In our most recent analysis, we delved into a wealth of almost 900 ripple events from the past, with the aim of uncovering the prevailing techniques employed by MITRE ATT&CK. Our ultimate objective is to acquire a comprehensive understanding of how these ripples materialize and propagate, safeguarding your organization from any harm they may cause.
In the next blog, we look at what attackers do once they have gained an initial foothold in the victim’s central environment. These post-compromise techniques include all the illicit activities attackers do to maintain a presence, escalate privileges, spread across the internal network (and to connected third parties), evade security defenses, establish command and control channels, etc.
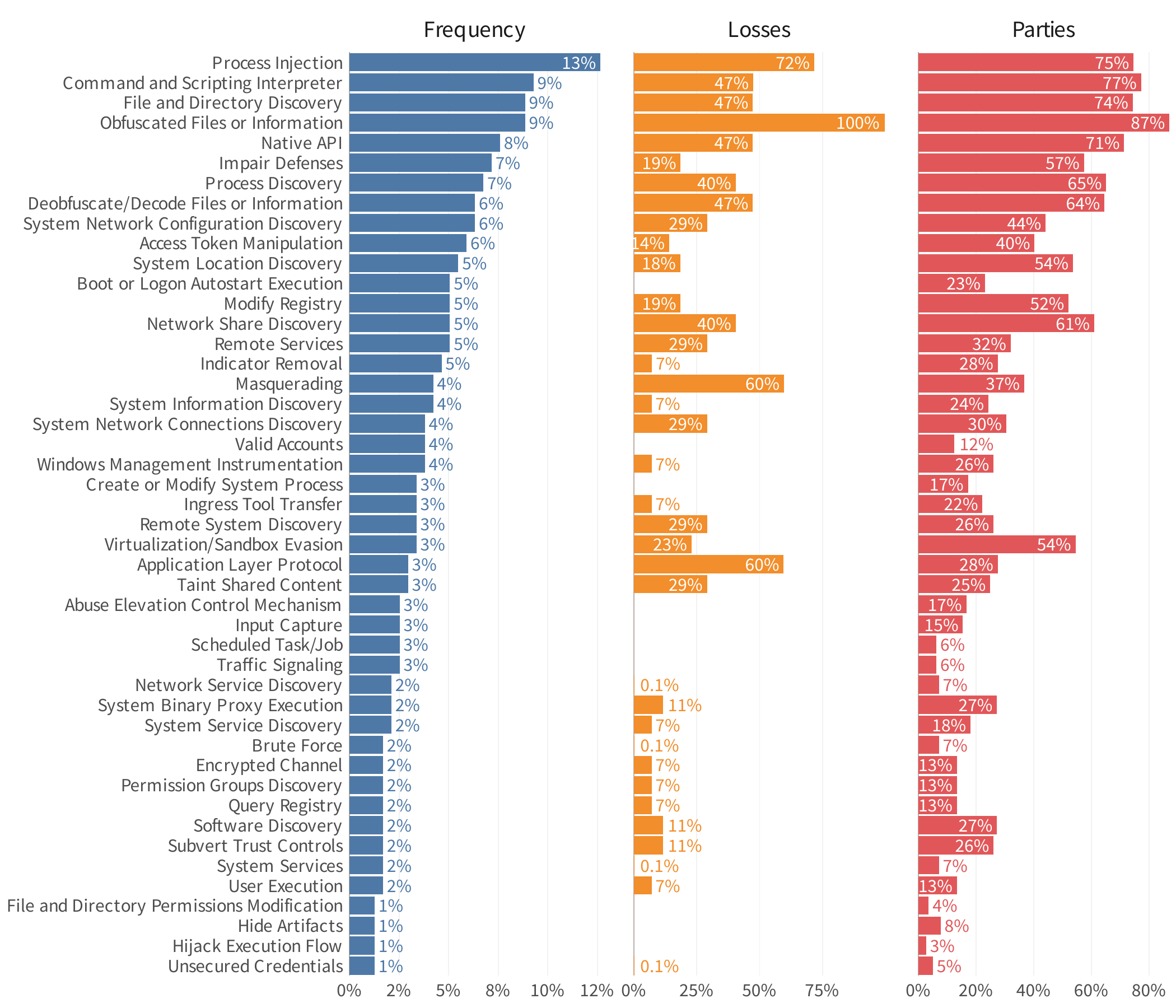
The figure below showcases all identified post-compromise techniques that contributed to at least 1% of ripple events. It’s rather overwhelming—but that’s actually a big part of the message we intend to convey. Attackers have an extensive toolkit at their disposal and use whatever is necessary to get the job done. Because the list is lengthy, we will highlight a few that stand out and leave the rest for your review at your leisure.
Process injection (T1055) is noteworthy, ranking #1 in frequency, second in financial losses, and third in affected downstream parties.
Adversaries use this technique to introduce or execute malicious code within legitimate applications or services.
Speaking of introducing code, obfuscated files or information (T1027) constitutes another favored post-compromise technique. Attackers typically employ this method to deliver payloads without setting off alarms. Astonishingly, this tactic involved 100% of known financial losses and 87% of impacted parties in multi-party security incidents.
