In our latest analysis, we looked into a treasure trove of nearly 900 ripple events from the past, aiming to unravel the dominant techniques employed by MITRE ATT&CK. Our ultimate goal is to gain a profound understanding of how these ripples come to life and spread, ensuring that your organization remains unharmed in their wake.
In this blog, we use MITRE ATT&CK to dive deeper into ripple event mechanics. ATT&CK is rapidly becoming the common language for adversary tactics and techniques used across the cybersecurity industry. A major benefit of ATT&CK is that it enables readers to easily find definitions and examples of each referenced technique and to explore a wealth of information on associated threat groups, malware, mitigations, attack simulations, etc.
Unfortunately, public disclosures or media coverage of security incidents rarely provide a detailed list of the involved ATT&CK techniques. Evidence collected via a digital forensics investigation is generally needed for that purpose. However, using a combination of analytical techniques, we validated the ATT&CK techniques for 23% of the primary incidents in our dataset.
While this percentage might not seem like much, keep in mind that a good chunk of these events fall outside the scope of ATT&CK by their nature (e.g., insider, physical, and privacy-related events). Furthermore, those incidents for which we were able to identify ATT&CK TTPs represent a higher proportion of recorded financial losses (35%) and impacted third parties (48% of the total number of affected companies). This suggests that we do, at least, cover a majority of the more important incidents.
We’ve organized identified techniques into three key stages of an incident: initial access, post- compromise (execution through lateral movement), and exfiltration and impact. In this section, we present the most frequently observed and impactful techniques for each of these stages.
Initial Access Techniques
Attackers use initial access techniques to gain entry to penetrate their target environment. From phishing to exploiting applications and supply chains, you’re likely familiar with most of these techniques. Understanding initial access trends is crucial for identifying the best mitigations to ward off adversaries before they become deeply embedded in networks and systems.
Recently, zero trust has become a huge topic in the cybersecurity industry of late, and looking at Figure 5, it’s hard to argue against the core thesis of this strategy. Three of the four most frequent initial access techniques target trust—trusted accounts or credentials, trusted relationships with third parties, and trusting users who fall for phishing schemes. These techniques also rank in the top four for financial losses.
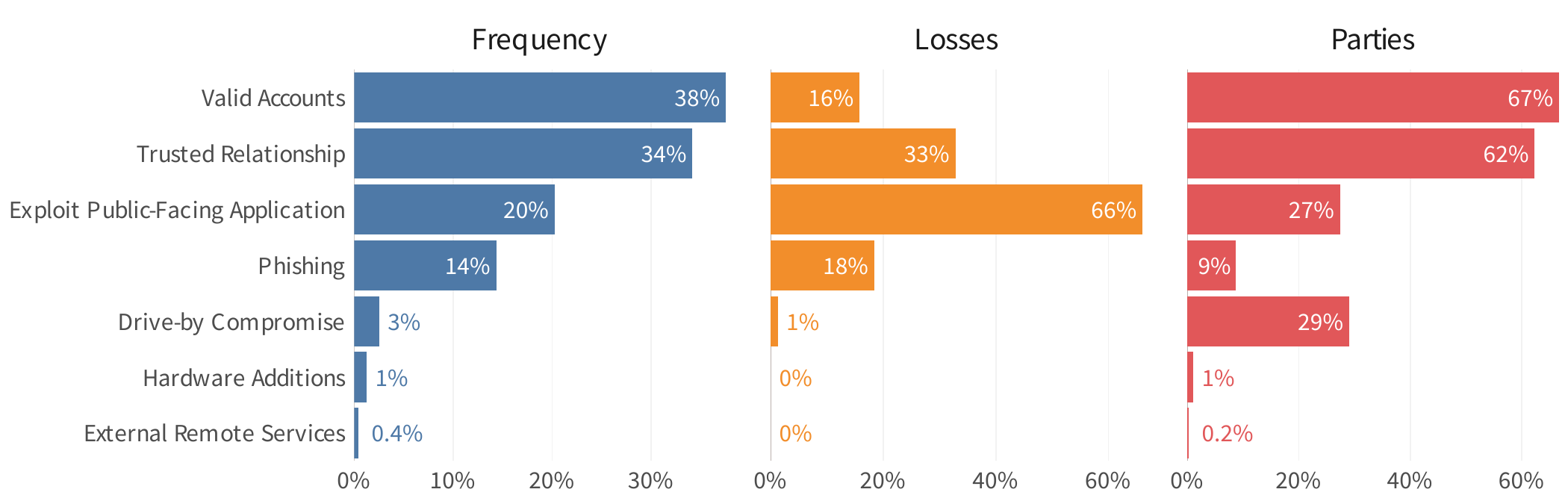
Key stats associated with the initial access techniques used in ripple events
The subversion of valid user accounts and trusted third-party relationships contribute to over 60% of downstream parties impacted by ripple events; and it’s easy to see why. Once an attacker gains the privileges intended for trusted users or third parties, they’re on the fast track to spreading across the network and supply chain. If you’re curious about the underlying risk factors enabling this spread, our Balancing Third-Party Risk report offers useful insight.
