In almost every way imaginable, we live in a hyperconnected world. This connectivity has brought many benefits to modern business models, but it has also introduced myriad challenges and risks. If you take the time to decompose even the simplest of business transactions, you’ll find in the mix a surprising number of parties from technical components supporting the transaction to the completed delivery of products to the customer. But what happens to all these parties when something goes wrong?
That is ultimately the question that this study seeks to explore. We identified 50 of the largest multi-party cyber incidents over the past several years in an effort to understand their causes and consequences from beginning to end. If you are familiar with our other research in the Information Risk Insights Study (IRIS) series, Tsunami draws from the same rigorous methodology. We started with a huge dataset of cyber loss events, identified those that involved multiple organizations, and then researched each event to understand who was behind it, what happened, how the after-effects propagated through the supply chain and the financial losses for all parties involved.
How was the data collected?
Like its predecessors in the IRIS series, this study leverages Advisenʼs Cyber Loss Data, containing nearly 100,000 cyber events collected from publicly verifiable sources. Three features make this dataset uniquely suitable for this research: 1) it has comprehensive coverage across a wide variety of incidents, 2) it links organizations that are involved in or impacted by a common incident, and 3) it tracks losses that were publicly disclosed in the wake of those events.
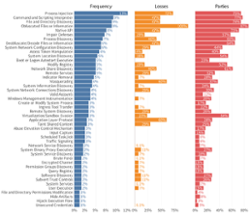
From Advisen’s Cyber Loss Data, we identified the 50 largest multi-party cyber incidents (see criteria in next section) and sought to collect hundreds of additional data points on those events. We followed the same data collection procedures used for the IRIS Xtreme, scouring public information sources to categorize incident types, identify the actors behind these events, record the techniques they employed, etc. Additionally, we gave special attention to discover the methods by which these incidents (or their effects) propagated from initial to secondary victim firms.
What’s a multi-party cyber incident?
Many cybersecurity incidents involve not only involve the primary organization but also generate secondary loss events that impact various other 3rd/4th/Nth parties. We refer to these multi-party incidents as “ripple events,” reflecting how their after-effects swell outward from the central victim to envelop others in their wake. Extending that metaphor, we’ve designated ripple events that propagate the furthest or cause the most damage as tsunamis. You’ll find a broad analysis of 900 multi-party cyber loss events in our joint report with RiskRecon titled Ripples Across the Risk Surface.
What constitutes a “tsunami” event?
We used several criteria to identify a subset of the largest ripple events (aka “tsunamis”):
- The largest 30 multi-party events as measured by total reported financial losses.
- The largest 30 multi-party events as measured by the number of data records affected.
- The largest 30 multi-party events as measured by the number of firms involved.
Any multi-party cyber incident meeting any of these criteria was a candidate for inclusion, and we then selected the top 50 based on the combined totals as well as information availability. These 50 digital tsunamis form the corpus of the analysis that follows in this study.