Key stats associated with top post-compromise techniques used in ripple events
Masquerading (T1036) and application layer protocol (T1071) are even less common, but their association with over half of the financial losses warrants mention. The former technique involves disguising malicious activity or tools as innocent, and the latter is often used to blend in with legitimate traffic to evade detection.
Top Post-Compromise Mitigations
Given the extensive list of post-compromise techniques, it follows logically that the list of potential mitigations would also be considerable. The chart below doesn’t disappoint in making this point.
Looking more closely, we see many of the same mitigation techniques also effectively thwart initial access attempts. That’s good news, as it suggests things like managing accounts, restricting permissions, and hardening systems will pay double dividends for prevention and limiting the extent of the damage.
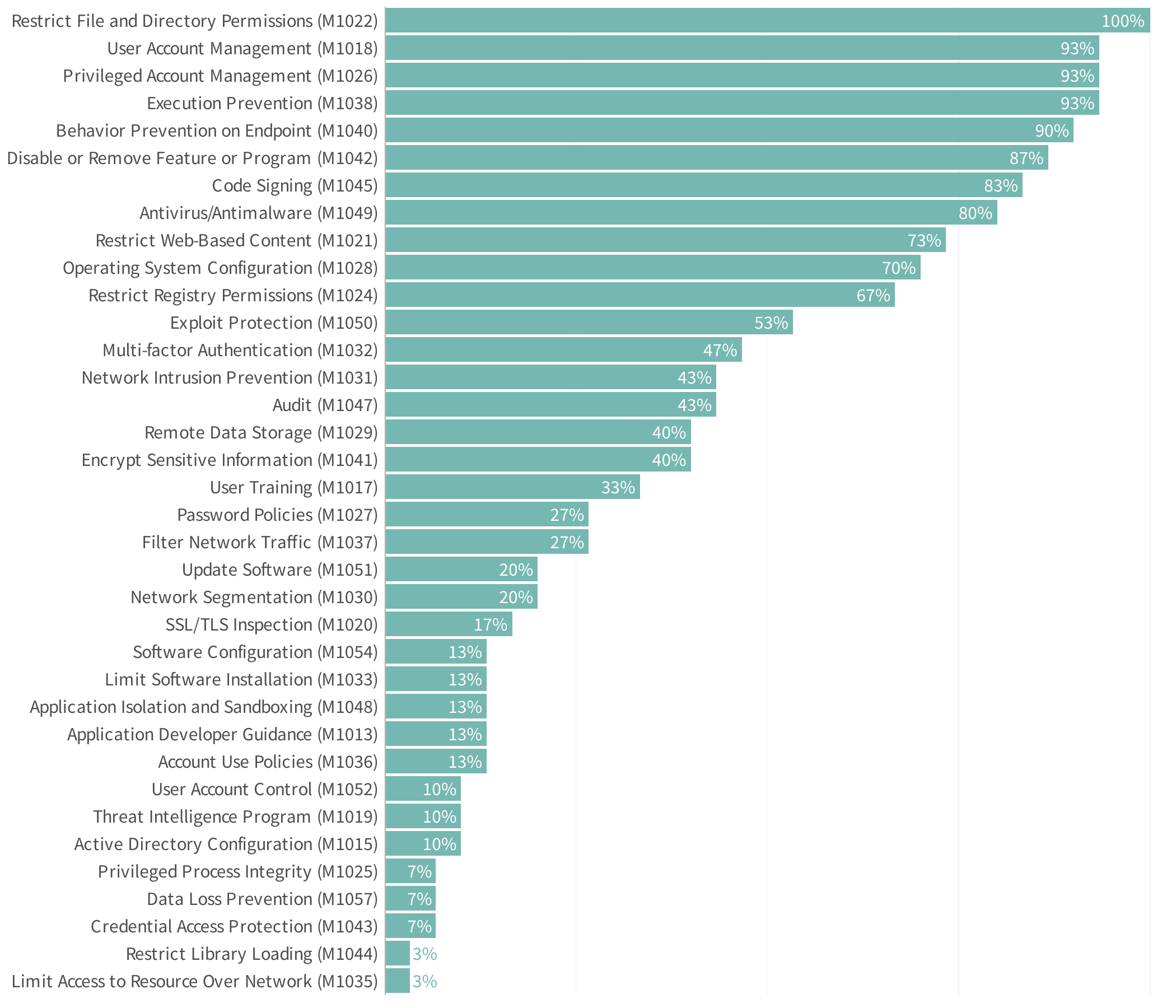
In line with the injection and obfuscation techniques referenced earlier, policies and controls that prevent unpermitted code introduction and changes also prove to be defensive assets in this phase of a security event.
We encourage you to access our latest report and delve into our comprehensive study. We believe it will provide invaluable insights into the critical importance of understanding the risks associated with your organization's digital supply chain. Download the report now and gain a deeper understanding of how to safeguard your organization from potential harm.








