. Our ultimate aim is to gain a profound understanding of how these ripples emerge and propagate, ensuring that your organization remains unharmed in their aftermath.
Technique Co-Occurrence and Flow
There is one last concept we’d like to explore before concluding this report. Thus far, we have treated techniques as standalone actions. This approach is certainly useful for prioritizing defenses, but adversaries in real cyber attacks utilize a combination of TTPs in various, frequently recurring sequences – which is why tools such as ATT&CK Flow have been developed.
Using a sunburst chart, we’ll begin with the concept of technique co-occurrence within events. This chart is even more interconnected than the previous one, so attempting to follow all the lines could be overwhelming. Nonetheless, it is essential to observe the multiple paths within and between the colored sections, which represent initial access (blue), post-compromise (orange), and exfiltration/ impact (red) techniques.
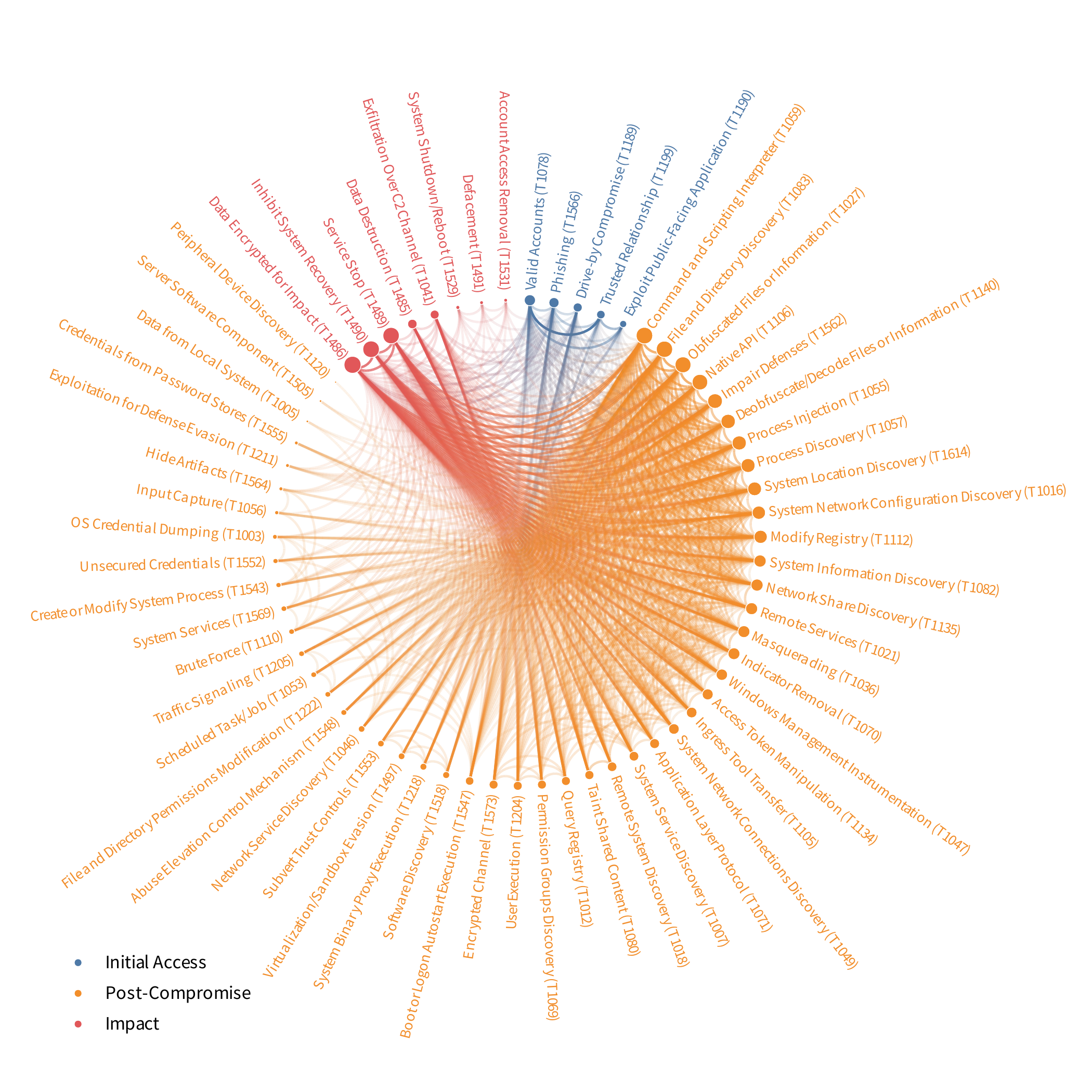
Co-occurence of ATT&CK techniques identified in ripple events
The frequent co-occurrence within initial access techniques, such as valid accounts (T1078) and Trusted Relationship (T1199), reflects the unique nature of ripple events. Multiple “initial” access points emerge as the incident spreads among victims.
The myriad paths among post-compromise techniques reveal the “Swiss Army knife” nature of these incidents. Once inside the network (or supply chain), adversaries leverage whatever tools and methods move them toward their objective. Nevertheless, mitigating even one of these techniques — Command and Scripting Interpreter (T1059), for example — could still significantly disrupt the adversary’s progression.
The connections between different tactic sets hint at technique combinations or flows that adversaries use to achieve their goals. If they always used the same sequence, there would be fewer, very prominent paths. The fact that we see more of a web-like structure suggests that adversaries do not follow a fixed script.