The exploitation of web applications is another major initial access vector for ripple events. Not only does this technique rank third on the frequency scale, it contributes to nearly two-thirds of all financial losses! This validates the critical importance of continual assessments to ensure that internet-facing devices are properly secured.
Top Initial Access Mitigation Strategies
As mentioned above, many of the most common and impactful initial access techniques target trusted accounts. Therefore, it’s fitting that several of the top mitigation methods illustrated in Figure 6 focus on securing those accounts and credentials (e.g., M1018, M1026, M1027, and M1032).
Other effective strategies include segmentation (M1030), limiting access to network resources (M1035), and isolating or sandboxing applications (M1048). These approaches can effectively restrict adversaries who manage to exploit accounts or applications.
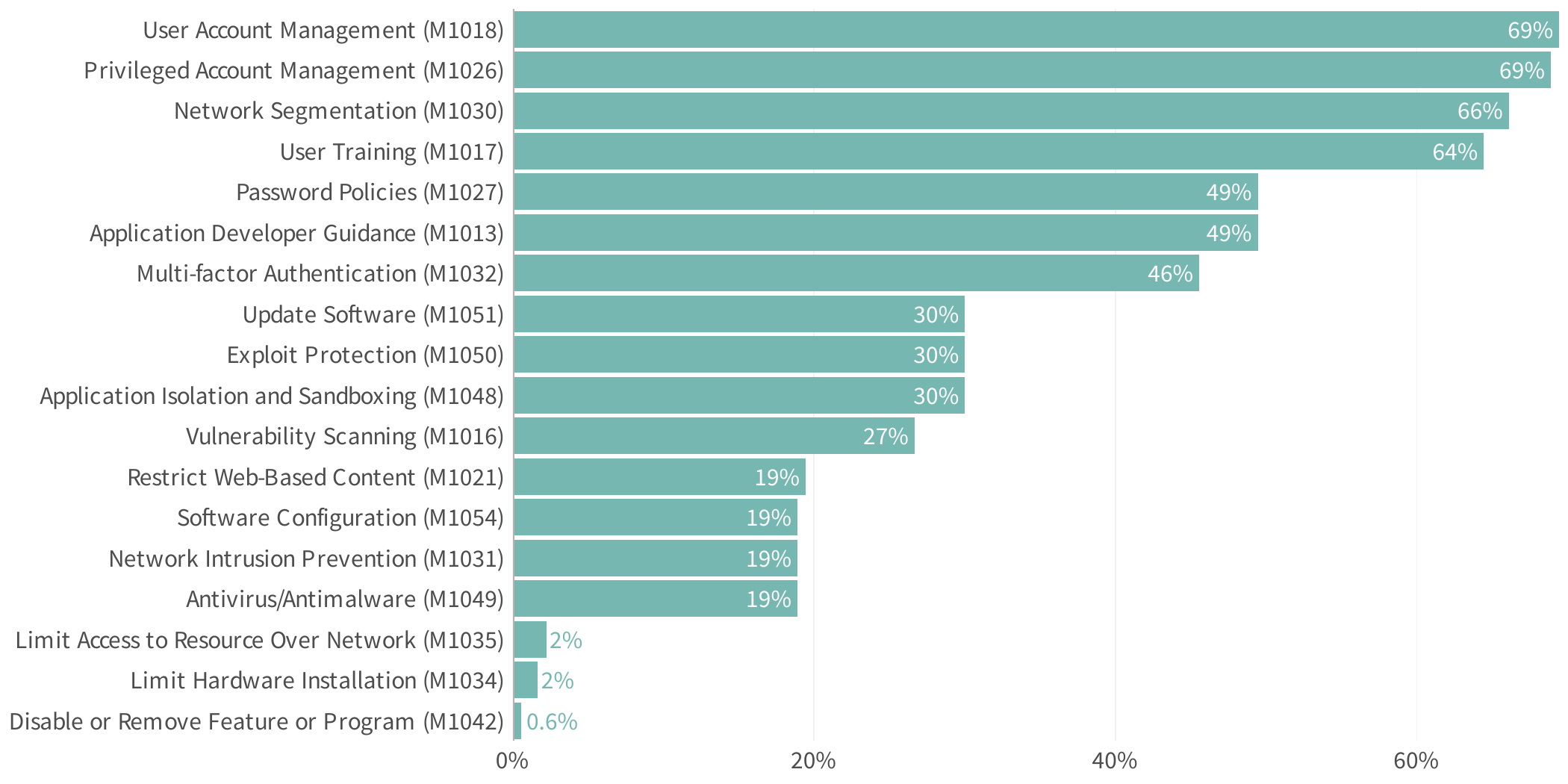
Recommended Mitigations for the most common initial access techniques
Security hygiene emerges as a third theme woven through the recommended mitigations for initial access techniques. Implementing measures such as updating software (M1051), avoiding easy exploitation (M1050), conducting vulnerability scans (M1016), and restricting unnecessary web content and services (M1021) all reduce the likelihood of your organization falling prey to opportunistic attackers.
Download our report for valuable insights into the risks of your digital supply chain, empowering informed decision-making.








