In almost every way imaginable, we live in a hyperconnected world. This connectivity has brought many benefits to modern business models, but it has also introduced myriad challenges and risks. If you take the time to decompose even the simplest of business transactions, you’ll find in the mix a surprising number of parties from technical components supporting the transaction to the completed delivery of products to the customer. But what happens to all these parties when something goes wrong?
In almost every way imaginable, we live in a hyperconnected world. This connectivity has brought many benefits to modern business models, but it has also introduced myriad challenges and risks. If you take the time to decompose even the simplest of business transactions, you’ll find in the mix a surprising number of parties from technical components supporting the transaction to the completed delivery of products to the customer. But what happens to all these parties when something goes wrong?
That is ultimately the question that this study seeks to explore. We identified 50 of the largest multi-party cyber incidents over the past several years in an effort to understand their causes and consequences from beginning to end. If you are familiar with our other research in the Information Risk Insights Study (IRIS) series, Tsunami draws from the same rigorous methodology. We started with a huge dataset of cyber loss events, identified those that involved multiple organizations, and then researched each event to understand who was behind it, what happened, how the after-effects propagated through the supply chain and the financial losses for all parties involved.
In this report, we identified 50 of the largest multi-party cyber incidents over the past several years in an effort to understand their causes and consequences from beginning to end. The goal of our research was to understand who was behind the incident, what happened, how the after-effects propagated through the supply chain and the financial losses for all parties involved.
The study found many interesting insights, including:
-
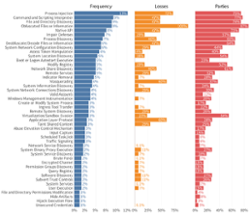
The median cost of these 50 extreme multi-party events stands at a whopping $90M. To put that in perspective, the typical incident runs a comparably measly $200K.
-
System intrusions were by far the most common type of incident, and they also impacted the largest number (57%) of downstream organizations.
-
Cracked and stolen credentials were the most common (50% of incidents) and costly (68% of losses) initial access technique.
Feel free to download the report here and dive into the findings.