As an exercise in exploring inter-tactic flows, we mapped each of the top four initial access techniques to the post-compromise techniques most often observed following them. To simplify the tracking of these flows, we created the Sankey diagram, shown in the chart below. Essentially, this diagram addresses the question, “After gaining access via a particular technique, what actions do adversaries tend to do after that?”
Overall, the message here is not one of “when attackers do x, they only do y.” Some post- compromise techniques, such as those in the top half of the table, are versatile and accessible from a number of initial access techniques. Other post- compromise techniques are more clearly associated with specific initial access techniques, such as T1078 (Valid Accounts) or T1566 (Phishing).
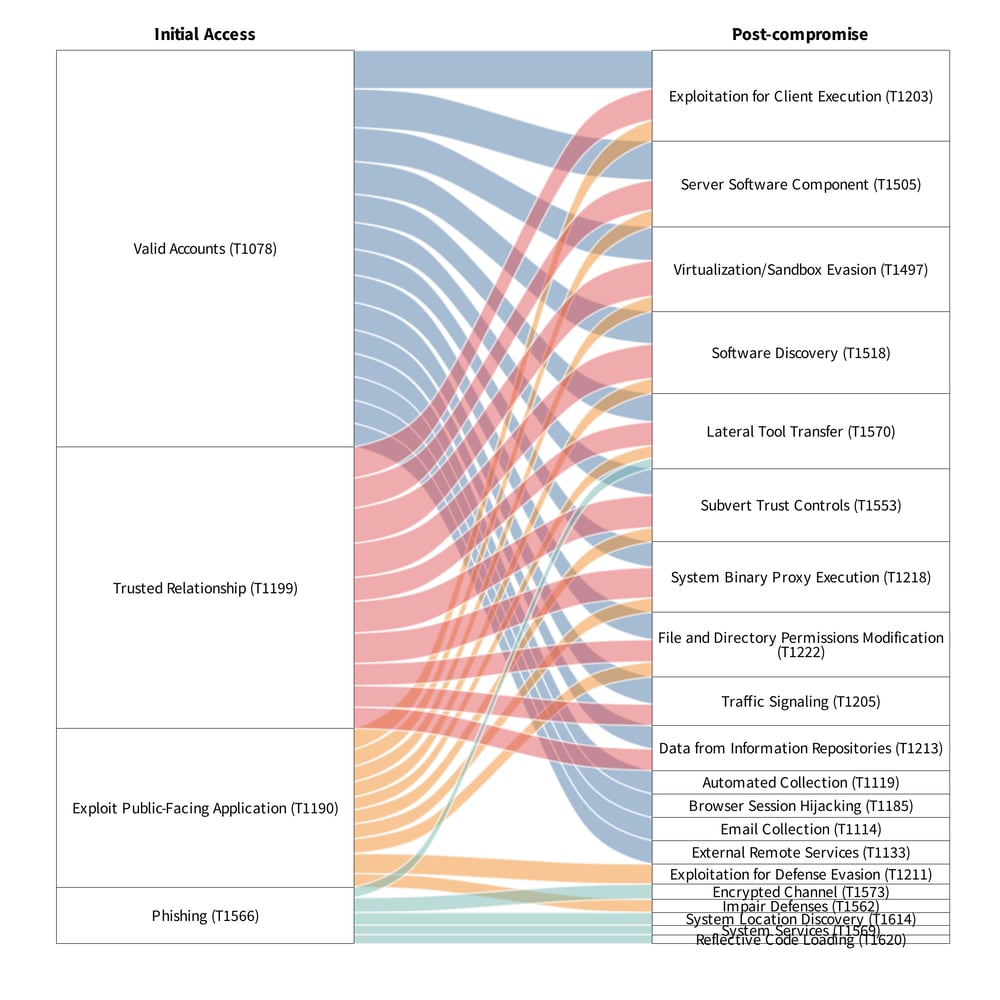 Flow between initial access and post-compromise ATT&CK techniques in ripple events
Flow between initial access and post-compromise ATT&CK techniques in ripple events
What can we make of all these findings?
Firstly, the financial ramifications of such incidents are notably higher, approximately seven times more costly, compared to single-party events. Among the various types of ripple events, system intrusions emerge as the most precarious, exhibiting both high frequency and substantial financial losses, impacting a multitude of third parties. The predominant methods of initial access involve targeting valid user accounts and leveraging trusted third-party relationships, underscoring the importance of robust authentication measures and diligent third- party management. Notably, exploiting public- facing applications contributes significantly to the financial toll of multi-party security incidents.
Surprisingly, incidents stemming from insider mistakes are not only twice as prevalent as those resulting from insider malice, but they are also exponentially more expensive, being 800 times costlier. Lastly, the involvement of malicious code injection and obfuscation is undeniably linked to reported financial losses, affecting 100% of cases, and impacting a substantial 87% of third parties in the context of multi-party security incidents. These findings emphasize the critical need for comprehensive security measures, vigilance in managing third-party relationships, and proactive strategies to mitigate the potential cascading effects of multi-party security breaches.
Get your hands on our comprehensive report to gain a deep understanding of the potential threats lurking in your digital supply chain. Through meticulous analysis of nearly 900 ripple events, we have successfully uncovered the intricate techniques employed by MITRE ATT&CK. Equipped with this invaluable knowledge, you can fortify your organization against any potential harm and establish a robust and impervious supply chain.








